团队赛MD5值:E5297609ACCD1C8DF7E6F56F8912E734
团队赛容器密码:mW7@B!tRpXz46Y9#KFUV^J2&NqoHqTpLCE%8rvGW(AX#1k@YL3$M5!bWY 9HLFq7UZR6^T!XoVmPK28J&CY9%6(Arz#tbU4oXYKLp7Wq^FV9H
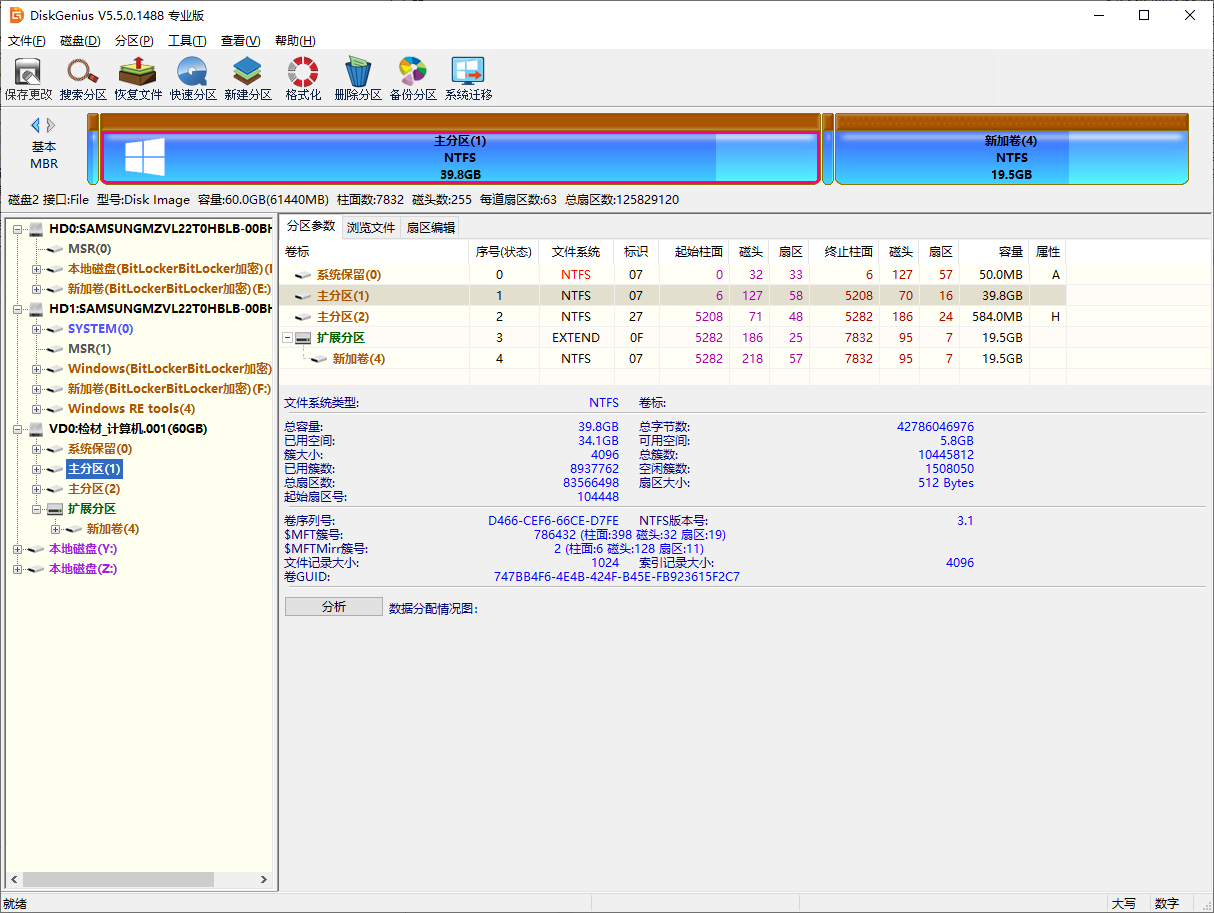
计算机取证 计算机取证-1 20 题目描述 计算机中曾挂载的bitlocker加密的分区的驱动器号为?(答案格式:大写字母,如C) (2.0分)
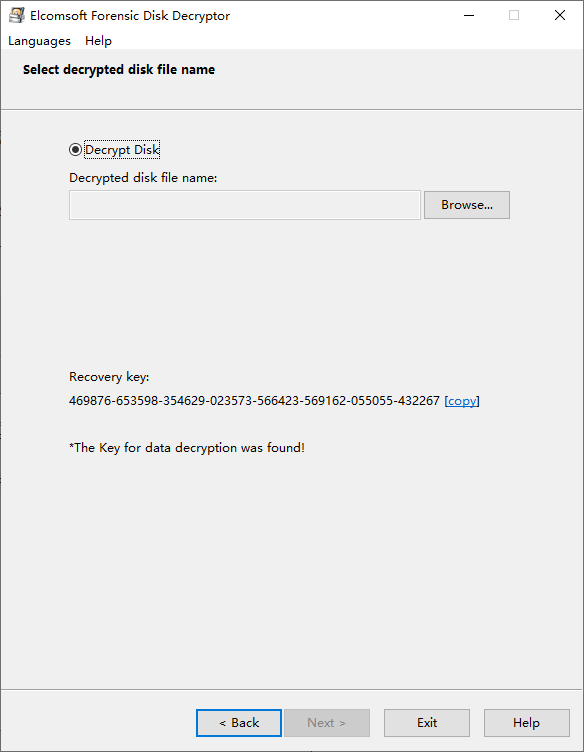
计算机取证-2 20 题目描述 分析计算机和内存检材,计算机中的Bitlocker加密分区的恢复密钥后6位为?(答案格式:123456) (4.0分)
得到
1 469876-653598-354629-023573-566423-569162-055055-432267
计算机取证-3 20 题目描述 计算机中通过向日葵接收的最后一个文件名称为?(答案格式:需带后缀名,如Abc.doc) (4.0分)
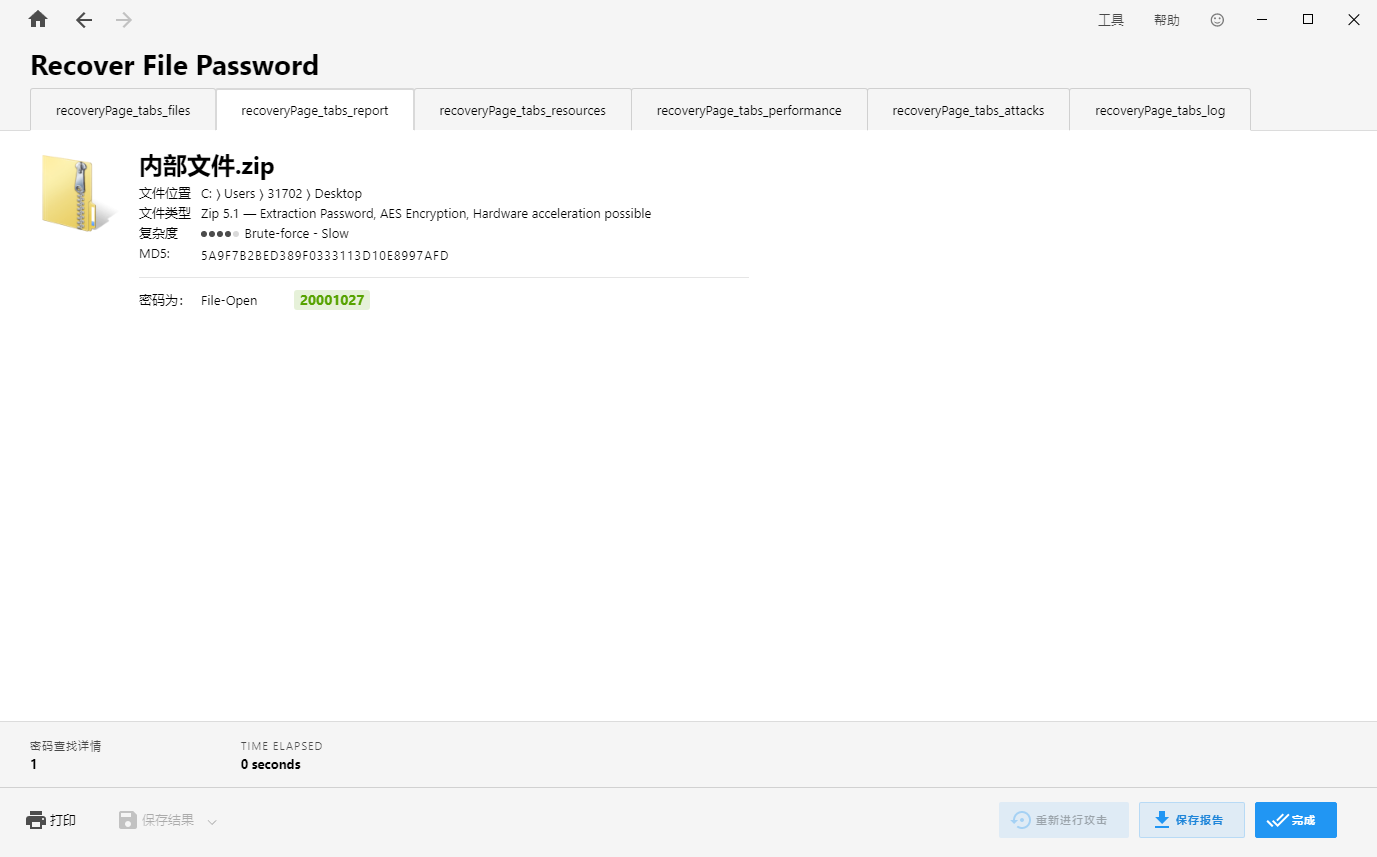
计算机取证-4 20 题目描述 计算机中加密容器8df84968a5b8c4d072c4daa4fd02cb19的解密密码为? (2.0分)
在同一文件夹下发现重要文件
010打开发现密码,比赛的时候暴搜密码出的
挂载后
计算机取证-5 20 题目描述 接上题,计算机中曾挂载的该加密容器分区中最后访问的文件,其文件名为?(答案格式:需带后缀名,如Abc.doc) (2.0分)
对应时间线和根据文件名判断Q盘
1 d7ed12489b9f8b521db78d121badbe83.jpg
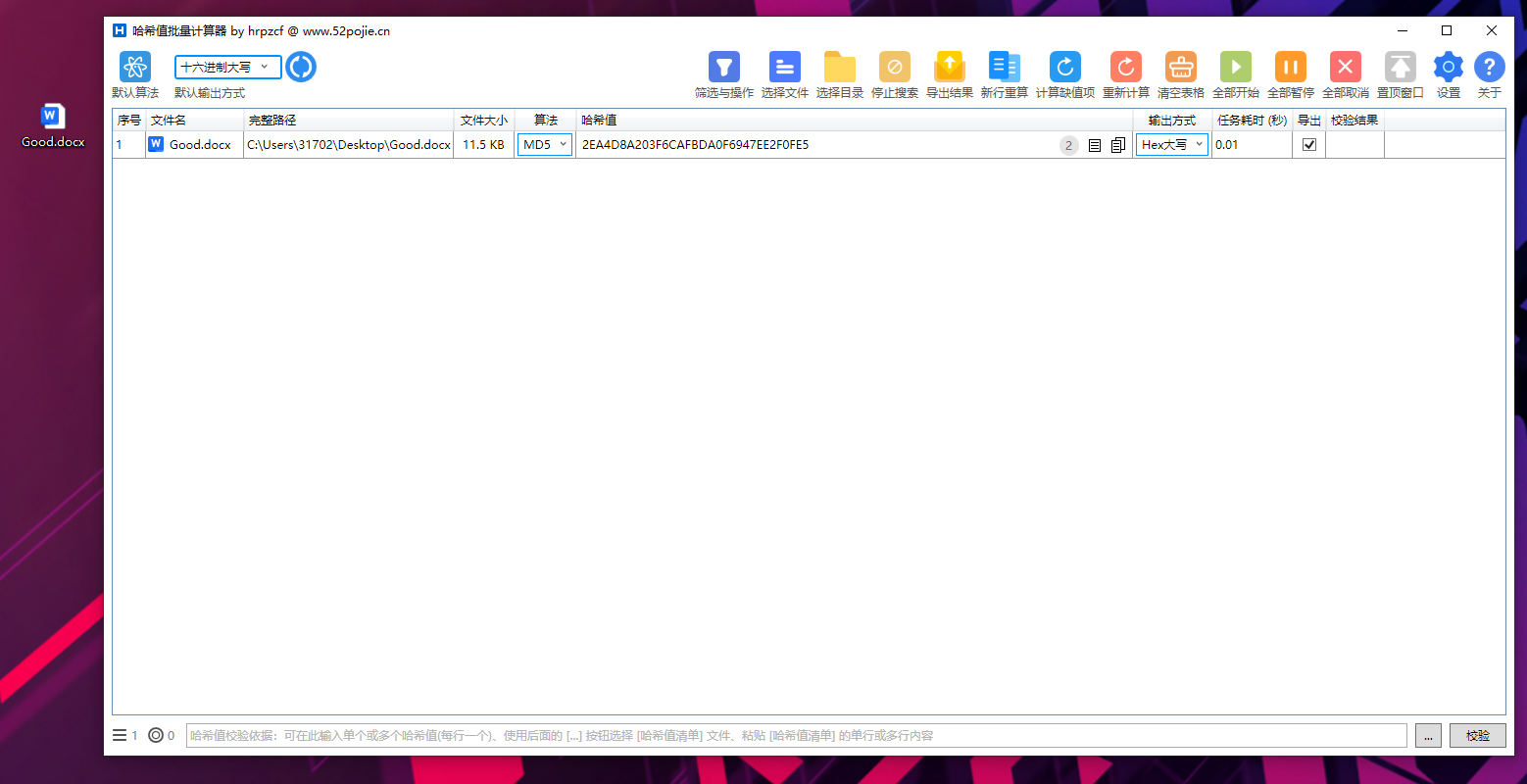
计算机取证-6 20 题目描述 请找到计算机中MD5值为2EA4D8A203F6CAFBDA0F6947EE2F0FE5的文件,写出其文件内容;(答案格式:需与实际一致,且涉及符号的部分半角全角需与实际一致) (4.0分)
右键分区-递归浏览-磁盘快照-计算哈希
但是这种方式没法计算EFS加密的文件-以后比赛多个心眼
对于文件内容需要将EFS解开
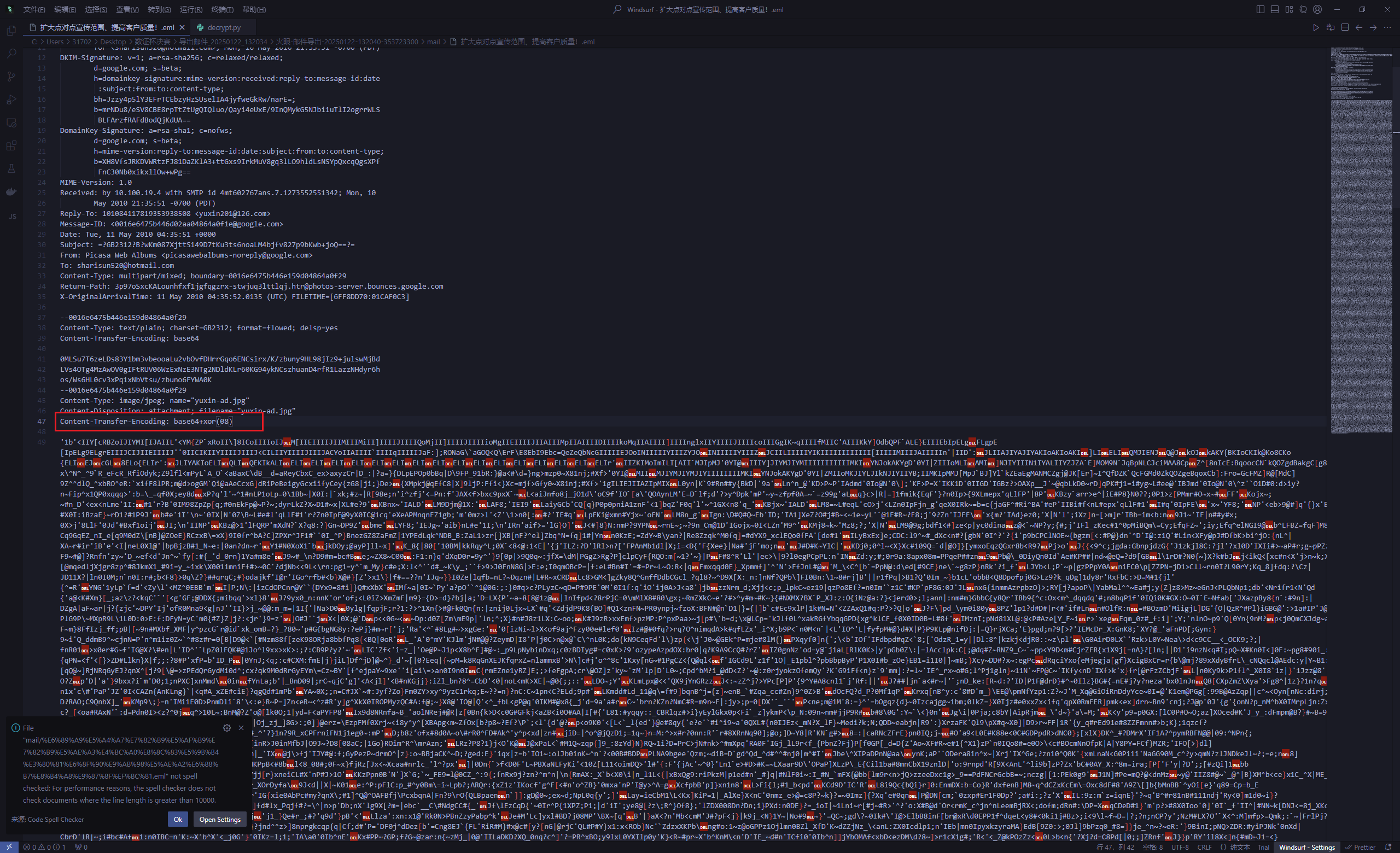
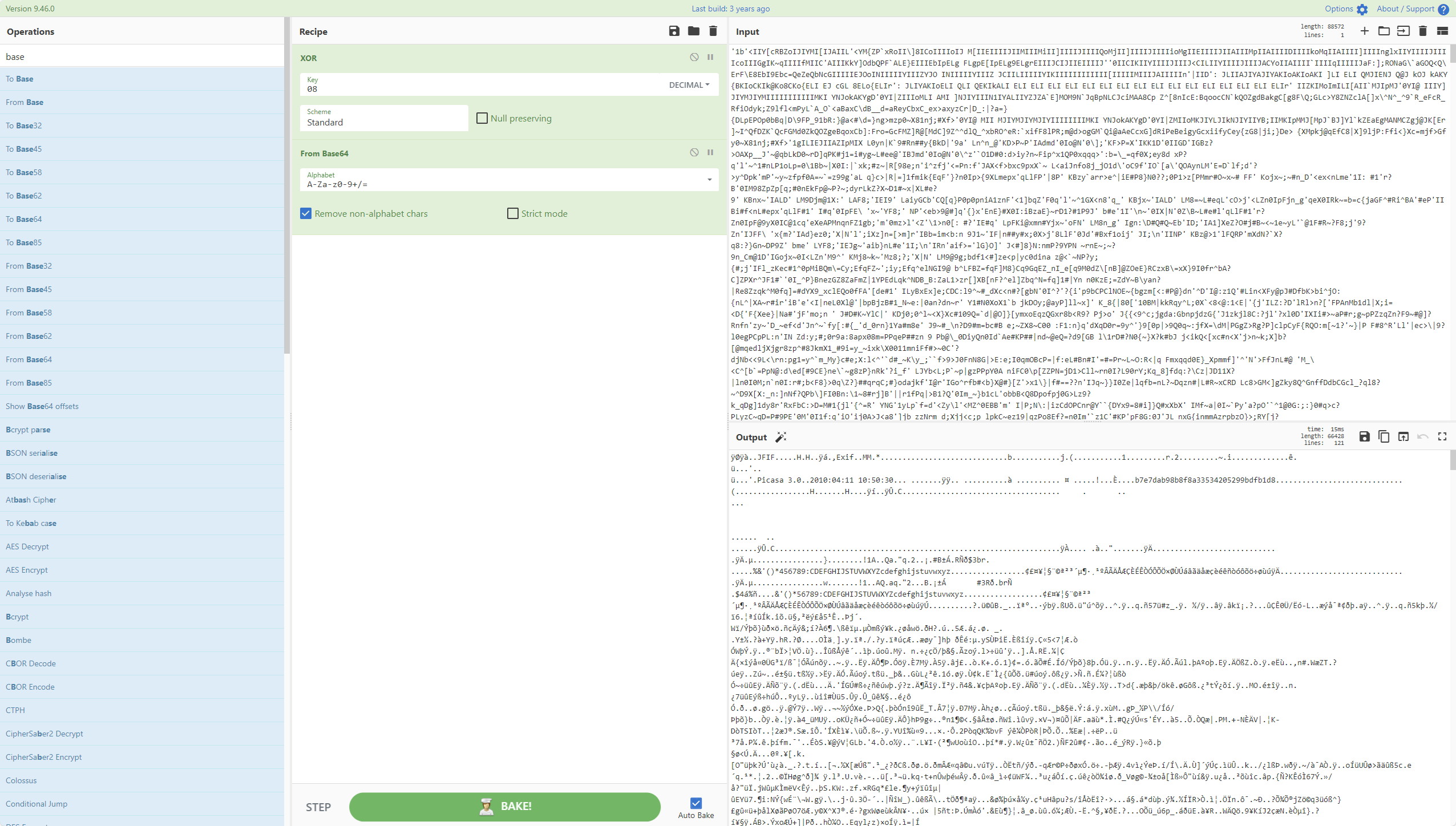
计算机取证-7 20 题目描述 计算机中sharisun520@hotmail.com 在2010年5月11日收到的邮件附件图片中的联系电话为? (6.0分)
没有正确解析 导出附件
看到加密方式base64+xor(08) 去赛博厨子解密
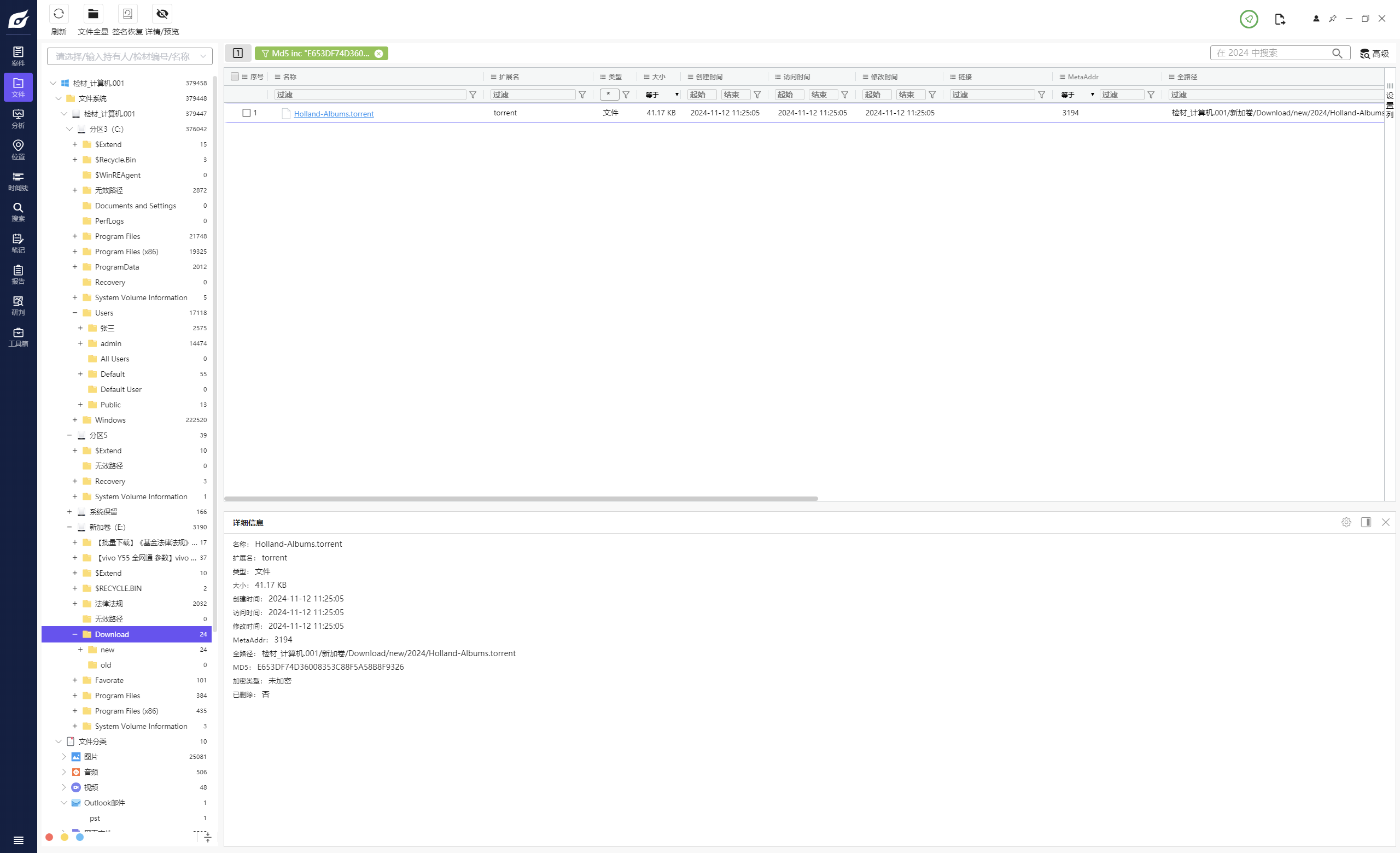
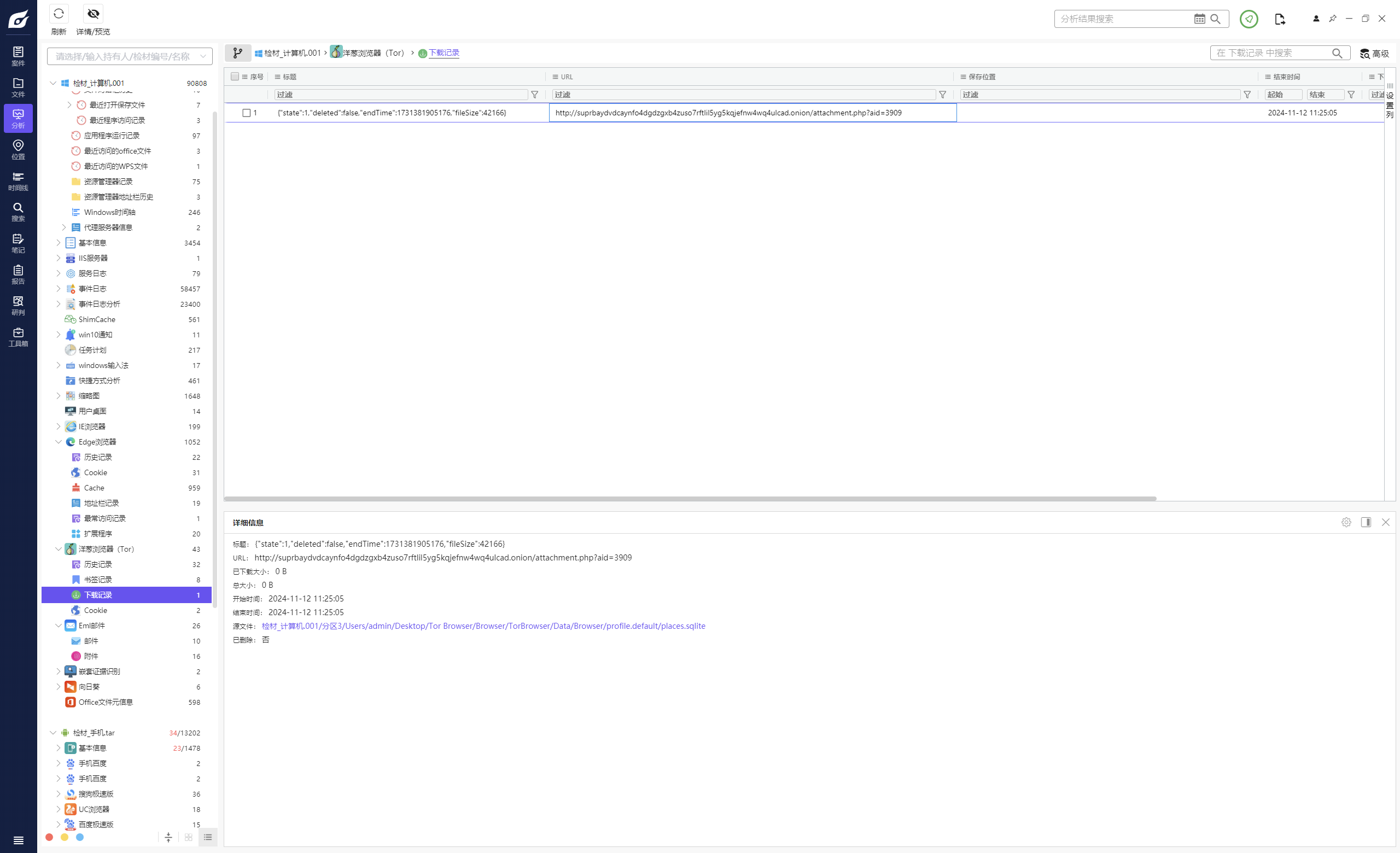
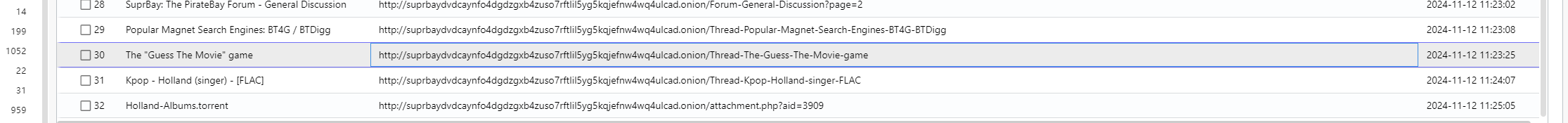
计算机取证-8 20 题目描述 计算机中MD5值为E653DF74D36008353C88F5A58B8F9326的文件是从哪个网址上下载的?(答案格式:http://abc/...) (1.0分)
1 http://suprbaydvdcaynfo4dgdzgxb4zuso7rftlil5yg5kqjefnw4wq4ulcad.onion/attachment.php?aid=3909
计算机取证-9 20 题目描述 计算机中2024年11月12日 11:23:25访问的暗网网址为?(答案格式:http://abc/...) (1.0分)
1 http://suprbaydvdcaynfo4dgdzgxb4zuso7rftlil5yg5kqjefnw4wq4ulcad.onion/Thread-The-Guess-The-Movie-game
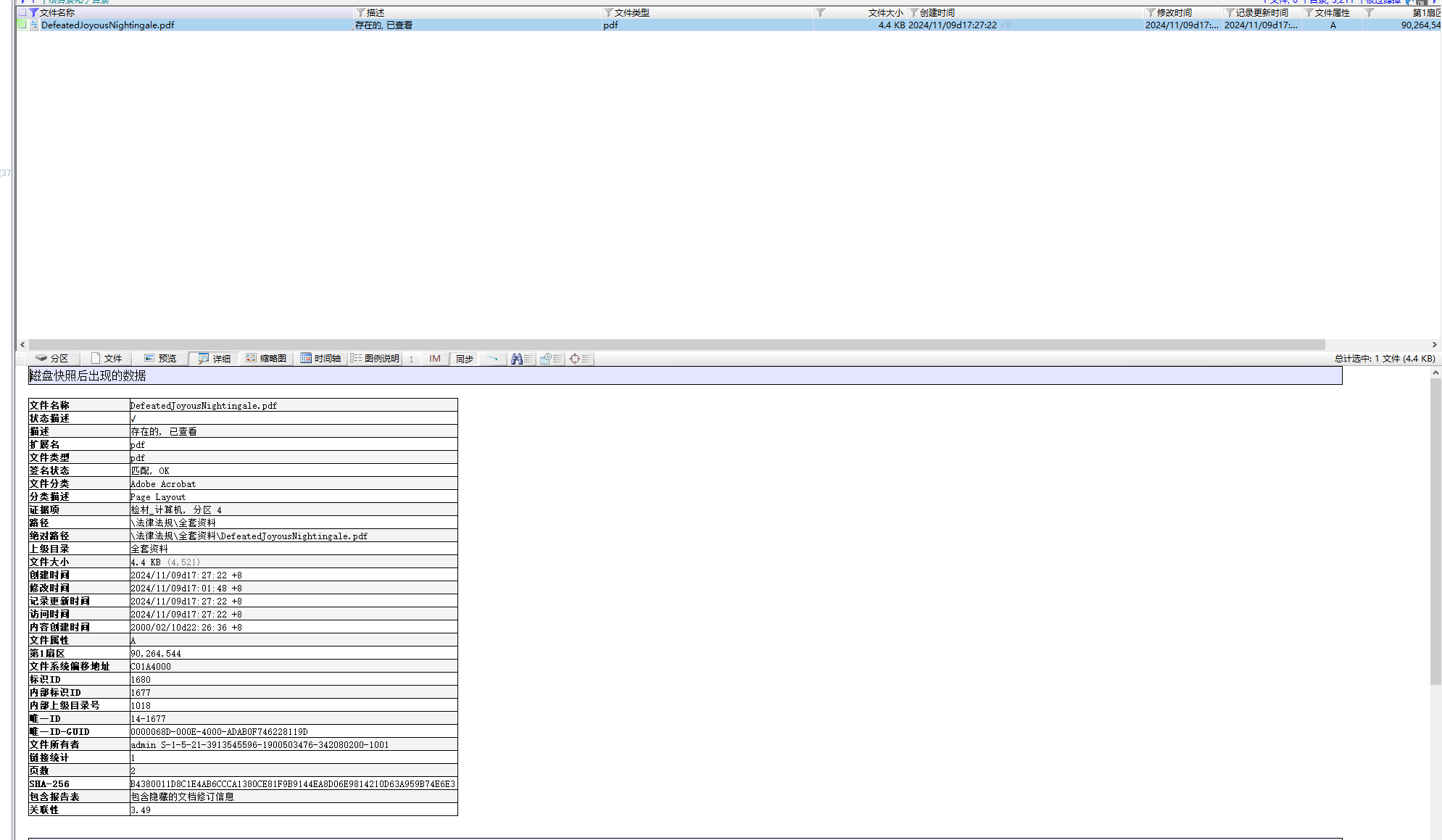
计算机取证-10 20 题目描述 请找到嫌疑人曾经接收的文件“DefeatedJoyousNightingale.pdf“,计算其SHA-256值;(答案格式:如遇字母全大写) (6.0分)
1 B4380011D8C1E4AB6CCCA1380CE81F9B9144EA8D06E9814210D63A959B74E6E3
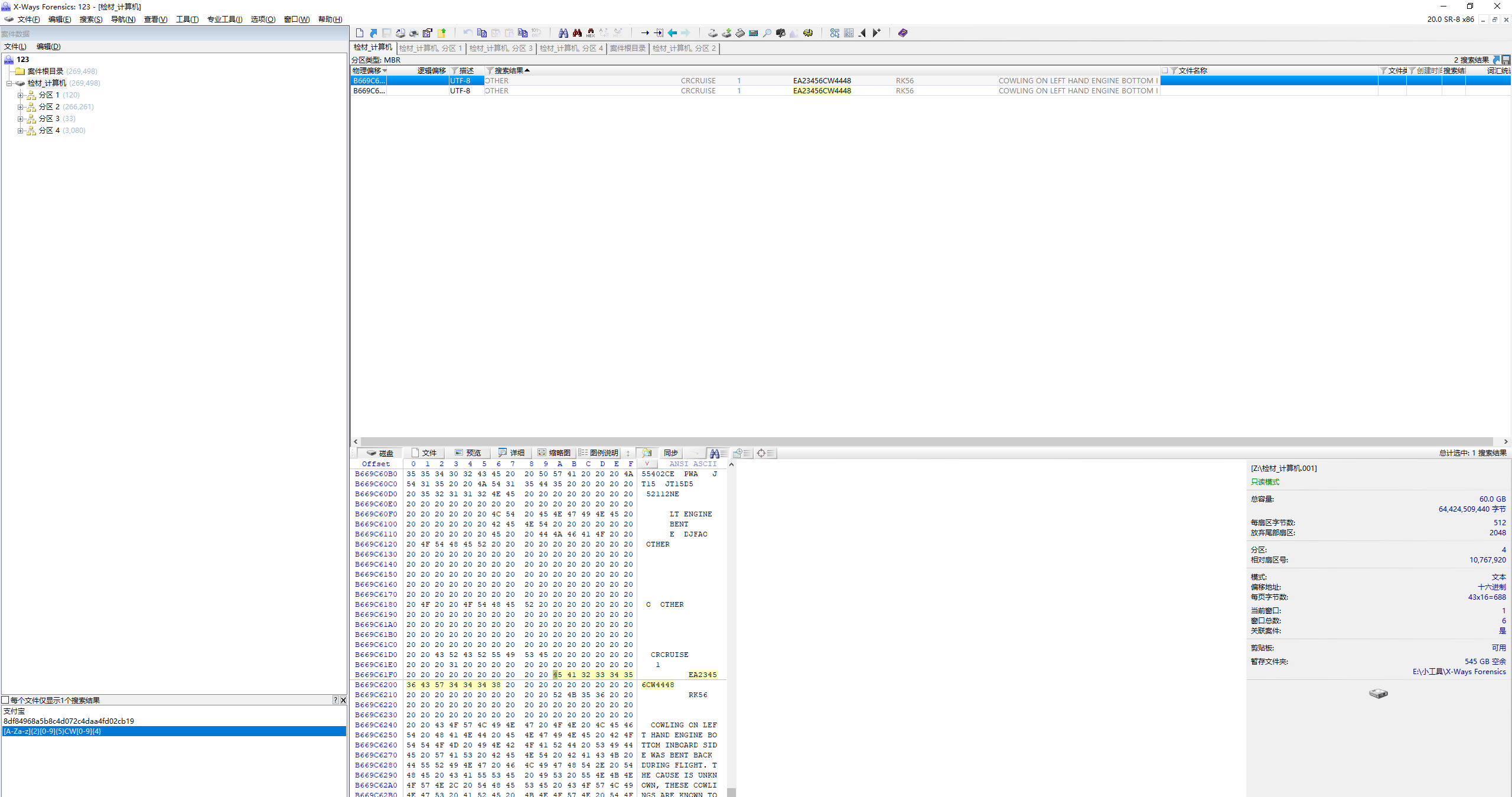
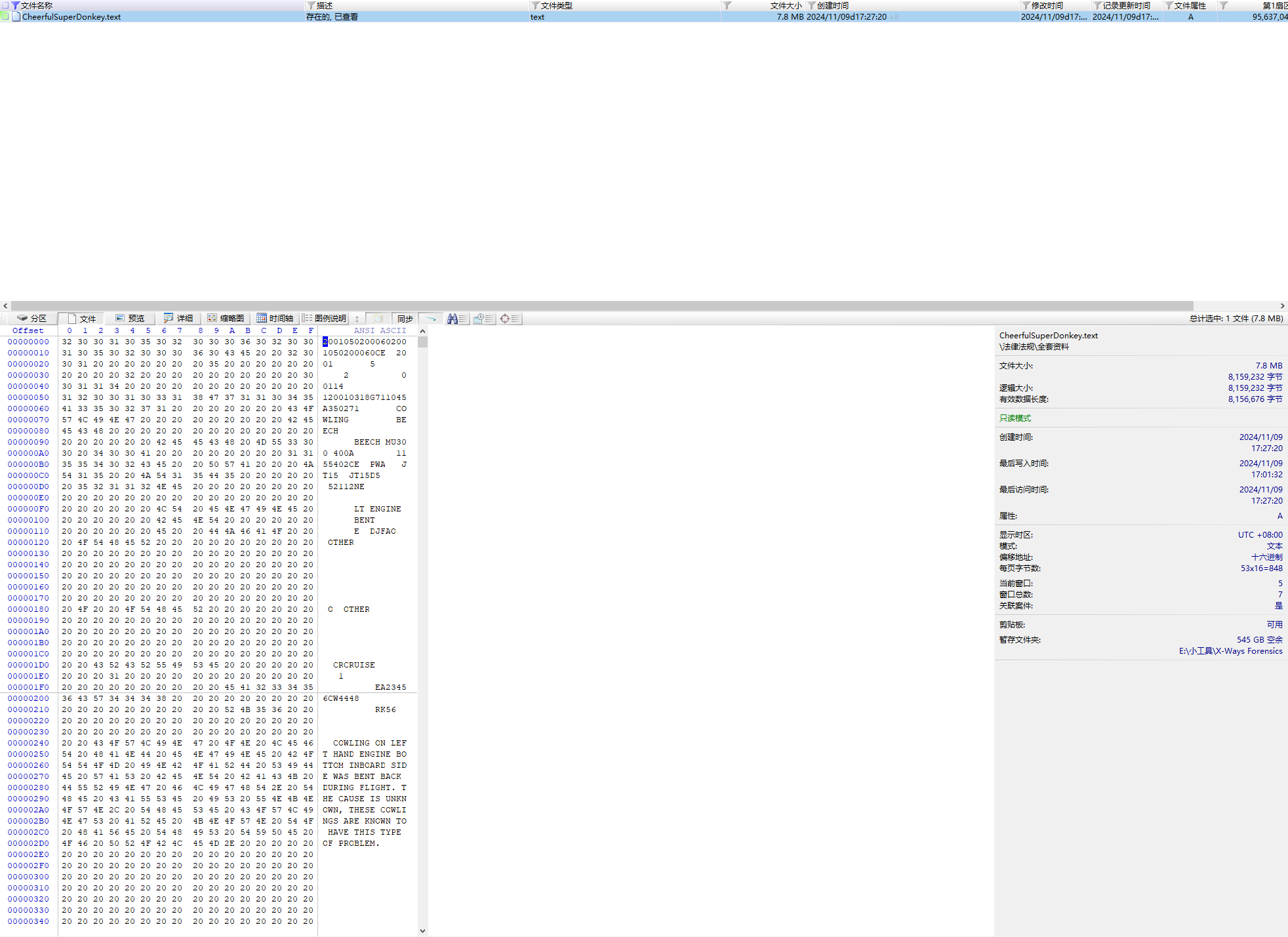
计算机取证-11 20 题目描述 计算机中包含由两个字母、五个数字、“CW”和四个数字组成的内容的文件名是?(答案格式:需带后缀名,如Abc.doc) (3.0分)
1 CheerfulSuperDonkey.text
GREP语法
1 [A-Za-z]{2}[0-9]{5}CW[0-9]{4}
计算机取证-12 20 题目描述 请写出计算机中系统分区上文件系统的卷序列号;(答案格式:全部8字节,小端序,忽略空格,如FA33C08ED0BC007C) (2.0分)
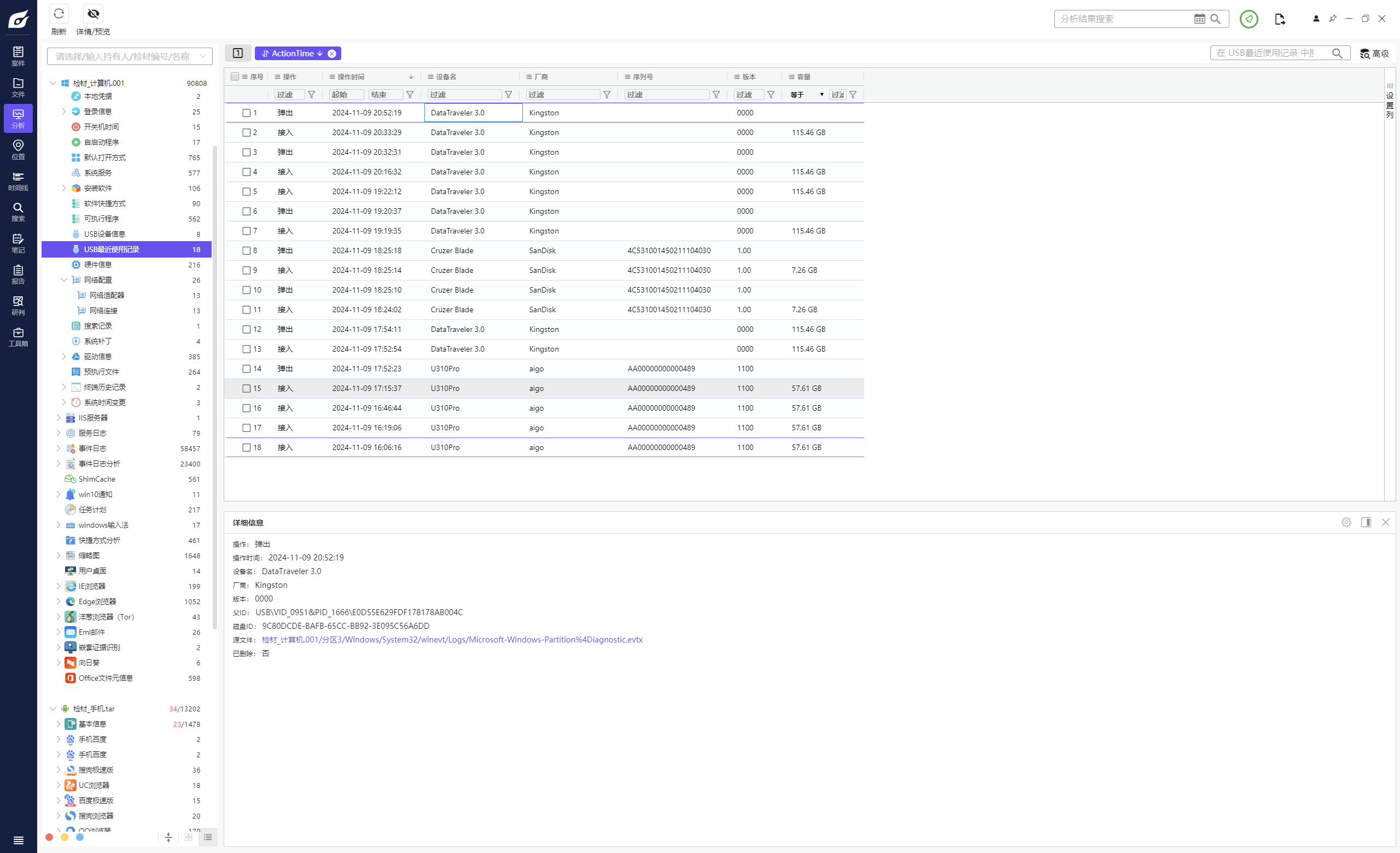
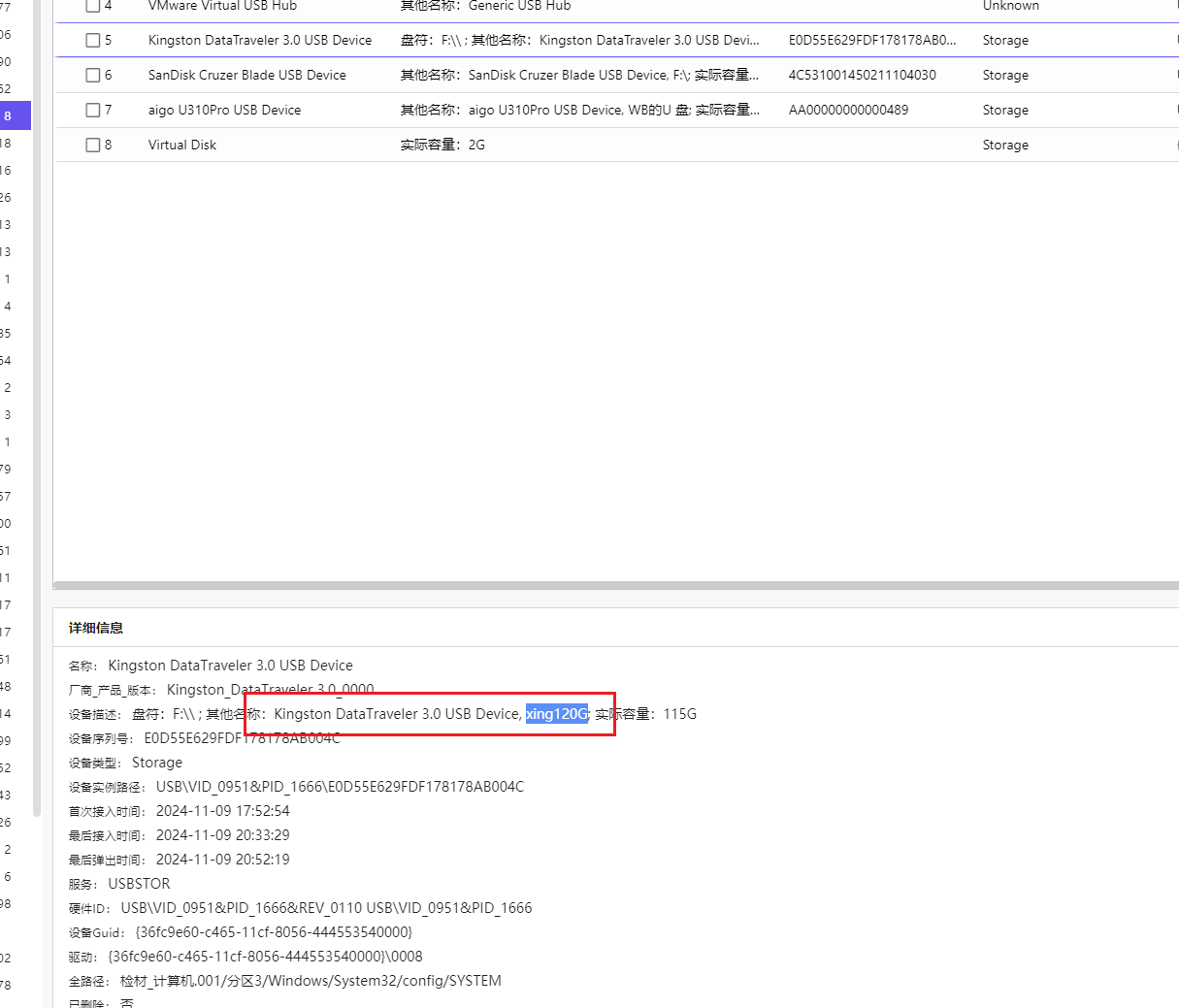
计算机取证-13 20 题目描述 计算机中最后接入的U盘的卷标名称是什么?(答案格式:如abcd111A) (5.0分)
或查看注册表
1 HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR
计算机取证-14 20 题目描述 计算机中程序wordpad.exe一共运行了多少次?(答案格式:请直接写数字,如6) (1.0分)
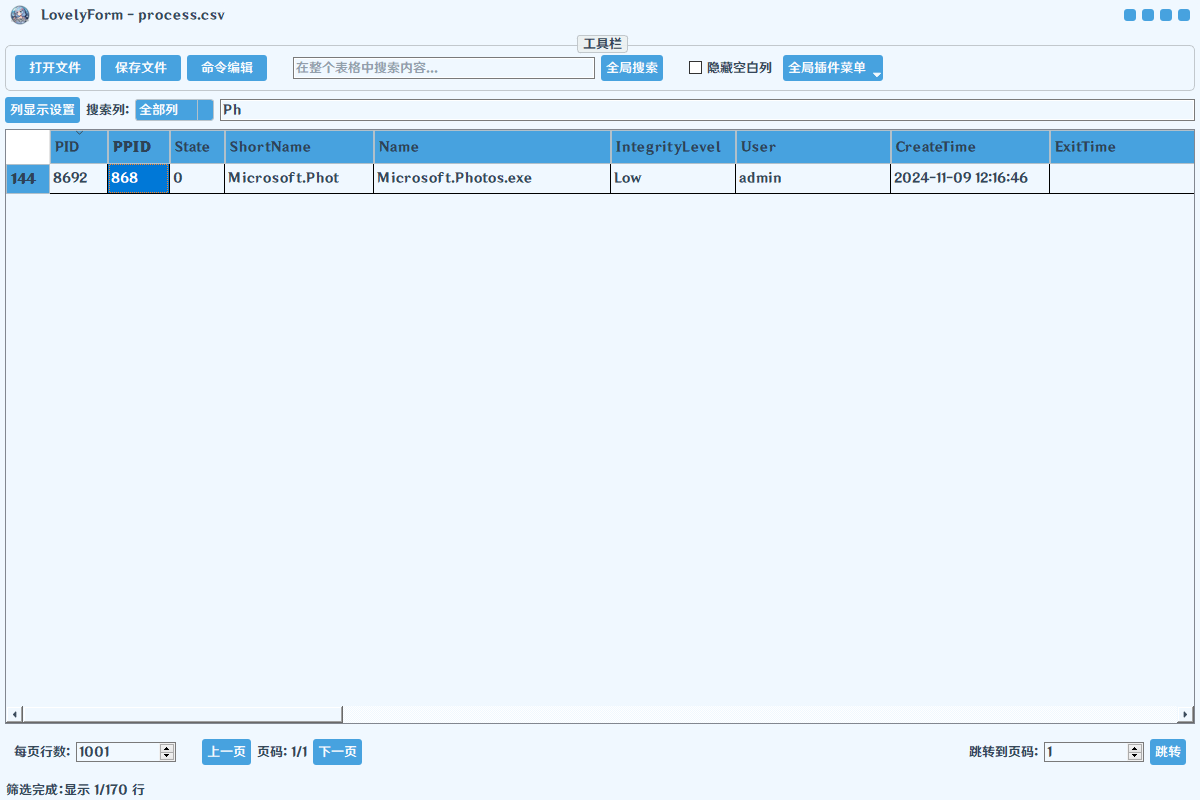
计算机取证-15 20 题目描述 计算机内存中正打开的图片中的动物为?(答案格式:直接写出动物名称,如狗) (4.0分)
在M:\name\Microsoft.Phot-8692\minidump找到对应进程的minidump
直接foremost出图片,或者后缀改data去gimp调参数
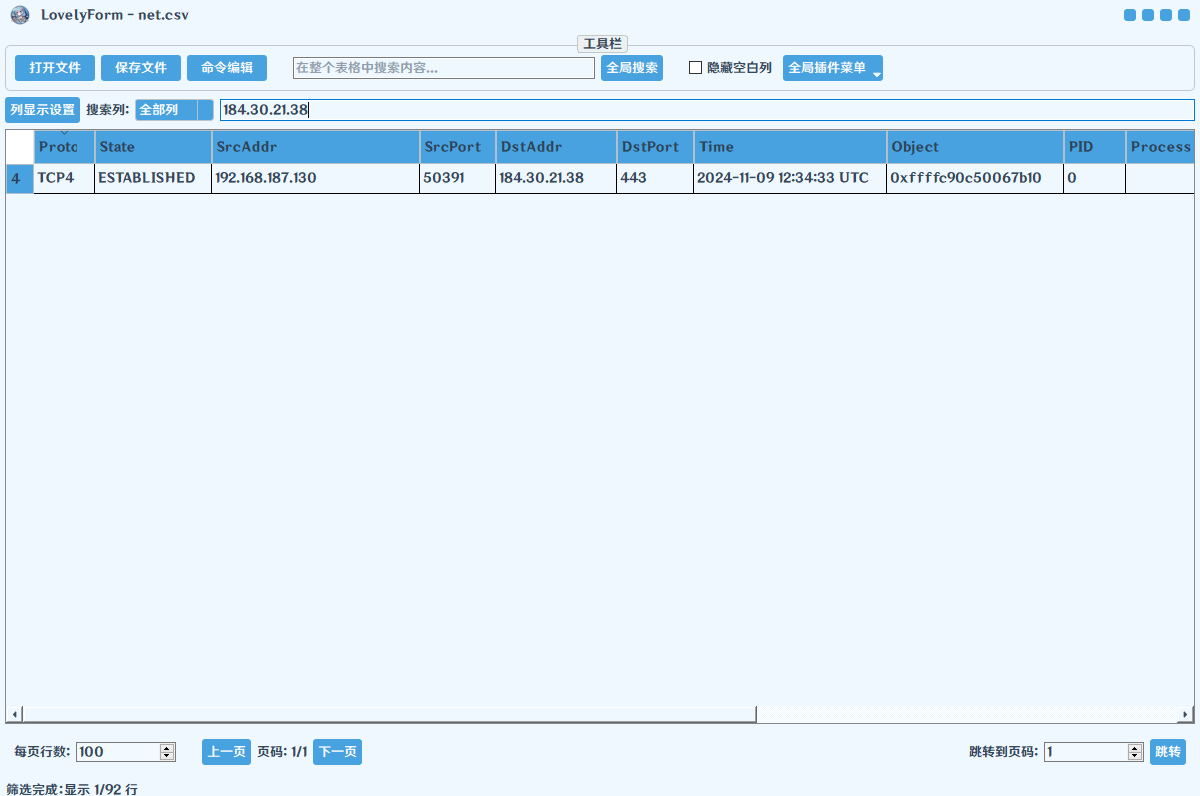
计算机取证-16 20 题目描述 计算机内存中本地浏览器使用哪个端口连接到了184.30.21.38?(答案格式:纯数字) (2.0分)
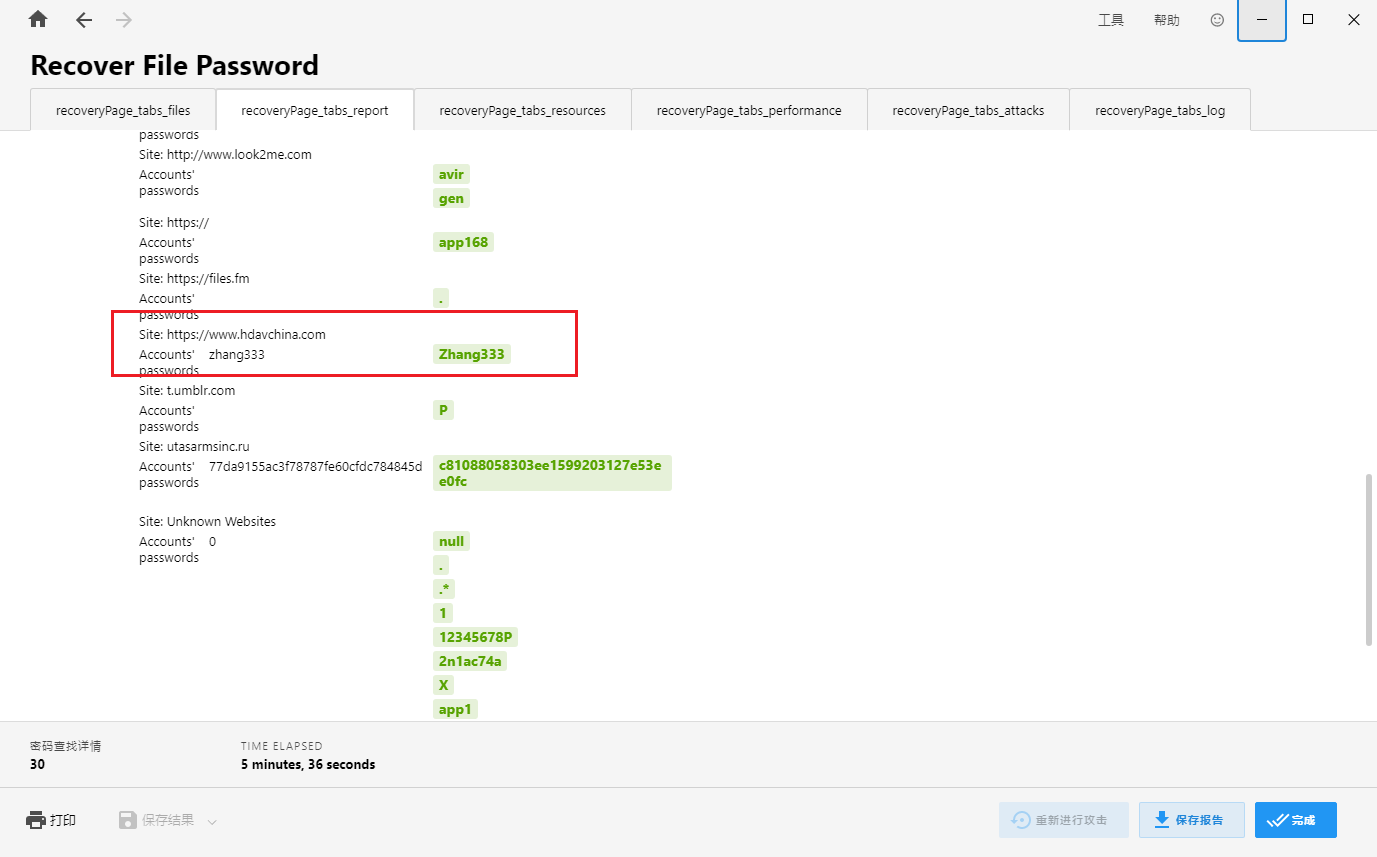
计算机取证-17 20 题目描述 计算机内存中极速浏览器最后浏览的网址的登录密码?(答案格式:与实际大小写需一致) (5.0分)
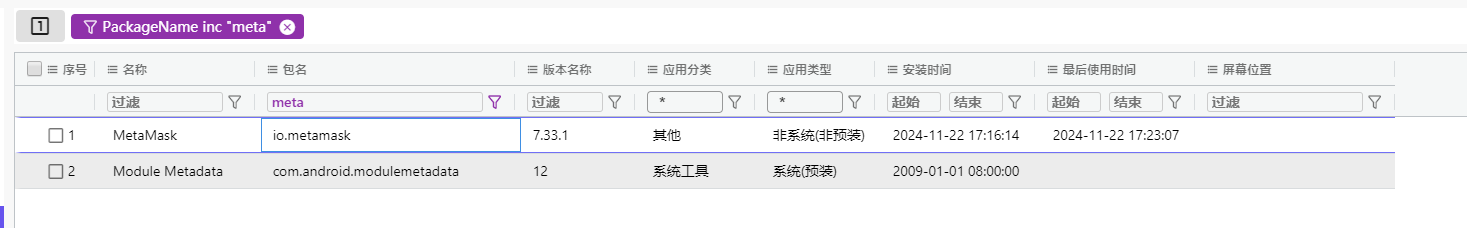
手机取证 手机取证-1 20 题目描述 分析手机检材,请找出嫌疑人的手机号; (2.0分)
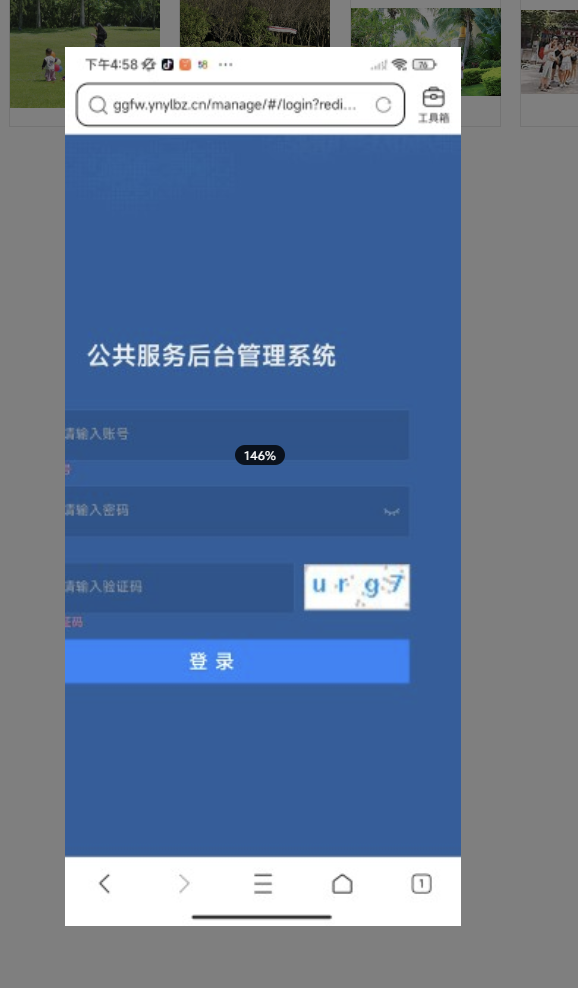
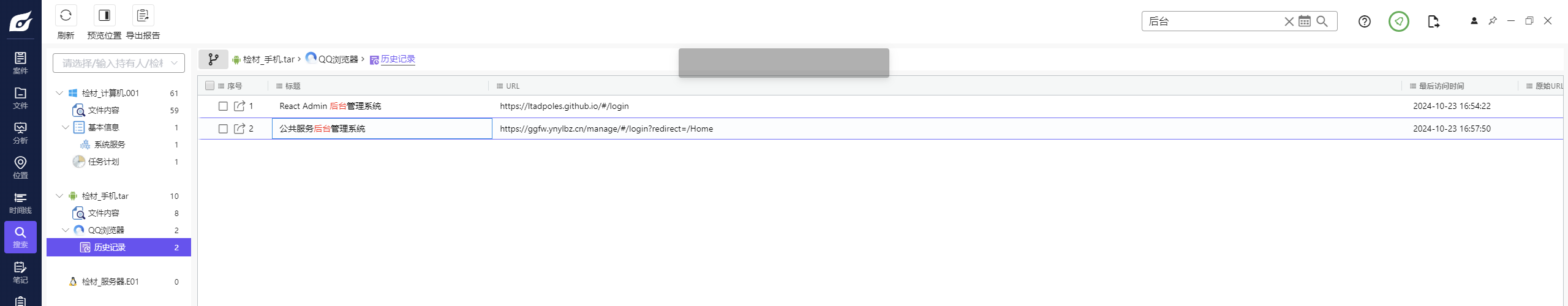
手机取证-2 20 题目描述 分析手机检材,嫌疑人曾经访问的公共服务后台管理系统的URL是?(答题格式:https://abc/...) (4.0分)
1 https://ggfw.ynylbz.cn/manage/#/login?redirect=/Home
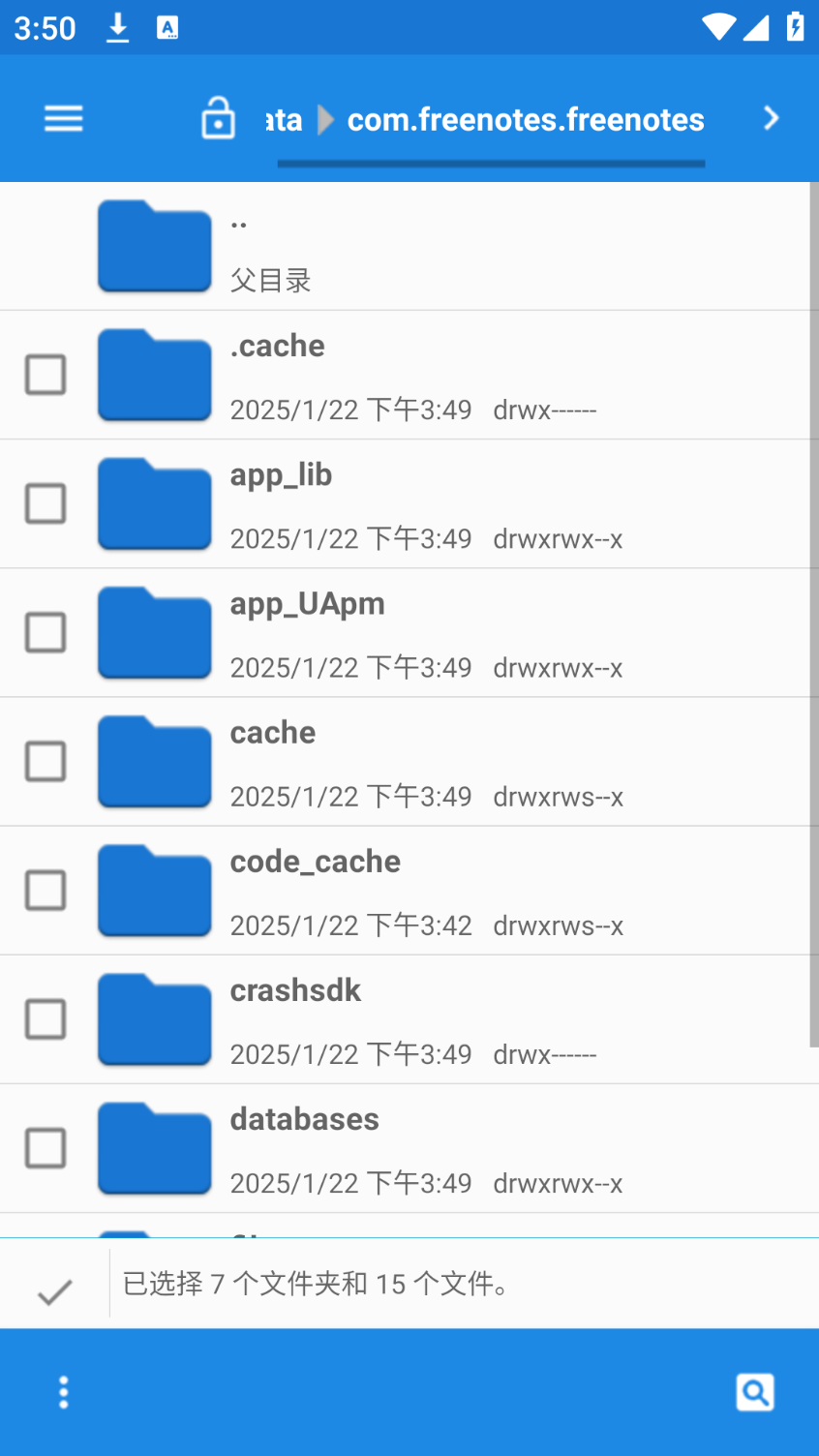
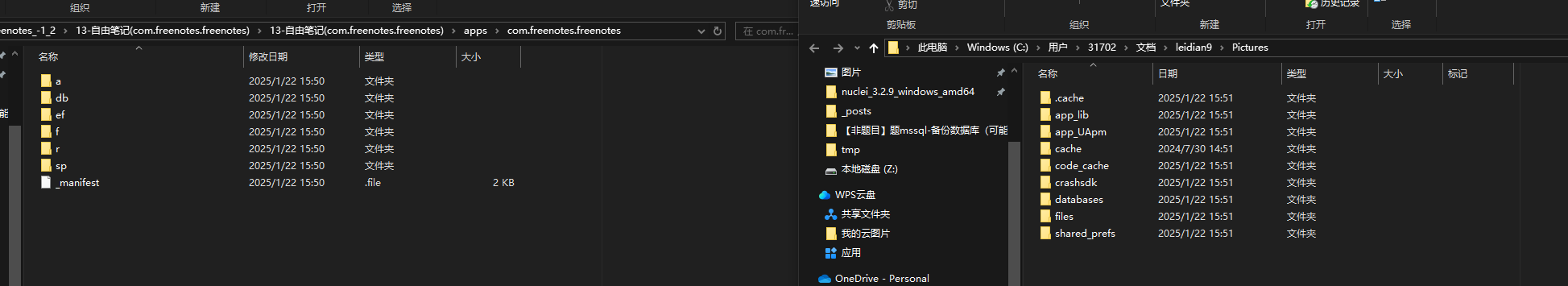
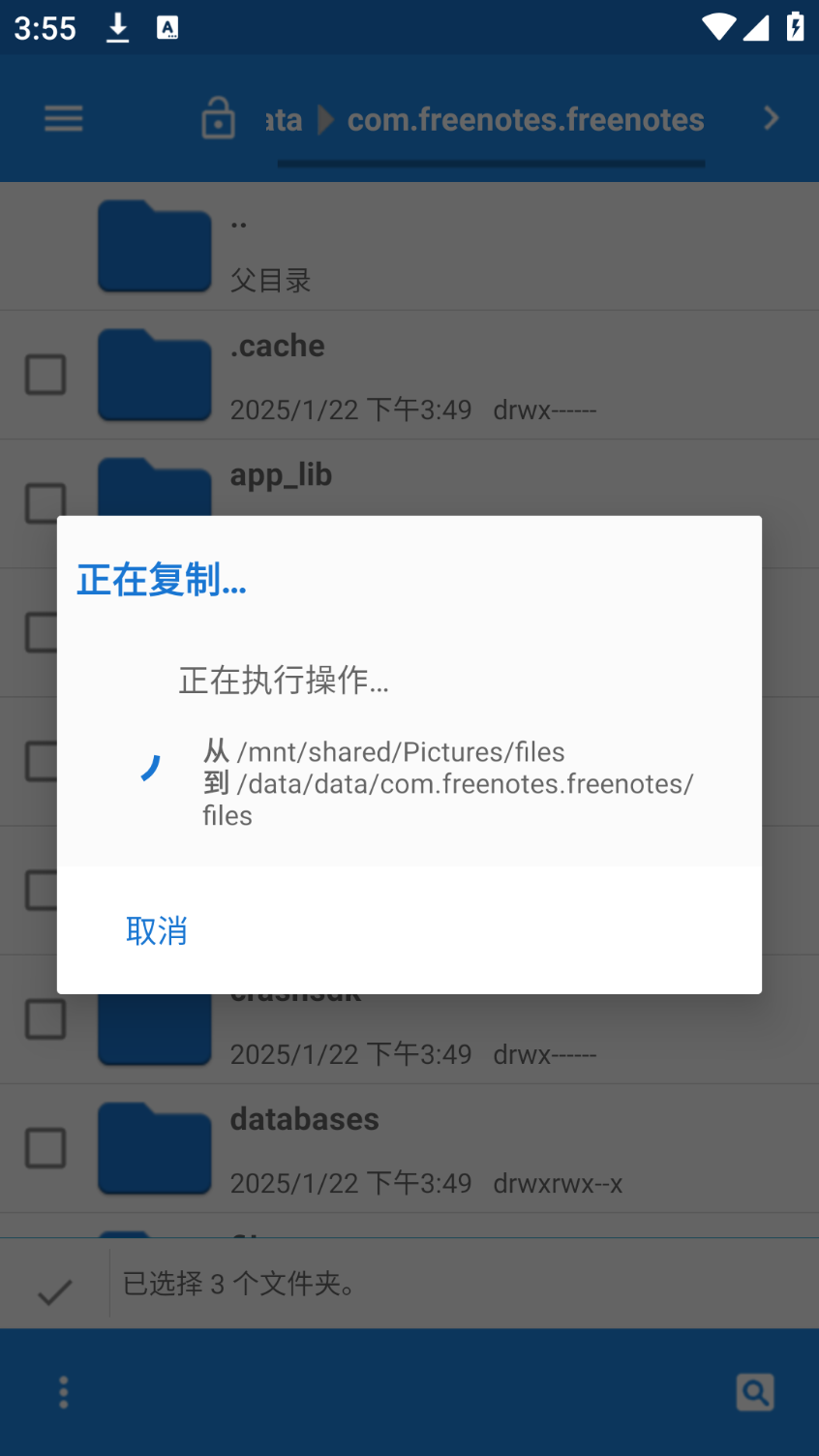
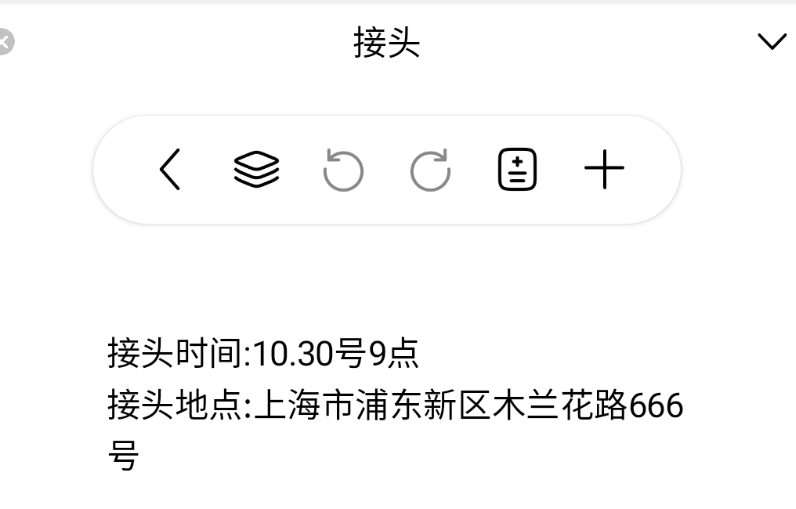
手机取证-3 20 题目描述 分析手机检材,找出嫌疑人在笔记中记录的接头地点;(答案格式:需与实际完全一致) (4.0分)
新建一个笔记 与已有的文件做对比
经比较 覆盖files databases shared_prefs r对应剩下几个
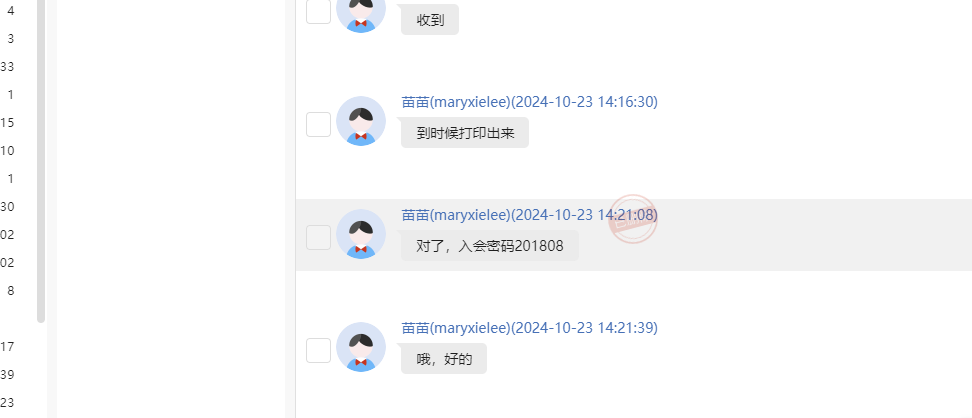
手机取证-4 20 题目描述 分析手机检材,找出嫌疑人的接头暗号;(答案格式:需与实际完全一致) (6.0分)
手机取证-5 20 题目描述 分析手机检材,找出嫌疑人10月23日开的腾讯会议的入会密码; (2.0分)
手机取证-6 20 题目描述 分析手机检材,找出嫌疑人公司即将发布的新产品型号;(答案格式:需与实际大小写完全一致) (4.0分)
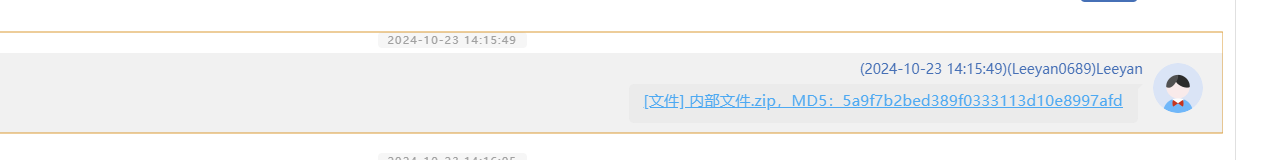
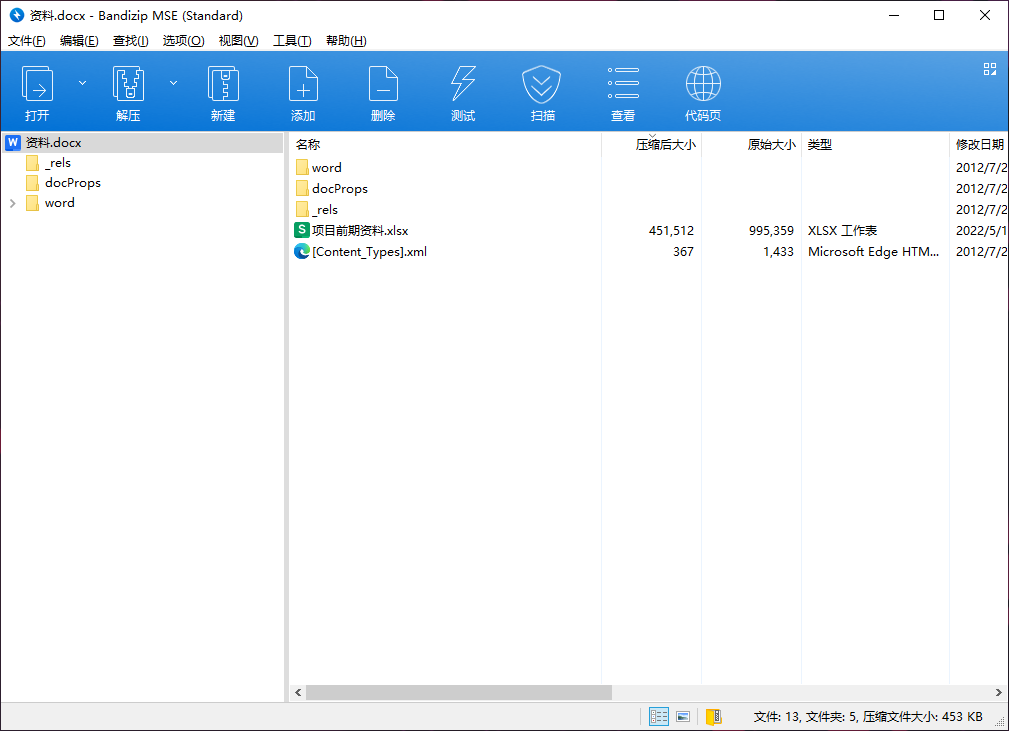
手机取证-7 20 题目描述 分析手机检材,找到嫌疑人曾经发送的项目前期资料文件,计算其SHA256;(答案格式:如遇字母全大写) (4.0分)
1 2425440B48170763AEA97931D806249A298AFAC72A4BED92A6494E6789ACDA19
项目前期资料内嵌在资料里
还是挺骚的
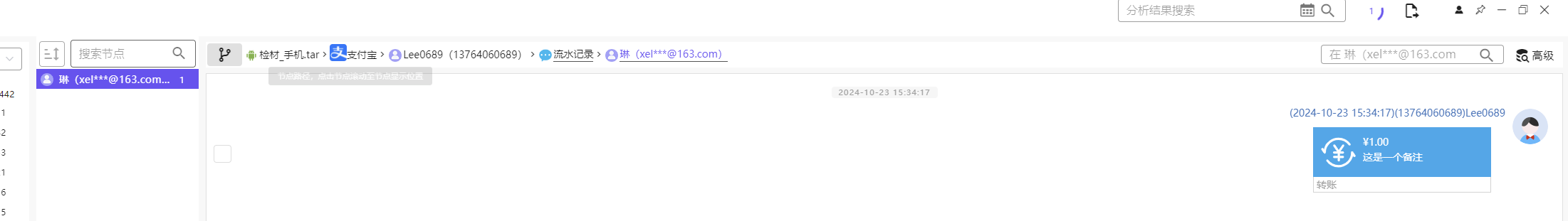
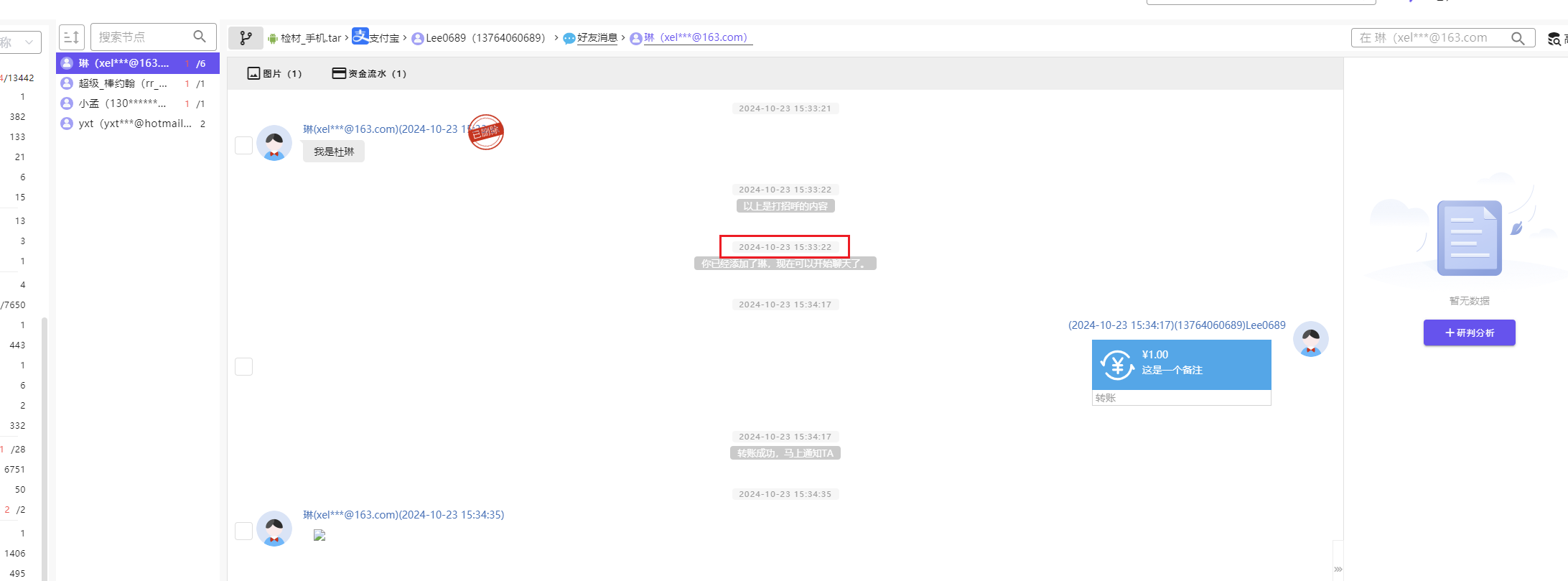
手机取证-8 20 题目描述 分析手机检材,嫌疑人曾进行过一次交易,请问嫌疑人与转账的接收者什么时候成为好友?(答案格式:2021-01-01 01:01:01) (2.0分)
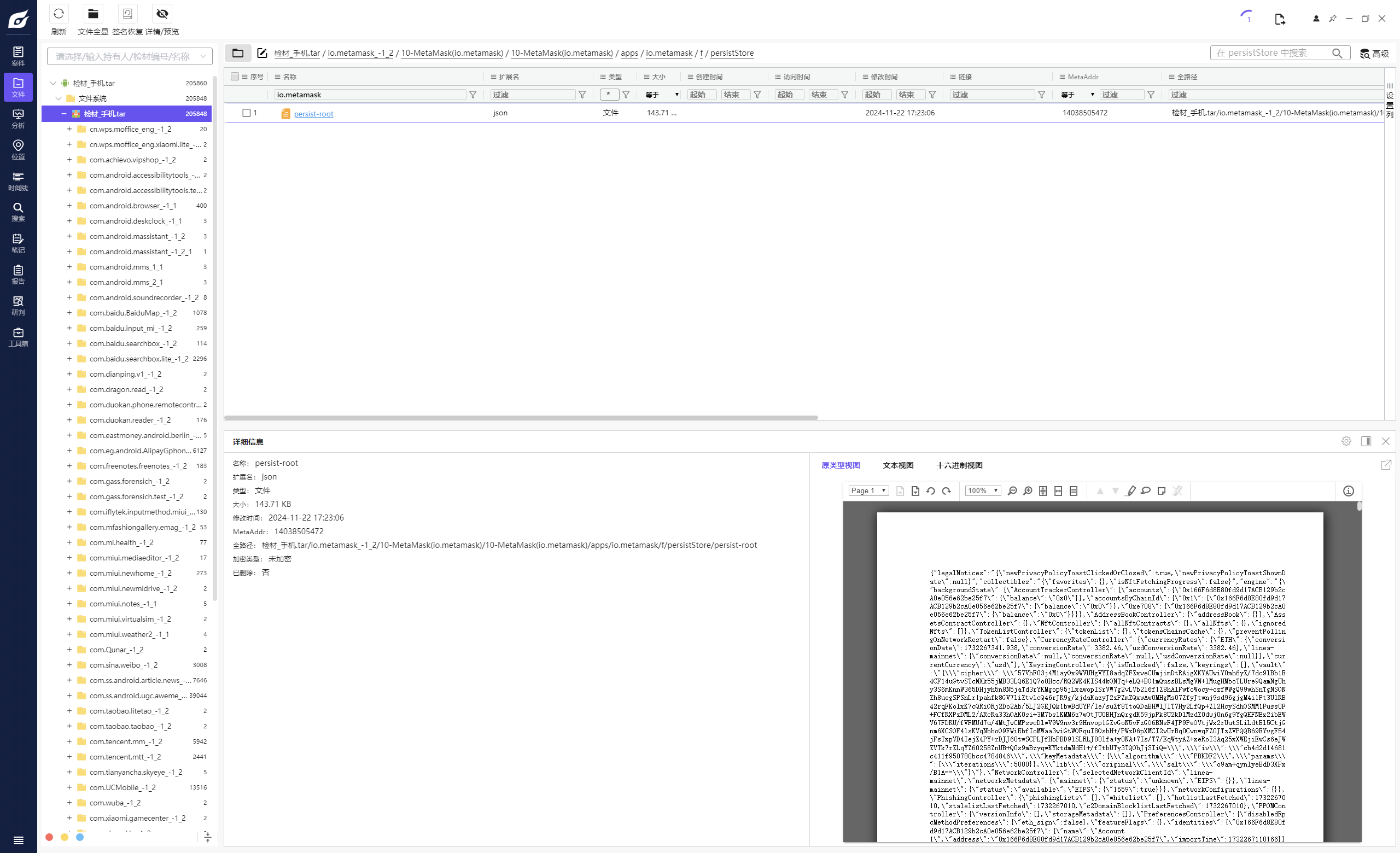
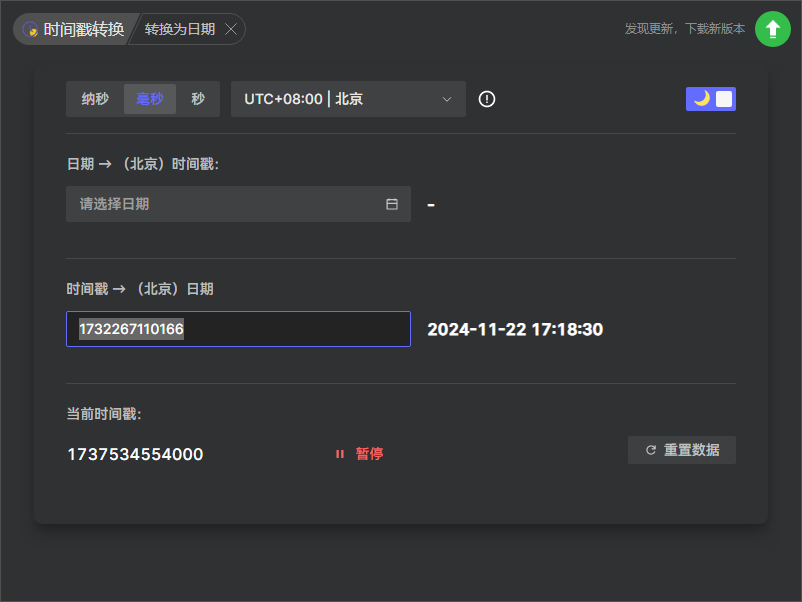
手机取证-9 20 题目描述 分析手机检材,写出嫌疑人钱包账户的导入时间;(北京时区,答案格式:1990-01-01 01:01:01) (6.0分)
服务器取证 服务器取证-1 20 题目描述 请写出服务器系统内核版本;(答案格式:1.1.1-11-abcdefe) (1.0分)
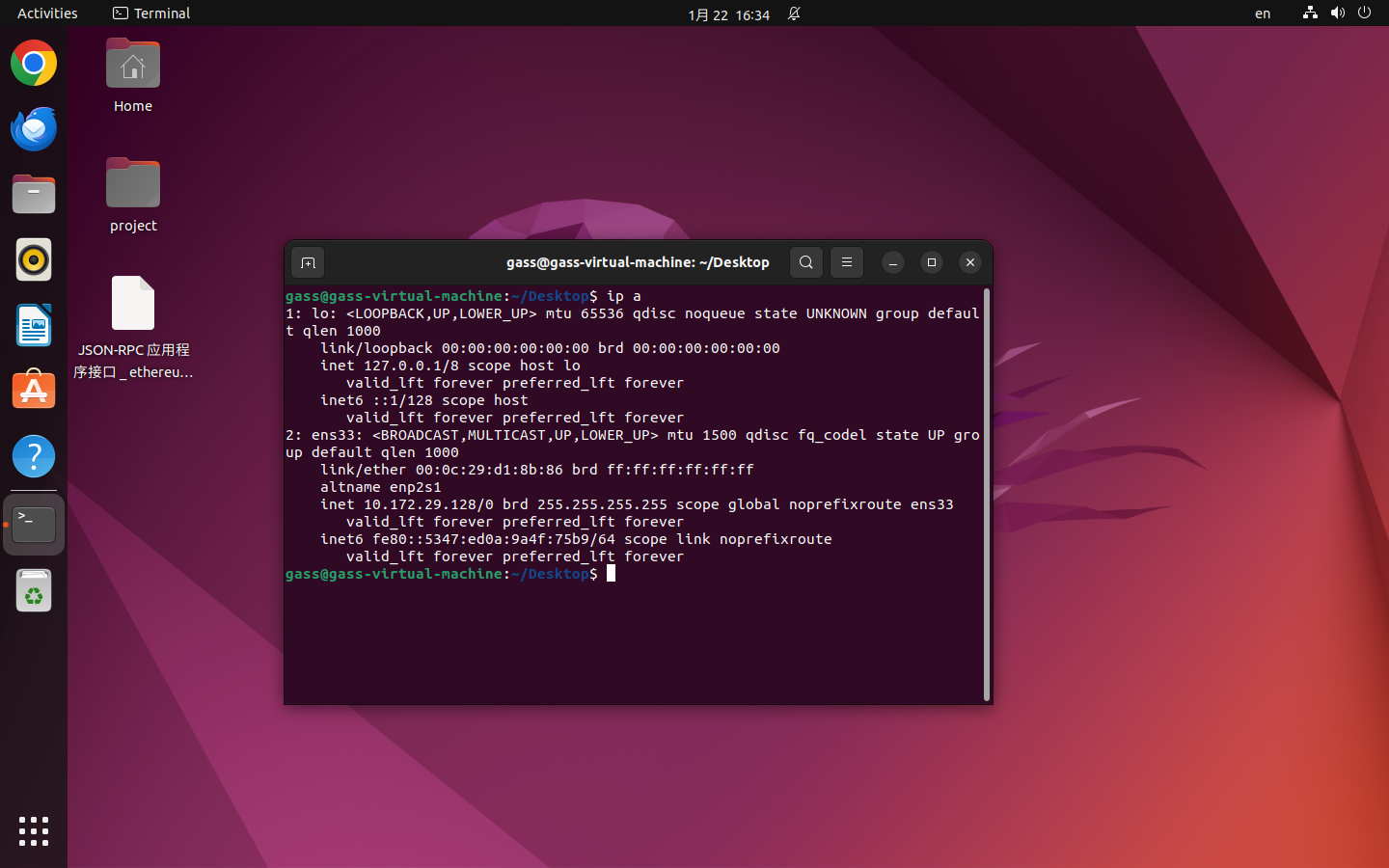
服务器取证-2 20 题目描述 请写出服务器的ens33网卡的ip地址; (1.0分)
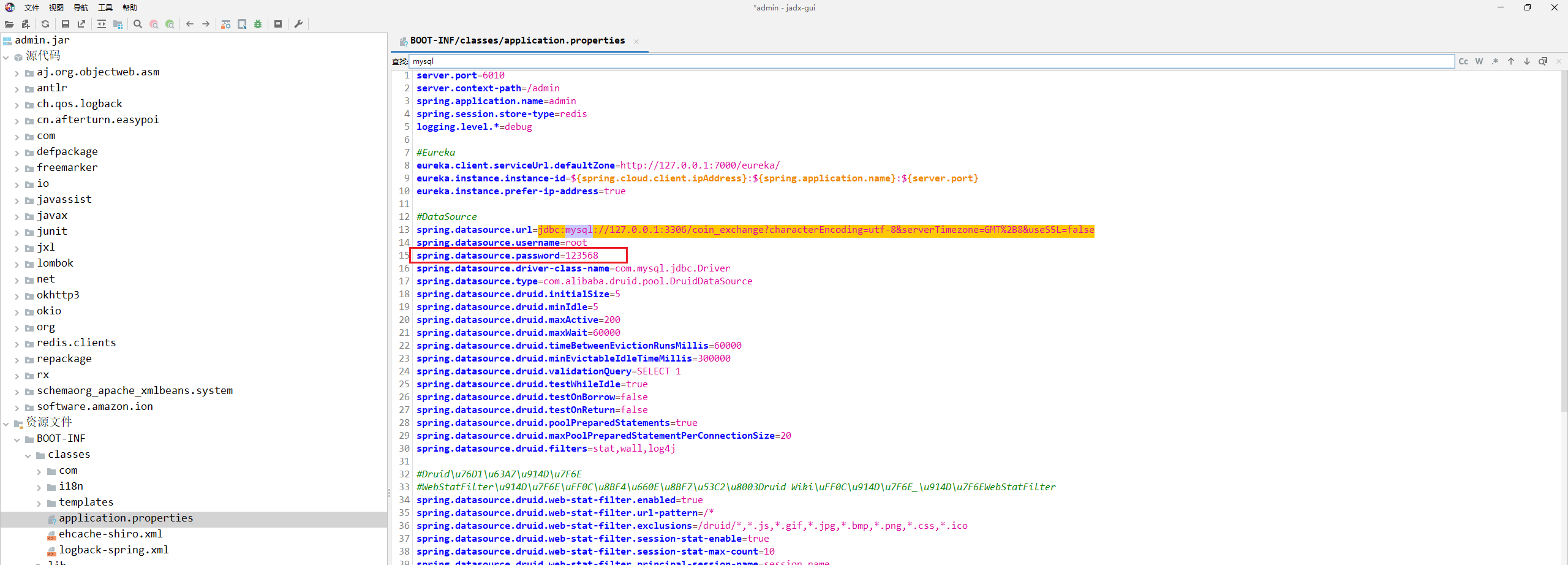
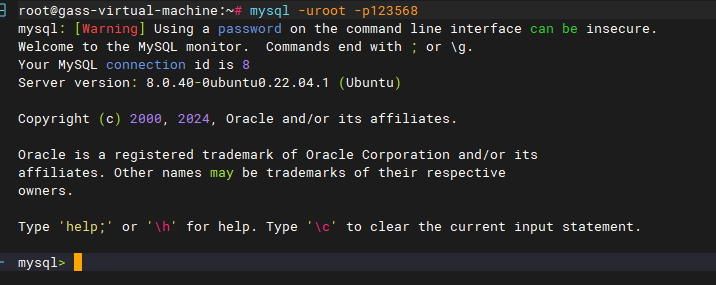
服务器取证-3 20 题目描述 请写出mysql数据库密码; (4.0分)
配一下网
1 2 3 root@gass-virtual-machine:/etc/netplan root@gass-virtual-machine:/etc/netplan root@gass-virtual-machine:/etc/netplan
1 2 3 4 5 6 7 8 9 10 11 12 13 network: version: 2 renderer: NetworkManager ethernets: ens33: dhcp4: no addresses: - 10.172 .29 .100 /8 routes: - to: default via: 10.172 .29 .2 nameservers: addresses: [8.8 .8 .8 , 8.8 .4 .4 ]
翻网站目录
验证一下
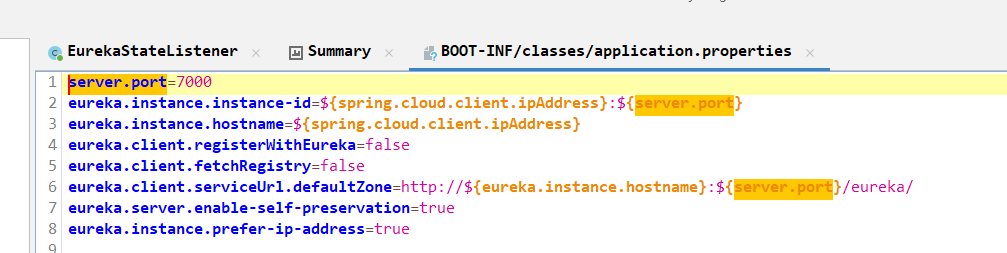
服务器取证-4 20 题目描述 后台服务中注册中心的服务端口是多少?(答案格式:纯数字) (2.0分)
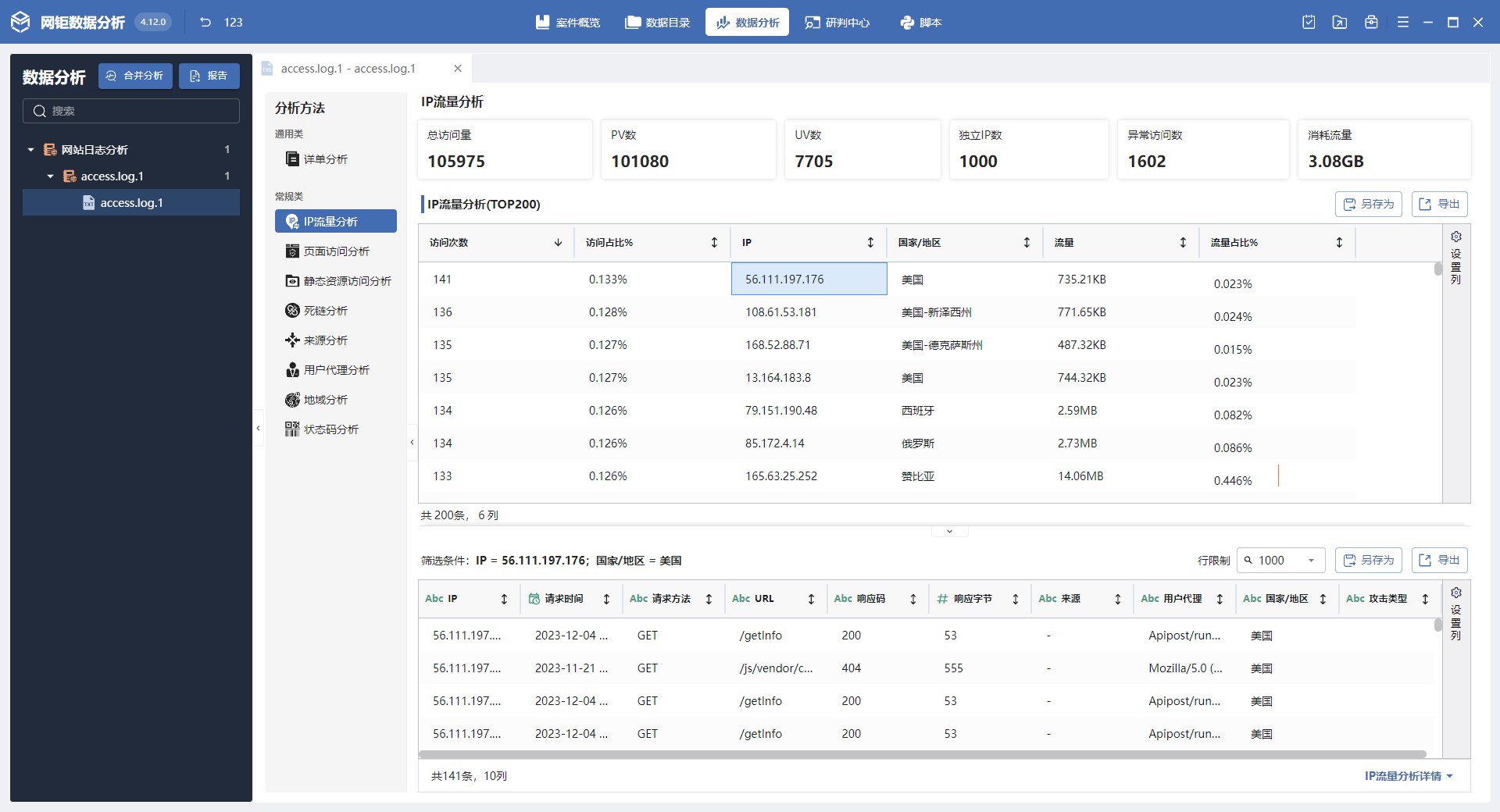
服务器取证-5 20 题目描述 服务器nginx日志中,哪个ip访问系统最为频繁?(答案格式:6.6.6.6) (6.0分)
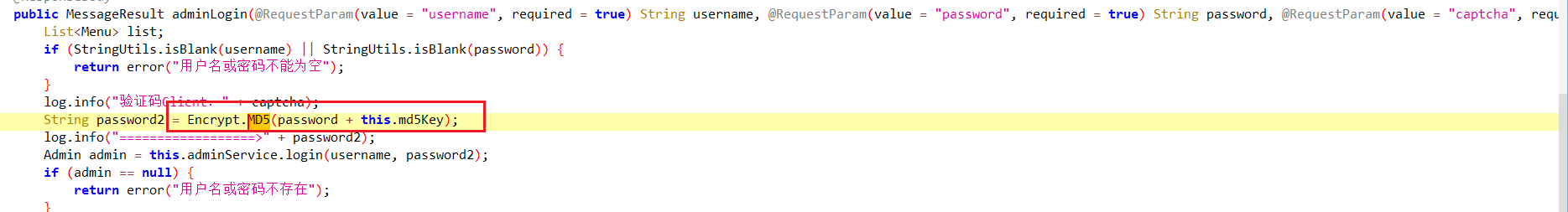
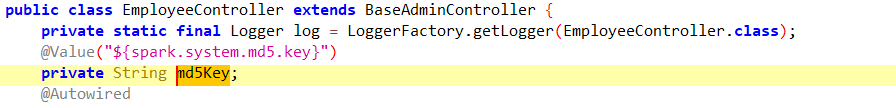
服务器取证-6 20 题目描述 请写出平台管理员密码加密算法;(答案格式:aes) (3.0分)
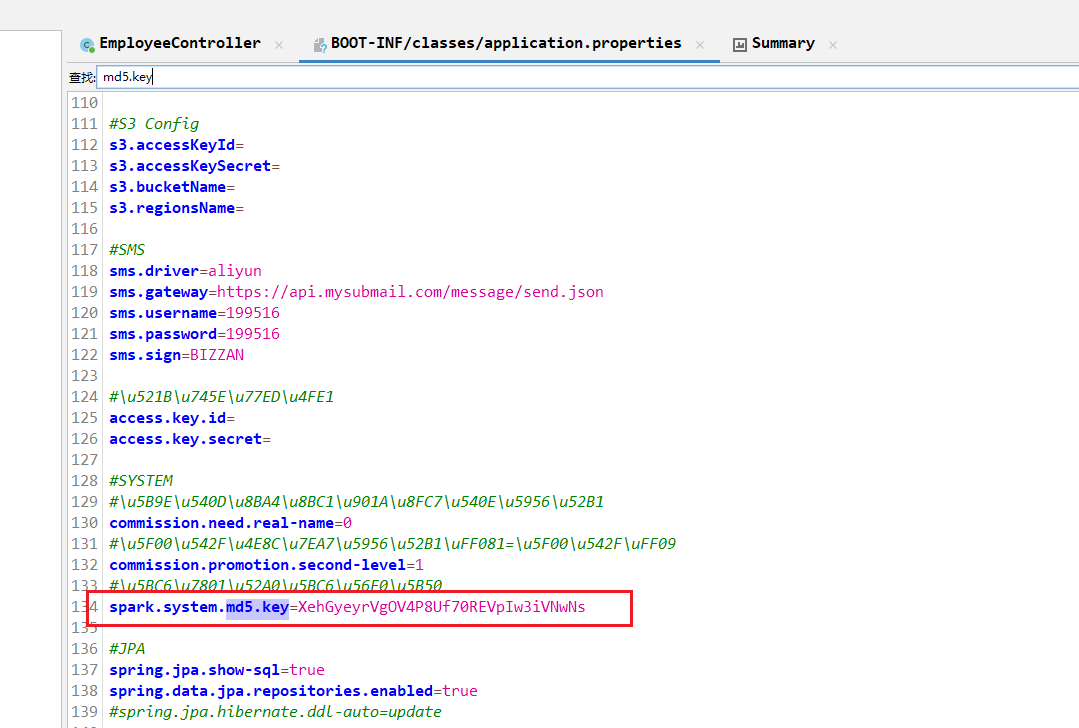
md5加盐 盐值在配置文件里拉
1 XehGyeyrVgOV4P8Uf70REVpIw3iVNwNs
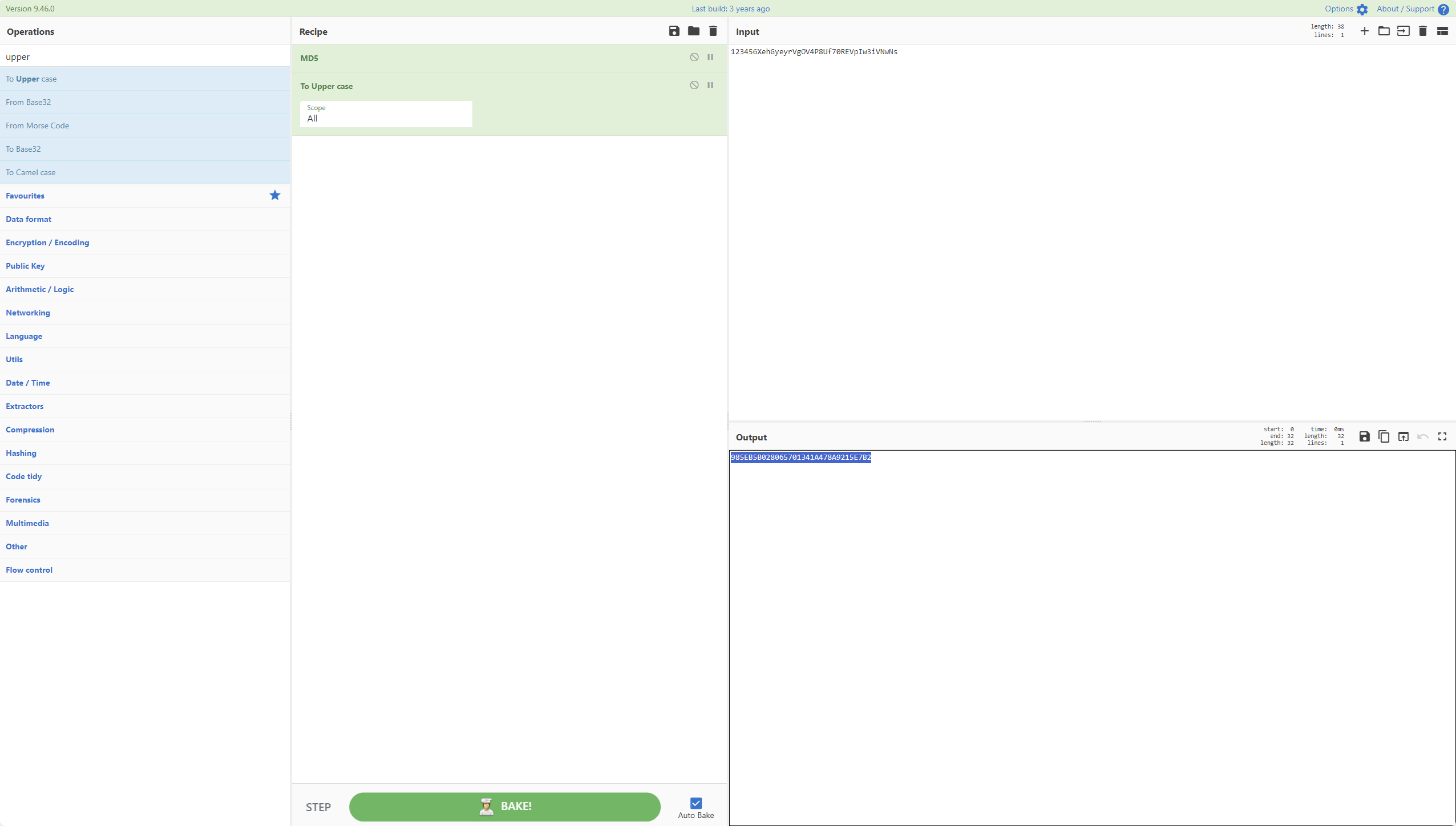
服务器取证-7 20 题目描述 假设某管理员密码是123456,请问该管理员的密码在数据库中存储的值是多少?(答案格式:如有字母,全大写) (5.0分)
1 985EB5B028065701341A478A9215E7B2
md5(123456XehGyeyrVgOV4P8Uf70REVpIw3iVNwNs)
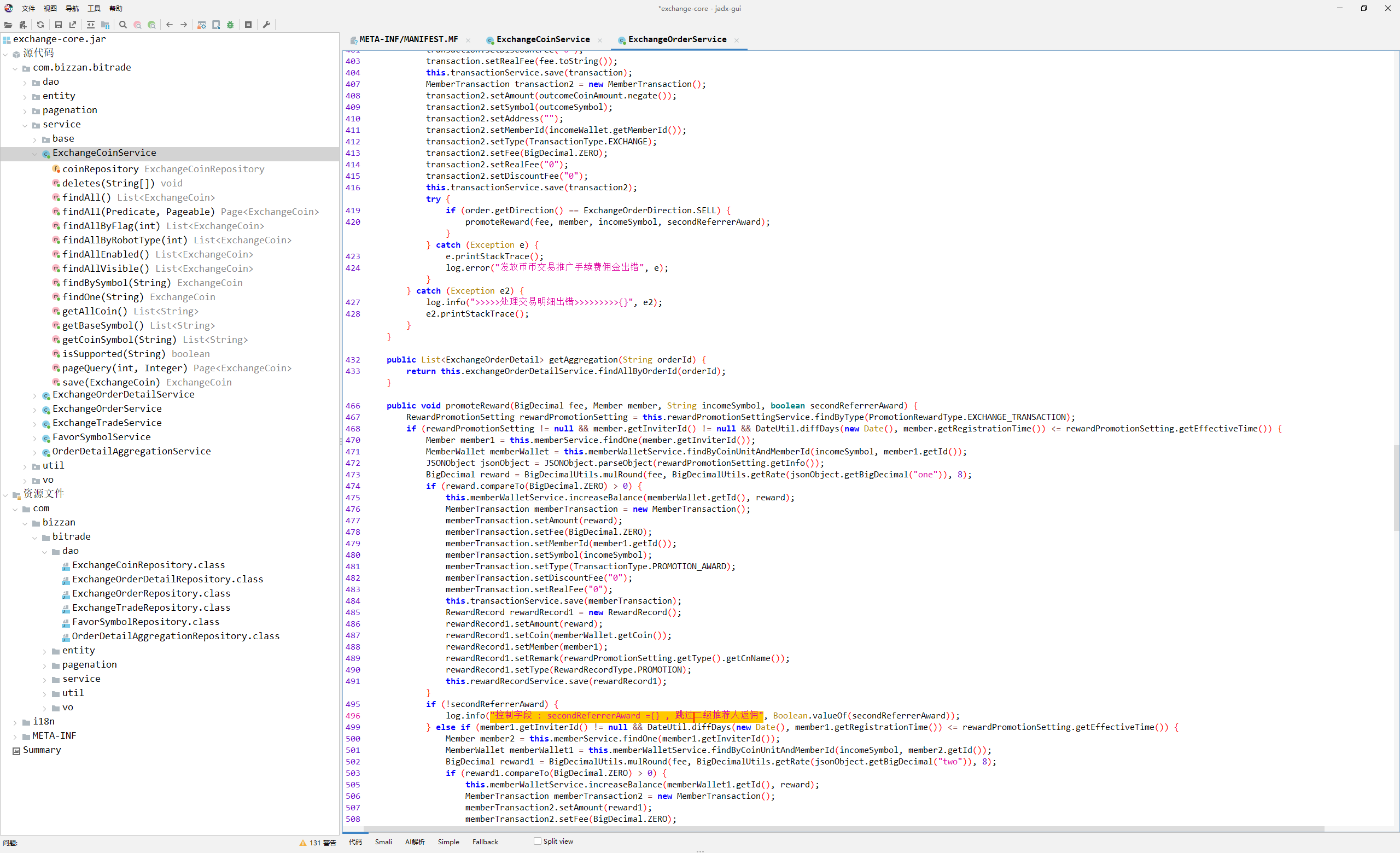
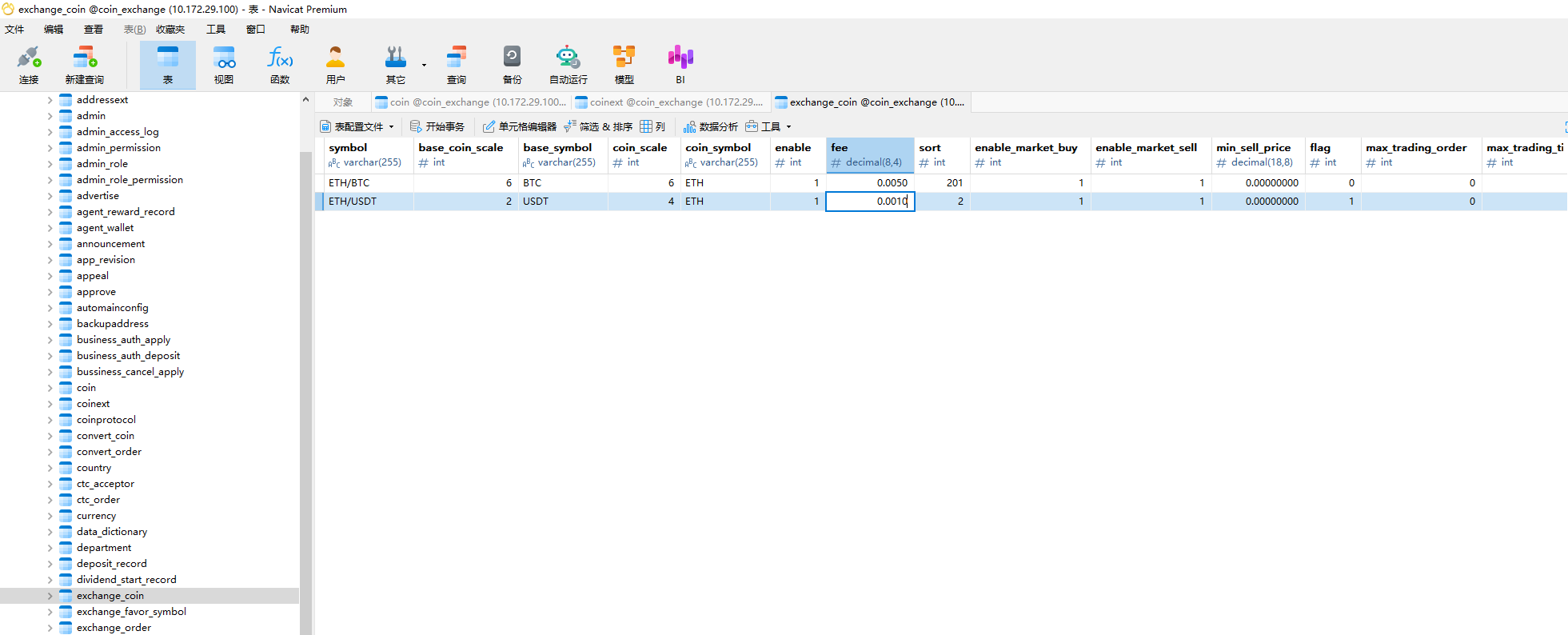
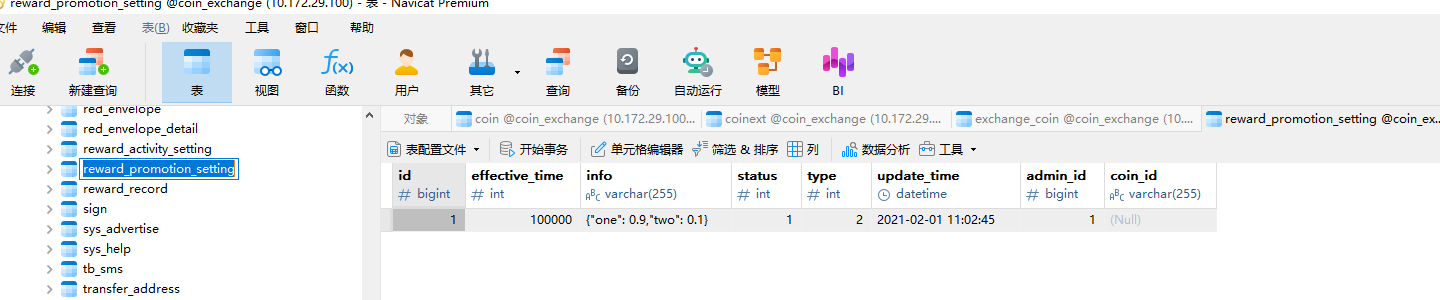
服务器取证-8 20 题目描述 已知某人卖出了5.2个ETH/USDT,请问他的二级推荐人可以获得多少个ETH佣金?(答案格式:写出数字即可,保留小数点后5位) (6.0分)
这一题比较难,首先要想做这一题,需要了解java开发的一些基本知识。
摘自 https://mp.weixin.qq.com/s/nb-5IzT92ONqXxrXYMU6Ug
查看对应规则
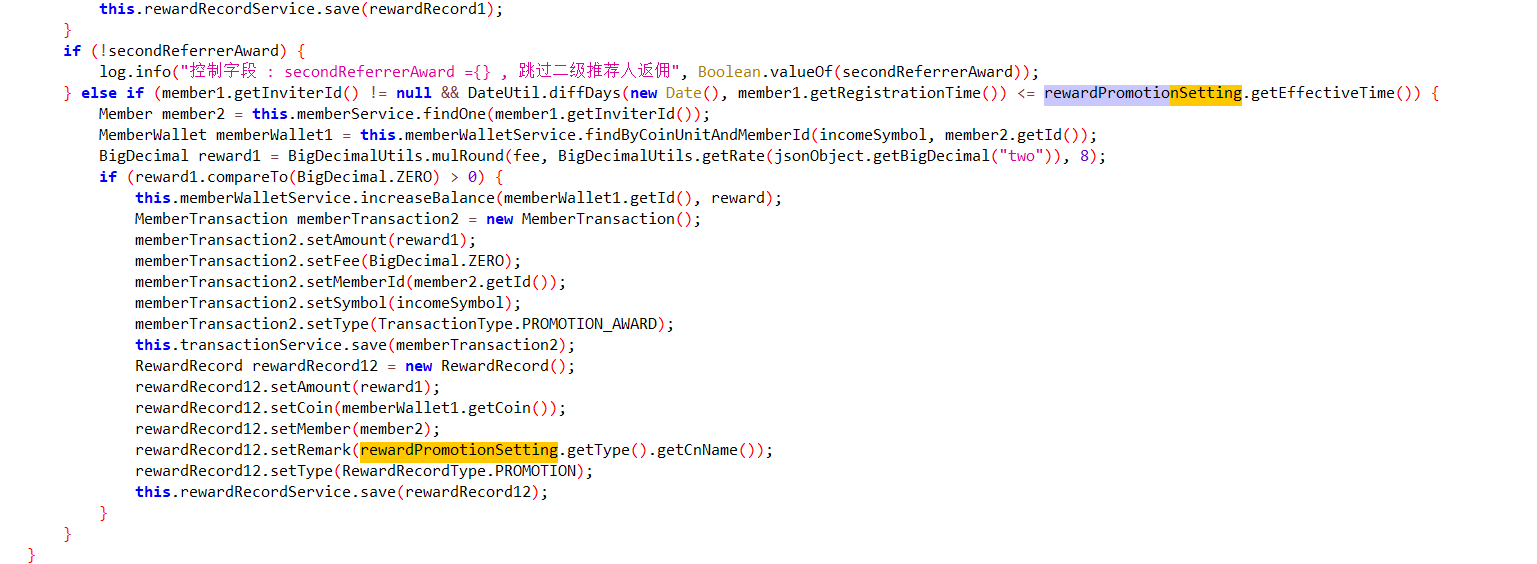
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 public void processOrder (ExchangeOrder order, ExchangeTrade trade, ExchangeCoin coin, boolean secondReferrerAward) { BigDecimal turnover; BigDecimal fee; BigDecimal incomeCoinAmount; BigDecimal outcomeCoinAmount; try { Long time = Long.valueOf(Calendar.getInstance().getTimeInMillis()); ExchangeOrderDetail orderDetail = new ExchangeOrderDetail (); orderDetail.setOrderId(order.getOrderId()); orderDetail.setTime(time.longValue()); orderDetail.setPrice(trade.getPrice()); orderDetail.setAmount(trade.getAmount()); if (order.getDirection() == ExchangeOrderDirection.BUY) { turnover = trade.getBuyTurnover(); } else { turnover = trade.getSellTurnover(); } orderDetail.setTurnover(turnover); if (order.getDirection() == ExchangeOrderDirection.BUY) { fee = trade.getAmount().multiply(coin.getFee()); } else { fee = turnover.multiply(coin.getFee()); } if (order.getMemberId().longValue() == 1 || order.getMemberId().longValue() == 10001 ) { fee = BigDecimal.ZERO; } orderDetail.setFee(fee); this .exchangeOrderDetailRepository.save(orderDetail); OrderDetailAggregation aggregation = new OrderDetailAggregation (); aggregation.setType(OrderTypeEnum.EXCHANGE); aggregation.setAmount(order.getAmount().doubleValue()); aggregation.setFee(orderDetail.getFee().doubleValue()); aggregation.setTime(orderDetail.getTime()); aggregation.setDirection(order.getDirection()); aggregation.setOrderId(order.getOrderId()); if (order.getDirection() == ExchangeOrderDirection.BUY) { aggregation.setUnit(order.getBaseSymbol()); } else { aggregation.setUnit(order.getCoinSymbol()); } Member member = this .memberService.findOne(order.getMemberId()); if (member != null ) { aggregation.setMemberId(member.getId()); aggregation.setUsername(member.getUsername()); aggregation.setRealName(member.getRealName()); } this .orderDetailAggregationRepository.save(aggregation); if (order.getDirection() == ExchangeOrderDirection.BUY) { incomeCoinAmount = trade.getAmount().subtract(fee); } else { incomeCoinAmount = turnover.subtract(fee); } String incomeSymbol = order.getDirection() == ExchangeOrderDirection.BUY ? order.getCoinSymbol() : order.getBaseSymbol(); MemberWallet incomeWallet = this .memberWalletService.findByCoinUnitAndMemberId(incomeSymbol, order.getMemberId()); this .memberWalletService.increaseBalance(incomeWallet.getId(), incomeCoinAmount); String outcomeSymbol = order.getDirection() == ExchangeOrderDirection.BUY ? order.getBaseSymbol() : order.getCoinSymbol(); if (order.getDirection() == ExchangeOrderDirection.BUY) { outcomeCoinAmount = turnover; } else { outcomeCoinAmount = trade.getAmount(); } MemberWallet outcomeWallet = this .memberWalletService.findByCoinUnitAndMemberId(outcomeSymbol, order.getMemberId()); this .memberWalletService.decreaseFrozen(outcomeWallet.getId(), outcomeCoinAmount); MemberTransaction transaction = new MemberTransaction (); transaction.setAmount(incomeCoinAmount); transaction.setSymbol(incomeSymbol); transaction.setAddress("" ); transaction.setMemberId(incomeWallet.getMemberId()); transaction.setType(TransactionType.EXCHANGE); transaction.setFee(fee); transaction.setDiscountFee("0" ); transaction.setRealFee(fee.toString()); this .transactionService.save(transaction); MemberTransaction transaction2 = new MemberTransaction (); transaction2.setAmount(outcomeCoinAmount.negate()); transaction2.setSymbol(outcomeSymbol); transaction2.setAddress("" ); transaction2.setMemberId(incomeWallet.getMemberId()); transaction2.setType(TransactionType.EXCHANGE); transaction2.setFee(BigDecimal.ZERO); transaction2.setRealFee("0" ); transaction2.setDiscountFee("0" ); this .transactionService.save(transaction2); try { if (order.getDirection() == ExchangeOrderDirection.SELL) { promoteReward(fee, member, incomeSymbol, secondReferrerAward); } } catch (Exception e) { e.printStackTrace(); log.error("发放币币交易推广手续费佣金出错" , e); } } catch (Exception e2) { log.info(">>>>>处理交易明细出错>>>>>>>>>{}" , e2); e2.printStackTrace(); } } public List<ExchangeOrderDetail> getAggregation (String orderId) { return this .exchangeOrderDetailService.findAllByOrderId(orderId); } public void promoteReward (BigDecimal fee, Member member, String incomeSymbol, boolean secondReferrerAward) { RewardPromotionSetting rewardPromotionSetting = this .rewardPromotionSettingService.findByType(PromotionRewardType.EXCHANGE_TRANSACTION); if (rewardPromotionSetting != null && member.getInviterId() != null && DateUtil.diffDays(new Date (), member.getRegistrationTime()) <= rewardPromotionSetting.getEffectiveTime()) { Member member1 = this .memberService.findOne(member.getInviterId()); MemberWallet memberWallet = this .memberWalletService.findByCoinUnitAndMemberId(incomeSymbol, member1.getId()); JSONObject jsonObject = JSONObject.parseObject(rewardPromotionSetting.getInfo()); BigDecimal reward = BigDecimalUtils.mulRound(fee, BigDecimalUtils.getRate(jsonObject.getBigDecimal("one" )), 8 ); if (reward.compareTo(BigDecimal.ZERO) > 0 ) { this .memberWalletService.increaseBalance(memberWallet.getId(), reward); MemberTransaction memberTransaction = new MemberTransaction (); memberTransaction.setAmount(reward); memberTransaction.setFee(BigDecimal.ZERO); memberTransaction.setMemberId(member1.getId()); memberTransaction.setSymbol(incomeSymbol); memberTransaction.setType(TransactionType.PROMOTION_AWARD); memberTransaction.setDiscountFee("0" ); memberTransaction.setRealFee("0" ); this .transactionService.save(memberTransaction); RewardRecord rewardRecord1 = new RewardRecord (); rewardRecord1.setAmount(reward); rewardRecord1.setCoin(memberWallet.getCoin()); rewardRecord1.setMember(member1); rewardRecord1.setRemark(rewardPromotionSetting.getType().getCnName()); rewardRecord1.setType(RewardRecordType.PROMOTION); this .rewardRecordService.save(rewardRecord1); } if (!secondReferrerAward) { log.info("控制字段 : secondReferrerAward ={} , 跳过二级推荐人返佣" , Boolean.valueOf(secondReferrerAward)); } else if (member1.getInviterId() != null && DateUtil.diffDays(new Date (), member1.getRegistrationTime()) <= rewardPromotionSetting.getEffectiveTime()) { Member member2 = this .memberService.findOne(member1.getInviterId()); MemberWallet memberWallet1 = this .memberWalletService.findByCoinUnitAndMemberId(incomeSymbol, member2.getId()); BigDecimal reward1 = BigDecimalUtils.mulRound(fee, BigDecimalUtils.getRate(jsonObject.getBigDecimal("two" )), 8 ); if (reward1.compareTo(BigDecimal.ZERO) > 0 ) { this .memberWalletService.increaseBalance(memberWallet1.getId(), reward); MemberTransaction memberTransaction2 = new MemberTransaction (); memberTransaction2.setAmount(reward1); memberTransaction2.setFee(BigDecimal.ZERO); memberTransaction2.setMemberId(member2.getId()); memberTransaction2.setSymbol(incomeSymbol); memberTransaction2.setType(TransactionType.PROMOTION_AWARD); this .transactionService.save(memberTransaction2); RewardRecord rewardRecord12 = new RewardRecord (); rewardRecord12.setAmount(reward1); rewardRecord12.setCoin(memberWallet1.getCoin()); rewardRecord12.setMember(member2); rewardRecord12.setRemark(rewardPromotionSetting.getType().getCnName()); rewardRecord12.setType(RewardRecordType.PROMOTION); this .rewardRecordService.save(rewardRecord12); } } } }
去数据库找
汇率为0.001
二级是0.1
因此5.2*0.001*0.01=0.000052
服务器取证-9 20 题目描述 请找到受害人“王涵”的手机号; (1.0分)
服务器取证-10 20 题目描述 请写出嫌疑人的违法交易网站的中文名称;(答案格式:2个汉字) (3.0分)
重构网站
1 find ./ -type f -exec sed -i 's/127.0.0.1/10.172.29.100/g' {} +
服务器取证-11 20 题目描述 请写出数据库中Recharge表的status字段中,0代表的中文含义; (1.0分)
服务器取证-12 20 题目描述 平台中所有账户中ETH余额最多的地址是多少?(答案格式:0x123F…) (6.0分)
1 0x928f5963c03340077a8d2375657fb3395fe4a790
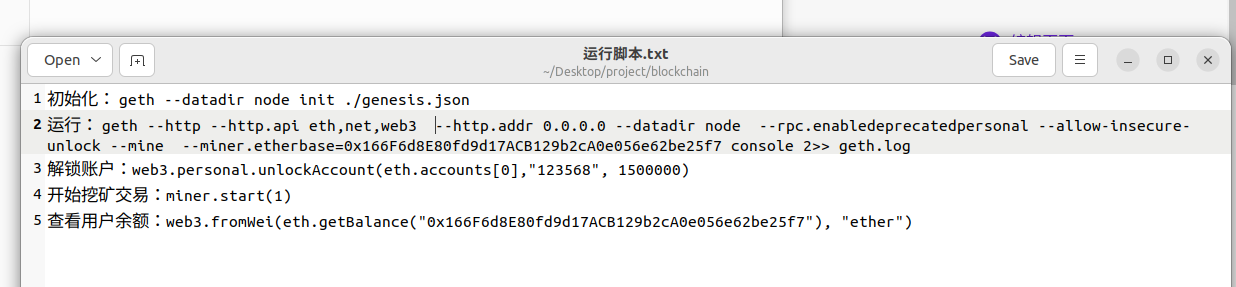
使用geth并且给了查询语句
ai写一个即可
1 var accounts = eth.accounts; var _max = 0; var _max_address = ''; for(var account of accounts){ var balance = eth.getBalance(account); if(balance > _max){ _max = balance; _max_address = account; }}; [web3.fromWei(_max, "ether"), _max_address]
服务器取证-13 20 题目描述 区块链搭建工具是?(答案格式:abcd) (1.0分)
同上
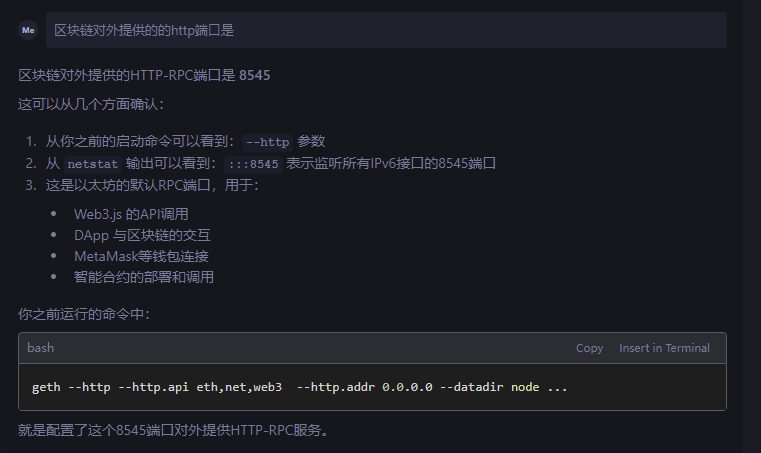
服务器取证-14 20 题目描述 区块链对外提供的的http端口是? (2.0分)
服务器取证-15 20 题目描述 服务器网站数据库使用的字符集为?(答案格式:如有字母,请小写) (1.0分)
服务器取证-16 20 题目描述 由于服务器定时清理了交易数据,请找寻整个区块链中最大的交易金额(答案格式:0x123F…) (6.0分)
1 0xbb218c4bd443824260673a92b575f6c249085b6e482d89f1445fdb4ba487b9f2
1 var max = web3.toBigNumber (0 ); var maxTx; for (var i = 0 ; i <= eth.blockNumber ; i++) { var b = eth.getBlock (i, true ); if (b && b.transactions ) { b.transactions .forEach (function (tx ) { if (tx.value > max) { max = tx.value ; maxTx = tx; } }); } }; web3.fromWei (max, "ether" )
服务器取证-17 20 题目描述 请写出嫌疑人在chrome上使用的钱包名称;(答案格式:如有字母全小写) (2.0分)
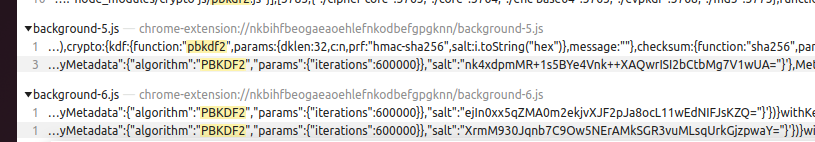
服务器取证-18 20 题目描述 请写出chrome钱包插件使用的pbkdf2加密算法的轮次;(答案格式:纯数字) (4.0分)
根据报错打断点调试也可以
服务器取证-19 20 题目描述 Chrome钱包密码的算法中对iv的加密方式是什么?(答案格式:如有字母请小写,如md5) (4.0分)
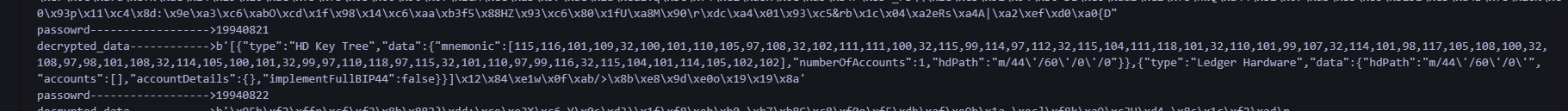
题目描述 已知服务器中嫌疑人的钱包登录密码为八位纯数字生日1994****,请写出该密码; (6.0分)
1 2 3 4 5 6 7 8 9 10 data : "4OBSCQ3fpgiiQG1CUT2KVKU9Sma1ixgcZ1xBb+XeQXlX9yFbyj6HgpPH4vKktB39FPVD5wlV0fFrKkrB4YvkwS4y0P2y15GrSMvJ7ZPV2FdT+o7/s9ydryf4j/dvWssWhlpIf8+Z/GTWxrd0pEKCumJ0SgM7pNCn+LPufqgAAc8Phk1V2G78YFFn27hoPalU+mfyLirBvbcNCe7PZhUEf02OB9HJxc6NL8VGHZ0mugf8CMCU4CfoMWBjGB358XwYgqVCAYfPeP612BcqH/2qGsf4v5MUynaoWjR3CDxg6z5n/SzvayET9KxzpnP5/YwrI1Kr6KSuX8hfWa4G7Qect7gRcJ5OSP9vjDAE0Oa7+2RoOvSuDhONrit9JD1j3PlF/HLHjCWcAxFPAqQHnaXHUT7+O/UR/nHBBUjwZqXcA3NvY6Up9gEyp7v252JKw/ybv9PYsNVBNNzaOCHM+2vLu4AEdhsJjEmzz1BMnl2a10lX3PIxT6g+eVdHNVOkeESS7Xiufrh1BNEXemU+/Mj8zOzC8X3sC+h7k6V+j8FO5gFFIsGVsehmhjQ0g3hv5OjHLu+8UbJ19HVC6nzyopbHF1EbgVc4bEfnsqxpBQT4xGY27MQLFa2SlcpRpue1NpZWdhV2C8/wTSBmcgnm3PHWgvBiuA==" iv : "oi49chysOL0hAXfqbviWIA==" salt : "fhlH2383hn7sqEKiLN8zSqv/F/v9x0s3xj/1zBI1zkA="
gpt写脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 from base64 import b64decodefrom Crypto.Protocol.KDF import PBKDF2from Crypto.Cipher import AESfrom Crypto.Hash import SHA256data = "4OBSCQ3fpgiiQG1CUT2KVKU9Sma1ixgcZ1xBb+XeQXlX9yFbyj6HgpPH4vKktB39FPVD5wlV0fFrKkrB4YvkwS4y0P2y15GrSMvJ7ZPV2FdT+o7/s9ydryf4j/dvWssWhlpIf8+Z/GTWxrd0pEKCumJ0SgM7pNCn+LPufqgAAc8Phk1V2G78YFFn27hoPalU+mfyLirBvbcNCe7PZhUEf02OB9HJxc6NL8VGHZ0mugf8CMCU4CfoMWBjGB358XwYgqVCAYfPeP612BcqH/2qGsf4v5MUynaoWjR3CDxg6z5n/SzvayET9KxzpnP5/YwrI1Kr6KSuX8hfWa4G7Qect7gRcJ5OSP9vjDAE0Oa7+2RoOvSuDhONrit9JD1j3PlF/HLHjCWcAxFPAqQHnaXHUT7+O/UR/nHBBUjwZqXcA3NvY6Up9gEyp7v252JKw/ybv9PYsNVBNNzaOCHM+2vLu4AEdhsJjEmzz1BMnl2a10lX3PIxT6g+eVdHNVOkeESS7Xiufrh1BNEXemU+/Mj8zOzC8X3sC+h7k6V+j8FO5gFFIsGVsehmhjQ0g3hv5OjHLu+8UbJ19HVC6nzyopbHF1EbgVc4bEfnsqxpBQT4xGY27MQLFa2SlcpRpue1NpZWdhV2C8/wTSBmcgnm3PHWgvBiuA==" salt = "fhlH2383hn7sqEKiLN8zSqv/F/v9x0s3xj/1zBI1zkA=" iv = "oi49chysOL0hAXfqbviWIA==" iteration = 600000 for month in range (1 , 13 ): for day in range (1 , 32 ): password = f"1994{month:02} {day:02} " key = PBKDF2(password, b64decode(salt), dkLen=32 , count=iteration, hmac_hash_module=SHA256) cipher = AES.new(key, AES.MODE_GCM, nonce=b64decode(iv)) decrypted_data = cipher.decrypt(b64decode(data)) print (f"decrypted_data {decrypted_data} " ) print (f"passowrd {password} " )
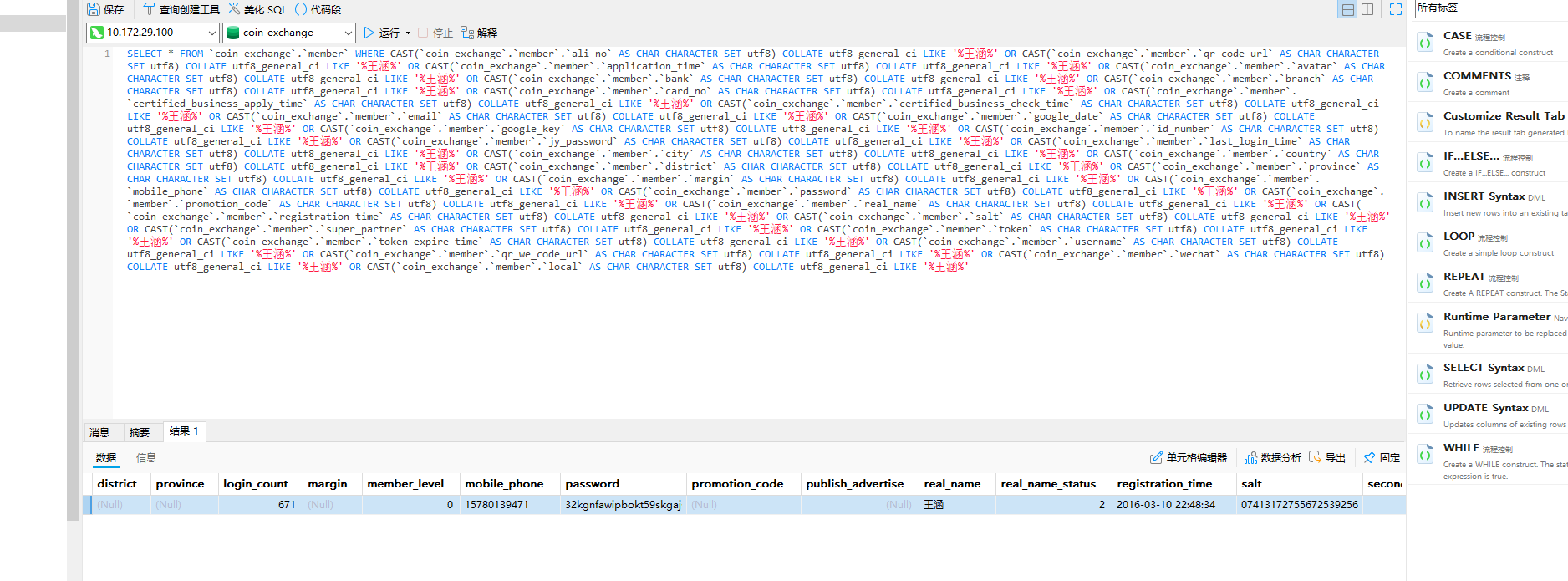
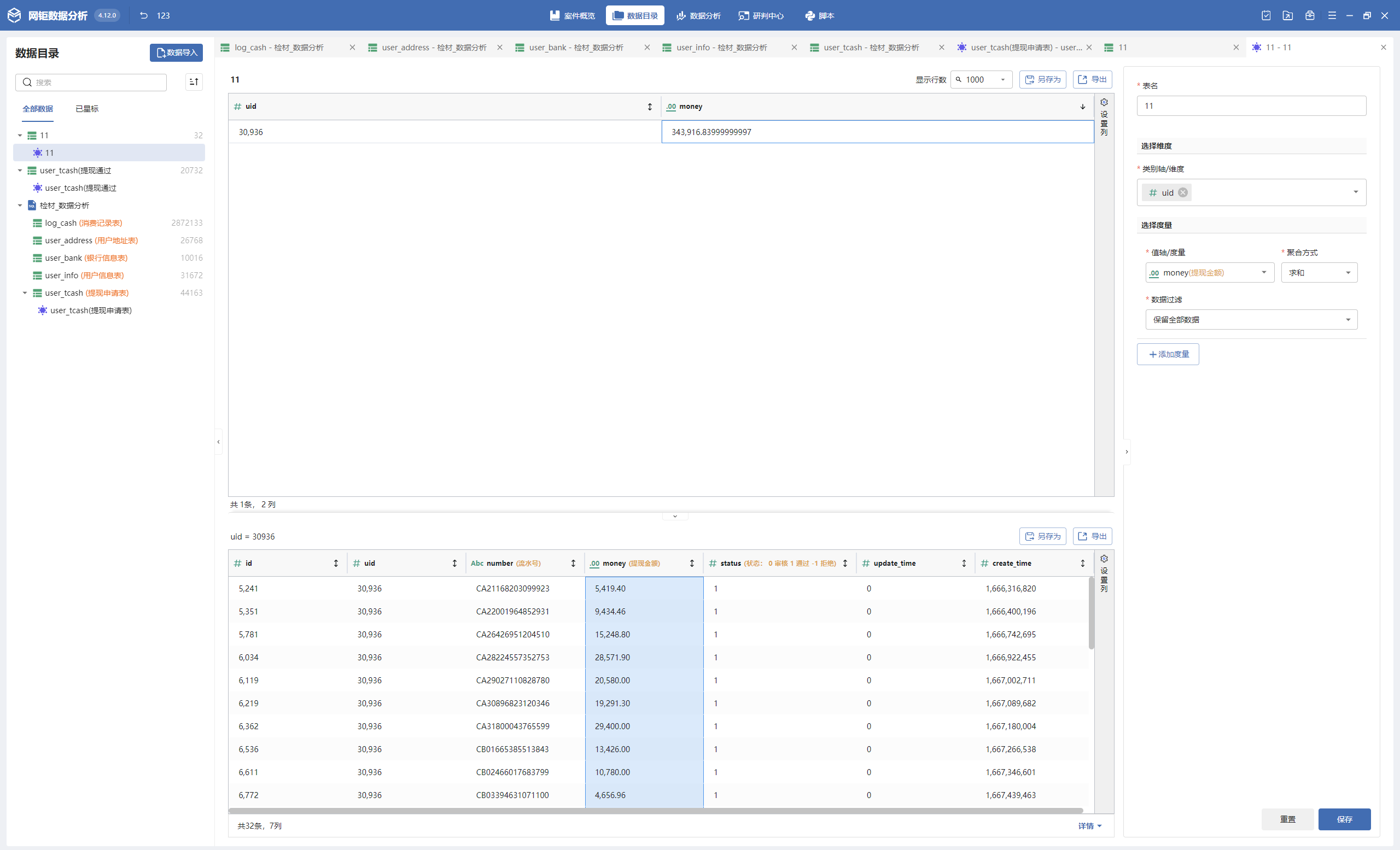
数据分析 数据分析-1 20 题目描述 分析数据库检材,请分别计算该数据库中每个用户审核通过的提现总金额,写出审核通过的提现总金额最大值; (2.0分)
先对status=1筛选后聚合
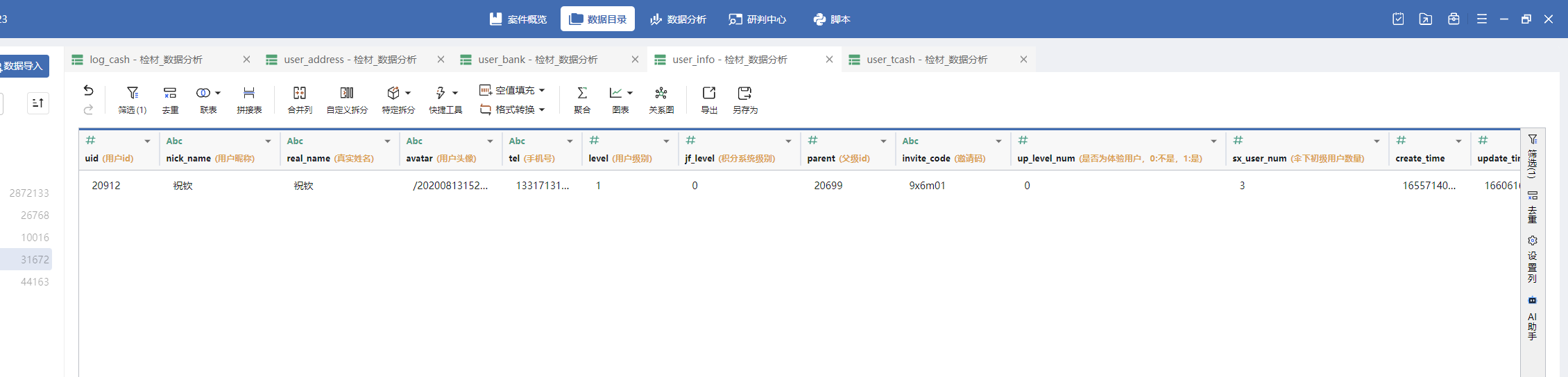
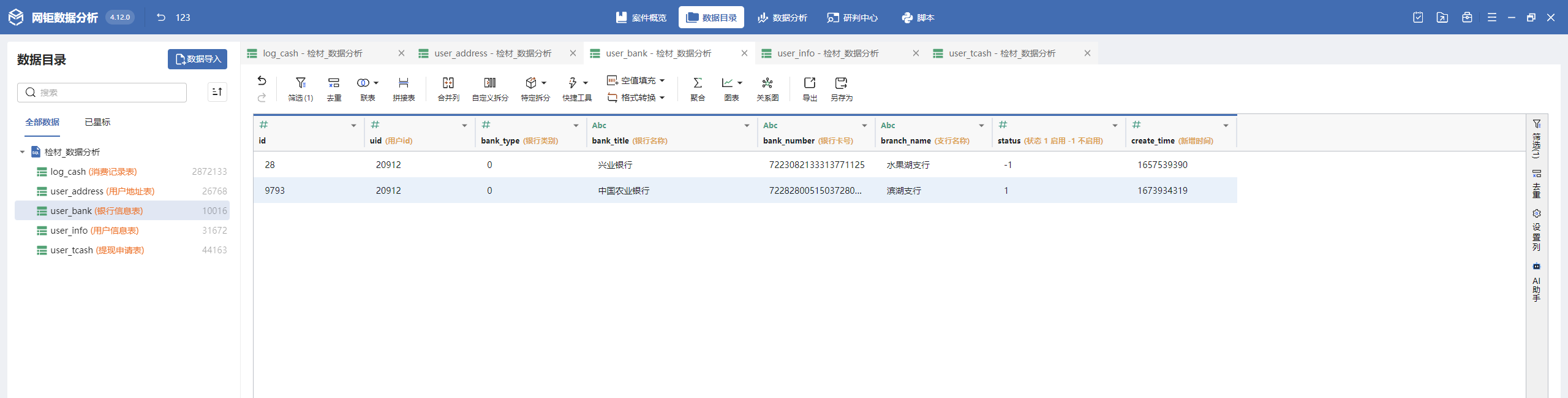
数据分析-2 20 题目描述 数据库中用户真实名称为“祝钦”的有效银行卡号是多少; (2.0分)
根据姓名得到uid 根据uid找有效银行卡号
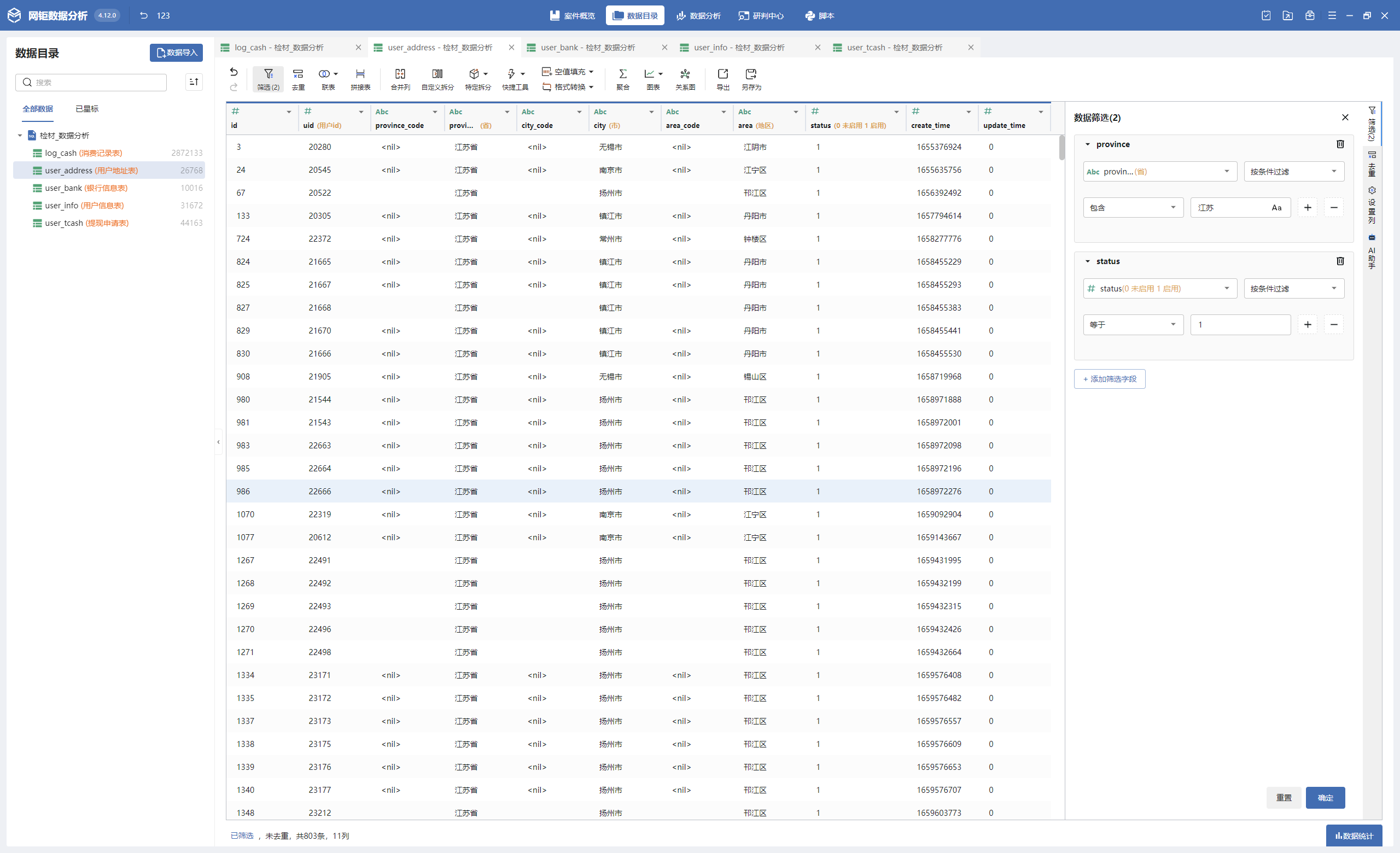
数据分析-3 20 题目描述 请计算数据库中地址在江苏省的启用用户数量; (2.0分)
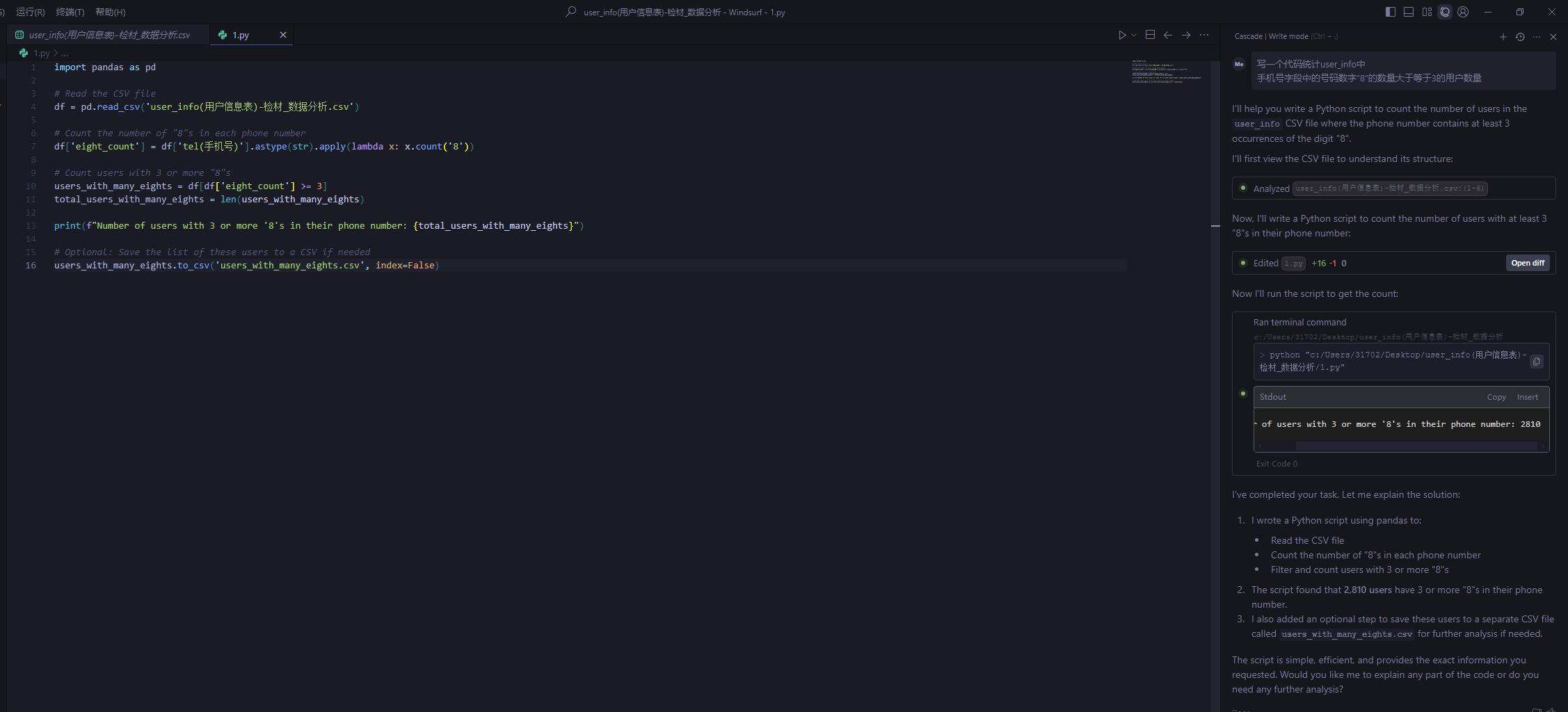
数据分析-4 20 题目描述 请计算手机号字段中的号码数字“8”的数量大于等于3的用户数量; (4.0分)
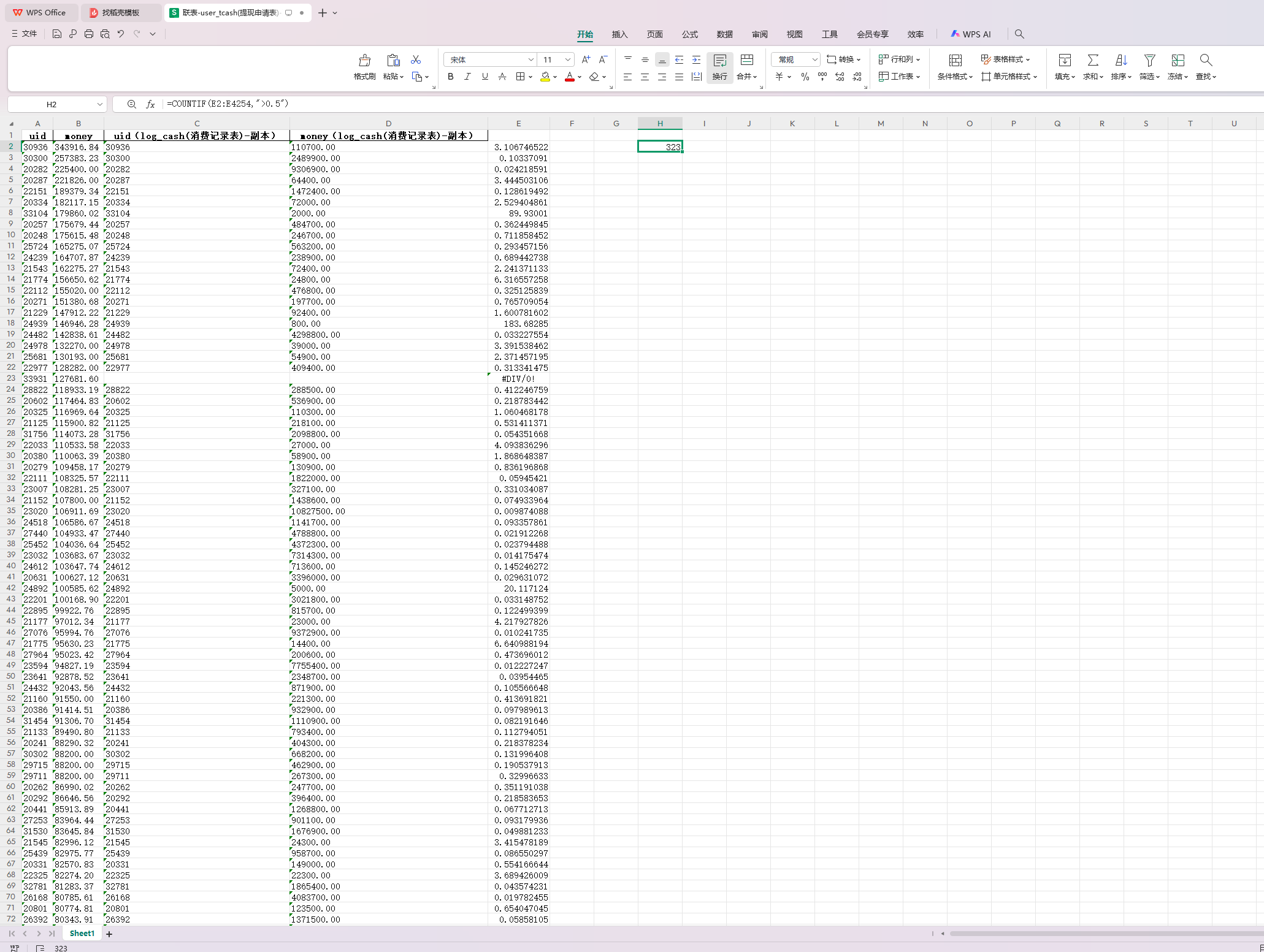
数据分析-5 20 题目描述 计算每个用户审核通过的总提现金额与其总消费金额的比值,该比值大于等于0.5的用户数量是多少? (4.0分)
导出后使用=COUNTIF(E2:E4254,”>0.5”)
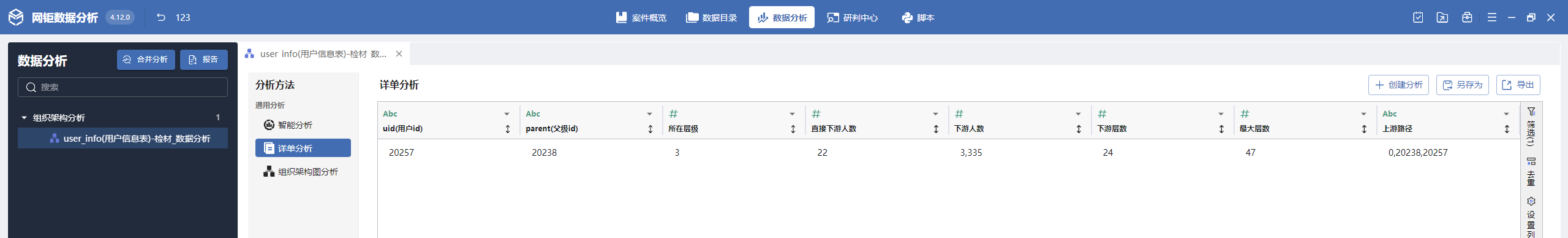
数据分析-6 20 题目描述 计算uid为“20257”的用户的下线最大层级数是多少(自己为第1层,若用户A是自己的直接下线,那么此时用户A所在层级=2); (4.0分)
导入组织架构,手动匹配一下